Bank of Melbourne Twitter account hacked, spreading phishing links
The Twitter account of Bank of Melbourne was compromised last Wednesday, and was used to spread phishing links as direct messages to the account followers, according to reports coming in from affected users.
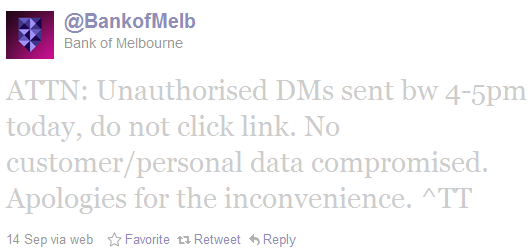
In a tweet, the bank said that:
ATTN: Unauthorised DMs sent bw 4-5pm today, do not click link. No customer/personal data compromised. Apologies for the inconvenience. ^TT
Followed by another one, once the incident was resolved:
Thanks for all your support. We take security very seriously & will be strengthening our policies to further protect our social channels ^TT
It's worth discussing how Bank of Melbourne got is social channel hacked in the first place. Moreover, what contributed to the ease of obtaining the login credentials for their Twitter account?
For starters, it would have been highly impractical to brute force the password for their Twitter account, no matter the fact that the CAPTCHA-solving process could be outsourced to vendors offering CAPTCHA-solving services to assist in brute forcing attacks.
Judging by the fact that the malicious attackers didn't just spread a prank or hacktivist message using the stolen credentials, it is highly likely that the attacker has a relatively advanced understanding of how the cybercrime ecosystem works. By spamvertising the phishing link using direct messages as an evasive element of the campaign, the attacker is attempting to take advantage of the trust factor established by the nature of direct messages.
Was Bank of Melbourne a victim of phishing attack, is there any chance that a malware-infected host within their network was successfully data mined for stolen Twitter credentials.
What do you think?
Talkback.