Brute force RDP attacks depend on your mistakes

Kaspersky Lab has added generic protection for an attack form they say is on the rise: brute force RDP attacks.
RDP stands for Remote Desktop Protocol and is the protocol for Windows Remote Desktop and Terminal Server. It is sometimes used for remote user access to servers, but very commonly used for remote administrator access. RDP "remotes" the Windows UI, allowing a remote user with an RDP client to log into Windows and use it as if local.
A brute force RDP attack would scan IP ranges and TCP port ranges (the default being 3389) for RDP servers, which could be either client or server systems. Once an attacker finds an RDP server, he would attempt to log on, particularly as Administrator. The IDS in Kaspersky products will now detect this type of attack as Bruteforce.Generic.RDP.
As Kaspersky says, a successful RDP attack against a server has the potential to be quite lucrative. But even as they call it a "brute force" attack, the Kaspersky account overstates its sophistication. Very simple and obvious actions on your part can prevent this attack from having any success:
- Use complex passwords, especially for accounts with administrator access
- Consider disabling the Administrator account and using a different account name for that access
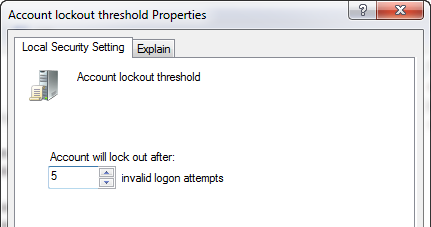
- Set the system to lock a user out for a period of time after some number of failed login attempts. Numerous group policies for these rules have been in Windows for a long time
- Require two-factor authentication, especially for administrator access
These guidelines are best practice for many reasons, not just to block brute force attacks, but they are good general advice against brute for attacks, not just those for RDP. As the Kaspersky story says, last year there was a major brute force campaign of this type against Wordpress accounts. It was so intense that it was effectively a DDOS. Good password and account lockout policies can't stop a DDOS, but they can stop a brute force login attack.