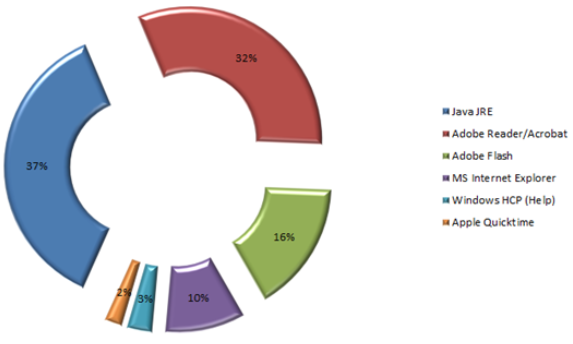
37 percent of users browsing the Web with insecure Java versions
Over a period of three months, researchers from CSIS have monitored 50 different exploit kits on 44 unique servers, and found out that 31.3 % were infected with the virus/malware due to missing security updates.
In particular, users were running outdated versions of specific applications and browser plugins. Java JRE accounted for 37 percent of the most vulnerable applications, followed by Adobe Reader/Acrobat with 32 percent and Adobe Flash with 16 percent.
Common vulnerabilities exploited by cybercriminals in their web malware exploitation kits include:
CVE-2010-1885 Microsoft Help & Support HCP CVE-2010-1423 Java Deployment Toolkit insufficient argument validation CVE-2010-0886 Java Unspecified vulnerability in the Java Deployment Toolkit component in Oracle Java SE CVE-2010-0842 Java JRE MixerSequencer Invalid Array Index Remote Code Execution Vulnerability CVE-2010-0840 Java trusted Methods Chaining Remote Code Execution Vulnerability CVE-2009-1671 Java buffer overflows in the Deployment Toolkit ActiveX control in deploytk.dll CVE-2009-0927 Adobe Reader Collab GetIcon CVE-2008-2992 Adobe Reader util.printf CVE-2008-0655 Adobe Reader CollectEmailInfo CVE-2006-0003 IE MDAC CVE-2006-4704 Microsoft Visual Studio 2005 WMI Object Broker Remote Code Execution Vulnerability CVE-2004-0549 ShowModalDialog method and modifying the location to execute code
Go through related posts:
- 56 percent of enterprise users using vulnerable Adobe Reader plugins
- Kaspersky: 12 different vulnerabilities detected on every PC
Verify your Java version here, ensure that all of your plugins and software applications are up to date in order to mitigate the risks posed by the existence of web malware exploitation kits.