China on WannaCry: It wasn't us, honest

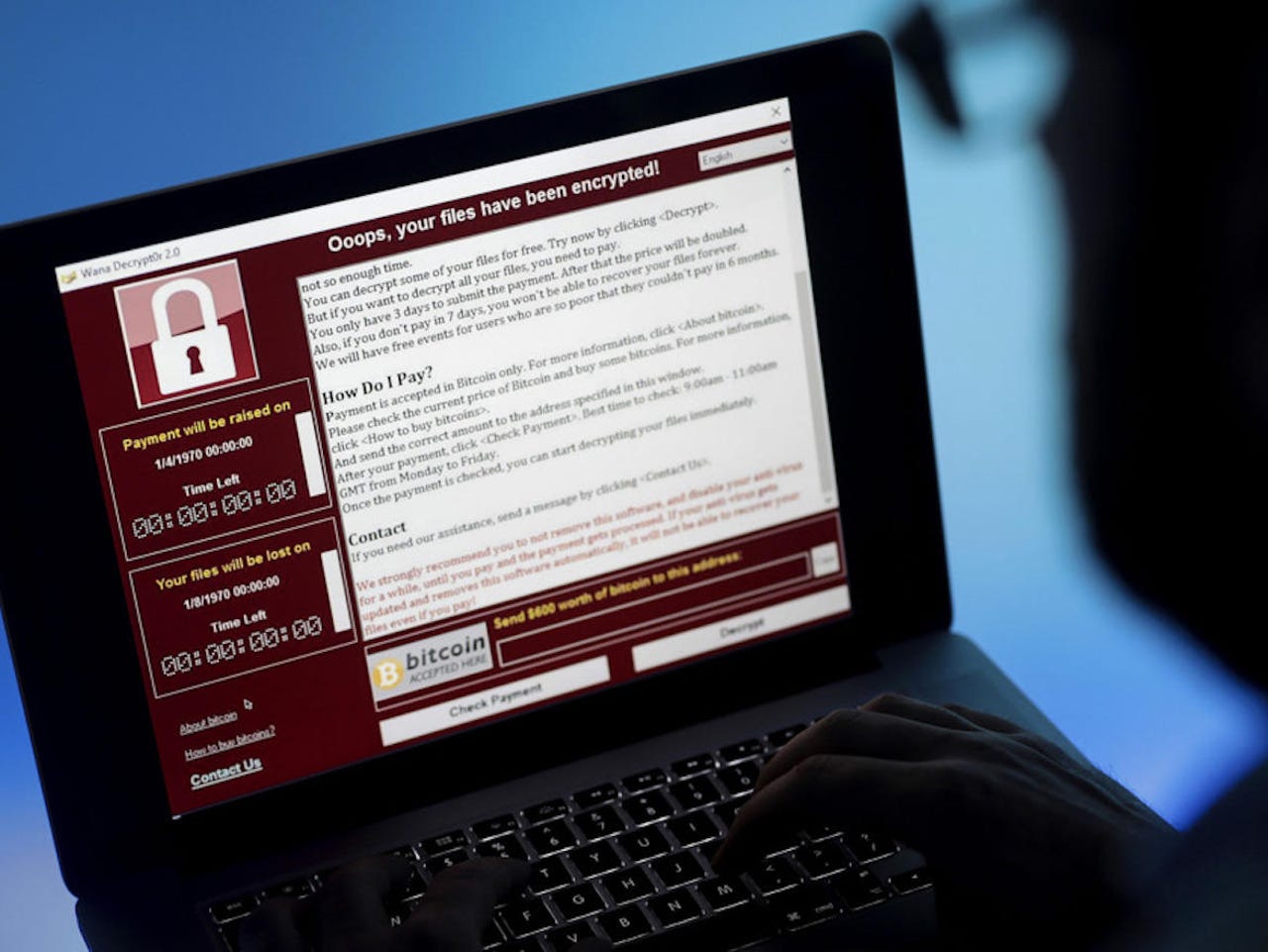
WannaCry caused chaos across the globe.
Chinese security firms have hit out against suggestions that last month's global WannaCry ransomware outbreak can be blamed on China.
The WannaCry ransomware epidemic hit over 300,000 PCs around the globe, using worm-like capabilities to spread and infect Microsoft Windows machines -- including many in China. While nobody has uncovered evidence to specifically identify the perpetrators, there are several theories as who might be behind the attack.
One hypothesis, offered by researchers Flashpoint following linguistic analysis of the WannaCry ransom note, is that it's the work of a native or highly fluent Chinese speaker who used machine translation to convert the original note into other languages.
But Chinese security firm Qihoo 360 has dismissed the claims and questioned the attempt to attribute the attacks by analysing the ransom note text.
"The correct and professional way is to trace the ransomware through the traits of the code," said Zheng Wenbin, chief security engineer at Qihoo 360, speaking to Chinese state-run media Xinhua.
"Hackers often add characters from different languages into their code to confuse the public and hide their identity," Zheng added. Flashpoint's researchers didn't dismiss this in their report, and acknowledged that misdirection on behalf of the attackers could be in play.
Li Bosong, deputy chief engineer at another Chinese security firm, Antiy Labs, also criticised claims that China is behind WannaCry, dismissing reports as lacking 'substantial evidence' and claiming that cybersecurity researchers -- be they Chinese or otherwise -- will 'easily' see the 'falsity' of the claims that it emerged from China.
Lazarus redux?
Meanwhile, some security firms have linked the cyberattack to the notorious Lazarus Group, a hacking operation connected to a number of high-profile cyberattacks in recent years, including the $80m Bangladeshi cyber bank heist.
Researchers at Symantec have tentatively cited similarities between code used in Lazarus campaigns and the code behind WannaCry, potentially pointing to the two sharing an author. Lazarus is suspected of working on behalf of North Korea, although there are suggestions that the group operates out of China.
However, China was one of the countries hit hardest by the attack, with with 29,000 organisations in total falling victim to the ransomware -- including Chinese government bodies for transport, industry, social security and immigration.
While WannaCry caused chaos across the globe, the ransomware hasn't been particularly lucrative for its creators: almost a month on from the outbreak, the ransomware has banked just under $150,000.
The figure represents a poor return for such a widespread campaign, especially when you consider how the value of the Bitcoin wallets are on the rise due to a recent surge in the cryptocurrency's valuation.
READ MORE ON WANNACRY
- Why was the WannaCry ransomware attack so widespread?
- Ransomware: An executive guide to one of the biggest menaces on the web
- Windows XP hit by WannaCry ransomware? This tool could decrypt your infected files
- How to defend yourself against the WannaCrypt global ransomware attack
- Ransomware: WannaCry was basic, next time could be much worse