Chrome 80 update cripples top cybercrime marketplace

A small change in the Google Chrome 80 browser has had a devastating effect on one of today's top cybercrime marketplaces.
According to new research shared with ZDNet this week by threat intelligence firm KELA, the Genesis Store is currently going through a rough patch, seeing a 35% drop in the number of hacked credentials sold on the site.
KELA says Genesis administrators are scrambling to fix their inventory deficit and feed the store with new credentials before customers notice a drop in new and fresh listings.
If they don't address the issues caused by the new Chrome 80 update, the store's entire future hangs in the balance.
What is Genesis?
The Genesis Store is a unique entity and a pioneer on the cybercrime landscape.
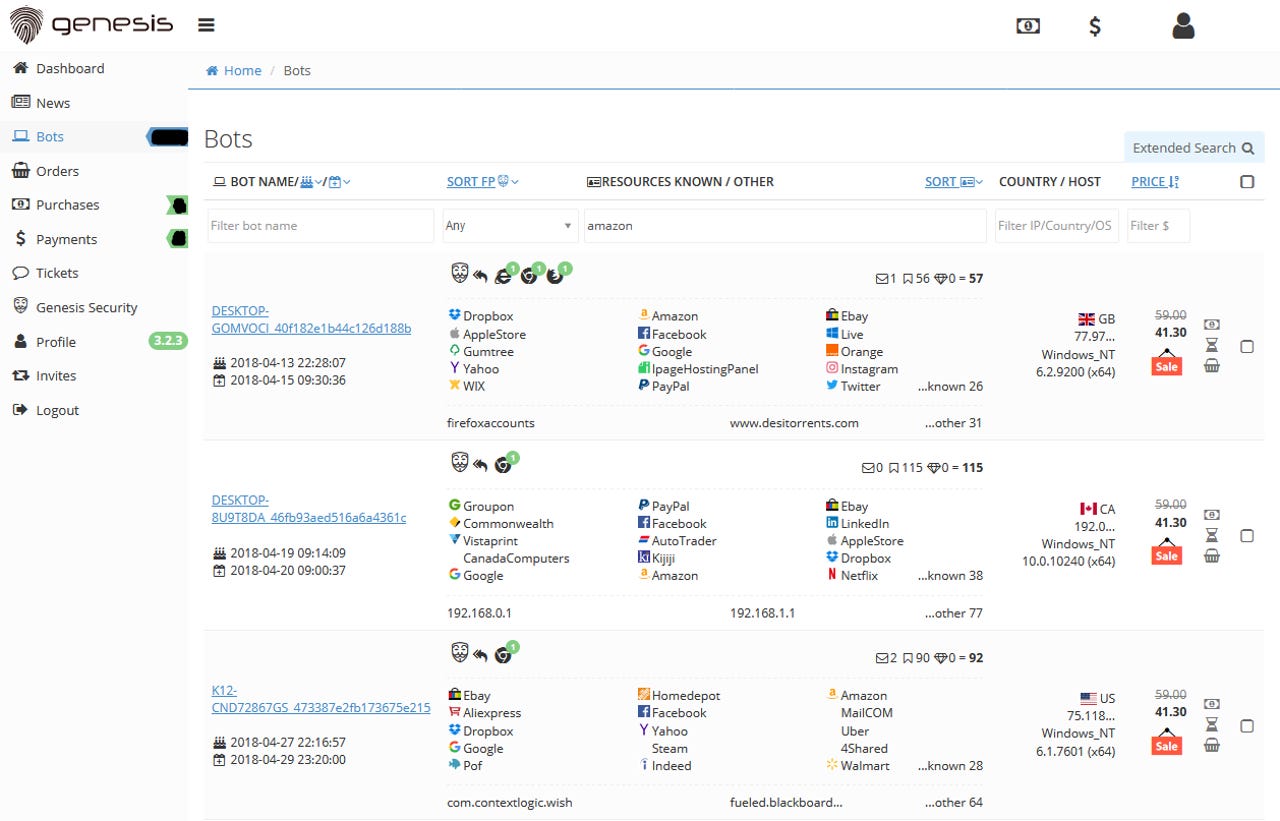
Launched in November 2018, the Genesis Store sells stolen browser credentials. However, unlike most of its competitors, the site doesn't merely sell access to a stolen username and password. Instead, the site sells so-called "fingerprints."
These fingerprints are a virtual image of a user's identity on an online website.
Also: Protect yourself: How to choose the right two-factor authenticator app
Fingerprints include basic details about a user's account, such as username and password, but also more detailed things, such as past IP addresses the user has used, browser cookies, user-agent strings, and other OS technical details.
Genesis customers can buy anything from fingerprints for Facebook and other social media accounts to fingerprints for intranets at some of the world's largest companies.
After buying a fingerprint from the Genesis Store, Genesis customers are provided with a Chrome extension that they can use to apply the stolen "fingerprint" to their browser and fully and entirely impersonate a user.
Because these fingerprints are extremely detailed and include extra information besides just a username and passwords, hackers are often able to access even accounts protected by some forms of two-factor authentication (2FA) solutions.
The ability to bypass 2FA has made Genesis one of the go-to places in the cybercrime landscape for buying access to hacked accounts.
The site's rise in popularity has also had an effect on its inventory, with Genesis growing from a tiny store selling access to 60,000 fingerprints in March 2019, to a mammoth portal peddling nearly 335,000 fingerprints at the end of the year.
Currently, the store plays a major role in many cybercrime operations, with many hacker groups often buying stolen fingerprints from Genesis to power their cybercrime sprees.
Most Genesis fingerprints come from AZORult infections
However, the site's internal operations have remained a mystery ever since Kaspersky experts first exposed its existence in March 2019.
Over the past few months, KELA product manager Raveed Laeb has put significant efforts into studying the Genesis Store beyond the initial Kaspersky report, in order to understand how the site operates.
One of the avenues of research Laeb looked into was the source of all the stolen fingerprints. While some security researchers suspected the site's fingerprints were being collected through malware installed on infected workstations, they didn't know what malware was responsible for all the data sold on the site.
To figure this out, Laeb told ZDNet in a phone call this week that he scraped the entire Genesis Store for all stolen fingerprints and then proceeded to classify each entry based on the GUID (generic user identifier) that's listed next to each fingerprint.
In research published last week, Laeb says he discovered that 90% of all the stolen fingerprints listed on Genesis had a format of 8-8-8-8-8 (eight alpha-numerical characters in five successive blocks), suggesting they came from one single malware strain.
After further research, Laeb said he was able to track this GUID to the format assigned to victims infected by the AZORult info-stealing malware -- which makes a lot of sense since AZORult was one of the most active and widespread malware strains used in 2019 and would be capable of fueling a site of Genesis' size.
While Laeb suspects that there are multiple malware gangs who operate distinct AZORult malware botnets and then provide stolen fingerprints to Genesis administrators, it is pretty clear to an external observer that AZORult is Genesis' primary weak point.
For example, if something would happen to the AZORult malware, the entire supply chain for the Genesis Store would be put in danger, with almost no alternatives for Genesis admins.
Chrome 80 update cripples Genesis operations
And this is exactly what happened in early February 2020, when Google released Chrome 80.
With Chrome 80, Google switched to using the AES-256 algorithm to hash passwords stored locally inside Chrome's internal SQLite database.
This switch to AES-256 has resulted in Chrome-saved passwords having a different format than they had before. Albeit tiny inside Chrome's huge codebase, this small change has crippled AZORult's ability to extract passwords from Chrome browsers.
In a phone call this week, Laeb told ZDNet that this Chrome update had an immediate and tremendous impact on Genesis operations.
While last year Genesis was seeing a steady influx of 18,000 new stolen fingerprints being added to the site on a daily basis, this number has now gone down 30 times to roughly 600 new entries.
Without a steady input of new fingerprints, the store's database has also started to slowly shrink in size, going down from its max of 335,000 stolen credentials to roughly 200,000-230,000, the volume listed in recent weeks, after the Chrome 80 update.
AZORult's second death
Laeb told ZDNet that things aren't looking good for the site unless they make a full switch to another malware strain and replace AZORult.
He cites replacing AZORult because development on the AZORult malware strain stopped at the end of 2018 when the malware's author called it quits.
While AZORult cracked versions are still being sold or exchanged online, the malware's source code is not available anymore. This means criminal gangs relying on AZORult can't update the malware to counteract the changes introduced in Chrome 80.
As Laeb noted in his research, we're effectively seeing AZORult's second death, after the one in late 2018. Furthermore, this one seems to be permanent.
However, while Chrome 80 killed AZORult, other malware strains have had no problem in updating their codebases, with the developer of the Raccoon infostealer providing an update within days after Chrome 80's release.
Other malware strains are expected to follow suit, and even Google's security team doesn't expect this change to be more than a nuisance for most malware authors.
"We aim to improve the security of Chrome with every release," a Google spokesperson told ZDNet in an email yesterday.
"With [Chrome] 80, we made changes that allow us to isolate Chrome's network stack into its own robustly sandboxed process. As part of those changes, we hardened the algorithm for encrypted passwords/cookies and changed the storage mechanisms, which disrupted the tooling that data thieves currently rely on," Google said.
"These changes are not a permanent defense against such attacks, and as such, we strongly recommend the use of robust multi-factor authentication, particularly Chrome's native U2F key support," Google said.
Genesis testing an AZORult replacement
However, for Genesis administrators, a bigger issue remains the store's dwindling supply of new fingerprints.
Laeb told ZDNet that in recent days, the Genesis admins appear to have stopped adding new AZORult-based fingerprints altogether, and are now consistently adding new fingerprints that have been stolen with the help of a yet-to-be-determined malware strain.
However, the new entries are still nowhere near the levels seen last year in AZORult's heyday, and the store's supply chain problem remains an issue.
But, to be fair, we fully expect Genesis to survive AZORult's "second death."
This is because the people who were operating AZORult botnets will also eventually figure out that the malware is no longer effective against recent versions of Chrome, and will most likely switch to a new malware strain as well.
Once they do, these suppliers are expected to rekindle their business partnerships with Genesis and provide the store with new fingerprints. If the number of stolen fingerprints will return to last year's levels remains to be seen.
Anyway, Genesis' impact is a long-lasting one on the cybercrime landscape, and other similar services have also popped up in the meantime, such as RichLogs. If Genesis can't adapt to AZORult's second death, fingerprints will still be available in other places.
The Genesis store that sells "digital browser fingerprints" now has a competitor.
— Catalin Cimpanu (@campuscodi) June 1, 2019
A new site called RichLogs launched in April and provides similar services. It sells browsers fingerprints so hackers can hijack victims accounts without triggering account fraud alerts pic.twitter.com/2JQLgl4QG3