China: Unstoppable threat dragon of Asia

SINGAPORE--The Asia-Pacific region's fastest growing economy is also the region's worst in terms of cyber threats.
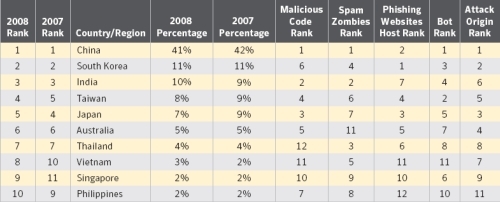
According to the latest annual Symantec's Asia-Pacific and Japan (APJ) Internet Security Threat Report, China was ranked No. 1 for malicious activity within the region in 2008, accounting for 41 percent of all such activity. China's new ranking mirrored that of the last report, where it also topped the region with a 42 percent share of all malicious activity in 2007.
Globally, the United States was the top-ranked country for malicious activity, said the security vendor. The United States, at 28 percent, was also found to be the top country from which attacks targeting the APJ region originated. Another 15 percent of such attacks originated from China, while 11 percent came from South Korea.
Malicious activity by country, Asia-Pacific and Japan (Source: Symantec)
As for Web attacks against the APJ region, China was the top country of origin within the region with a share of 79 percent. Worldwide, China was No. 2 for Web-based attacks, with 13 percent of the global total. The report noted that the number of compromised Web sites relating to the Beijing 2008 Olympic Games contributed to the country's high ranking.
In 2008, the world's most populous nation was tops in APJ for spam output. It was also second in the number of phishing sites hosted, after South Korea.
China again dominated on the botnet front, emerging as the top country for bot command-and-control servers in the region with a share of 63 percent. Symantec reported it identified 3,567 distinct new bot masters within APJ last year.
During the same period, the number of distinct bot-infected computers decreased year-on-year to just over 2 million, representing 22 percent of all zombie machines identified globally. An average of 11,683 active infected computers were detected daily in the APJ region in 2008, a 3 percent increase from the 11,329 recorded in 2007.
China had the highest bot infections last year, but its share fell from 66 percent in 2007 to 58 percent. The outbreak of the Downadup worm, or more popularly known as Conficker, may have to a certain extent, reinforced China's first-place ranking, said the report. Conficker infections, Symantec pointed out, were found to be largely prevalent in Asia, with the largest concentrations found in the Greater China region. As the threat is still ongoing, the security firm expects 2009 statistics to be impacted as well.
Avinash Lotke, Symantec's systems engineering manager for the Asia-Pacific region, told ZDNet Asia in a phone interview Tuesday, that there were several factors for China's rankings. An important factor was that China overtook the United States in 2008 as the country with the most number of broadband subscribers. "Even if the bandwidth is not that great, [PCs are] always on and available for malicious guys to attack," he noted.
In addition, there are also comparatively more illegal cafes and shared resources for Internet browsing in China. Even with a government crackdown on such avenues prior to Beijing 2008, they are "still quite prevalent", said Lotke.
Focus on consumers, but enterprises should be wary
Compared to previous years where the focus was on the corporate realm, attackers seemed to place greater emphasis on compromising consumer information in 2008, according to Lotke.
"Most large enterprises have some form of security in place to monitor [for suspicious activity], and have dedicated teams to look at their security posture," he pointed out. "The more vulnerable group is the consumers--their systems may not be patched, or they may not have the right security tools."
However, Lotke warned that enterprises should not let their guard down, as without proper diligence it would just be "a matter of time" before their systems are compromised.