Cisco WebEx Chrome extension allowed arbitrary code execution: Project Zero

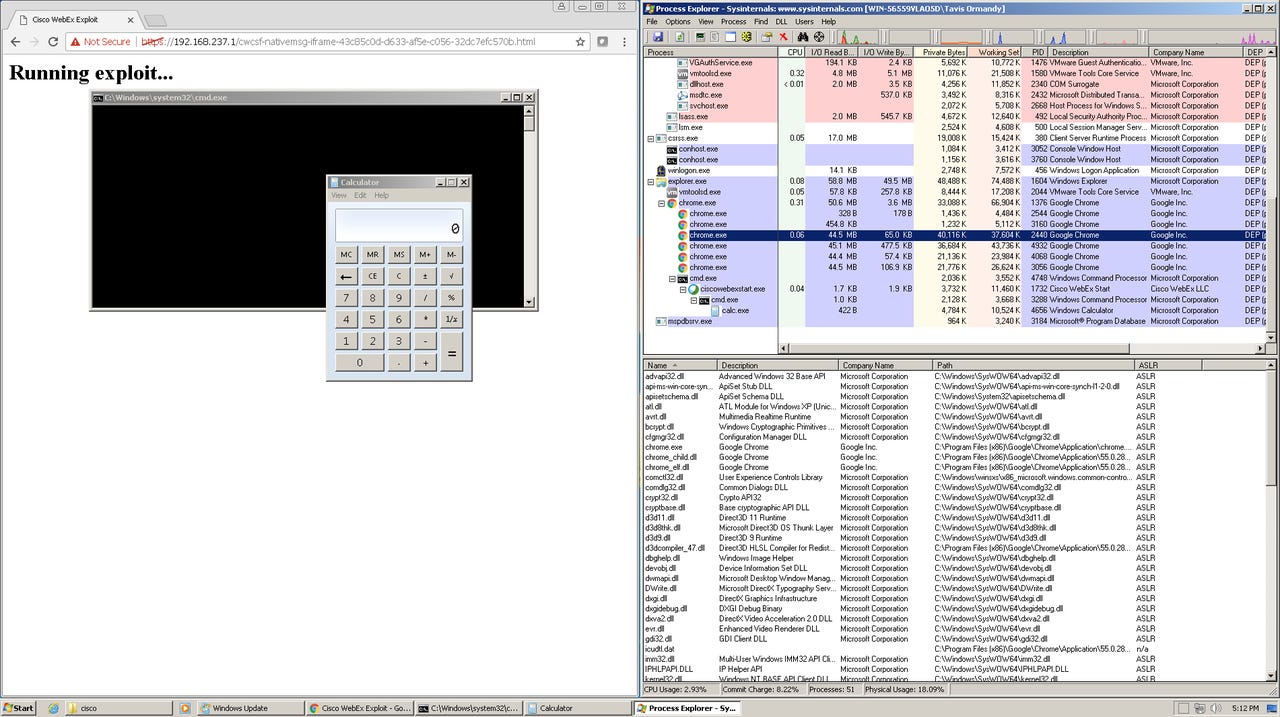
Cisco has closed a remote code execution vulnerability in its WebEx extension for Chrome, after Project Zero's Tavis Ormandy alerted the networking giant to the issue on Saturday.
According to Ormandy, the extension worked on any URL that matched against a magic pattern, and since it could be used in a non-visible iframe, the user need not be aware the extension was engaged.
"The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!)," the security researcher wrote in the Project Zero issue tracker.
Security
After noticing Cisco shipped a copy of Microsoft's C runtime, Ormandy was able to make system calls and run remote code.
In response, Ormandy said Cisco initially blocked new installations of the extension, before limiting the pattern matching to webex.com domain.
"This means that if a site is not *.webex.com or *.webex.com.cn, then the user must click OK for code execution to happen," Ormandy said.
"I think we will consider this issue fixed now. Hopefully, webex.com is well maintained and not full of XSS."
The patched version of the WebEx Chrome extension is currently being rolled out.
Filippo Valsorda of Cloudflare recommends users install the WebEx extension in a dedicated Chrome profile to protect a user's main profile from attack.
Last week, the Google Project Zero researcher found a cross-site scripting (XSS) bug in an auto-installed Chrome extension bundled with Abode Acrobat Reader on Windows.
Earlier this month, Ormandy called out Kaspersky for simplistically storing certificates that left users open to TLS certificate collisions, thanks to the Russian security company only storing the first 32 bits of an MD5 hash in the SSL proxy packaged with its Anti-Virus product.
"You don't have to be a cryptographer to understand a 32-bit key is not enough to prevent brute-forcing a collision in seconds," Ormandy said.
Google began Project Zero in 2014 in an effort to reduce the number impacted by zero-day attacks.