Critical WinRAR vulnerability places 500 million users at risk

Featured
An unpatched, critical remote code execution flaw within WinRAR's SFX archive features has been disclosed by a researcher.
WinRAR, available for Windows users, is an unzipping tool able to decompress .ZIP, .RAR and .7Z files, among others.
However, a security flaw which reportedly allows for remote code execution has been discovered in WinRAR SFX version 5.21.
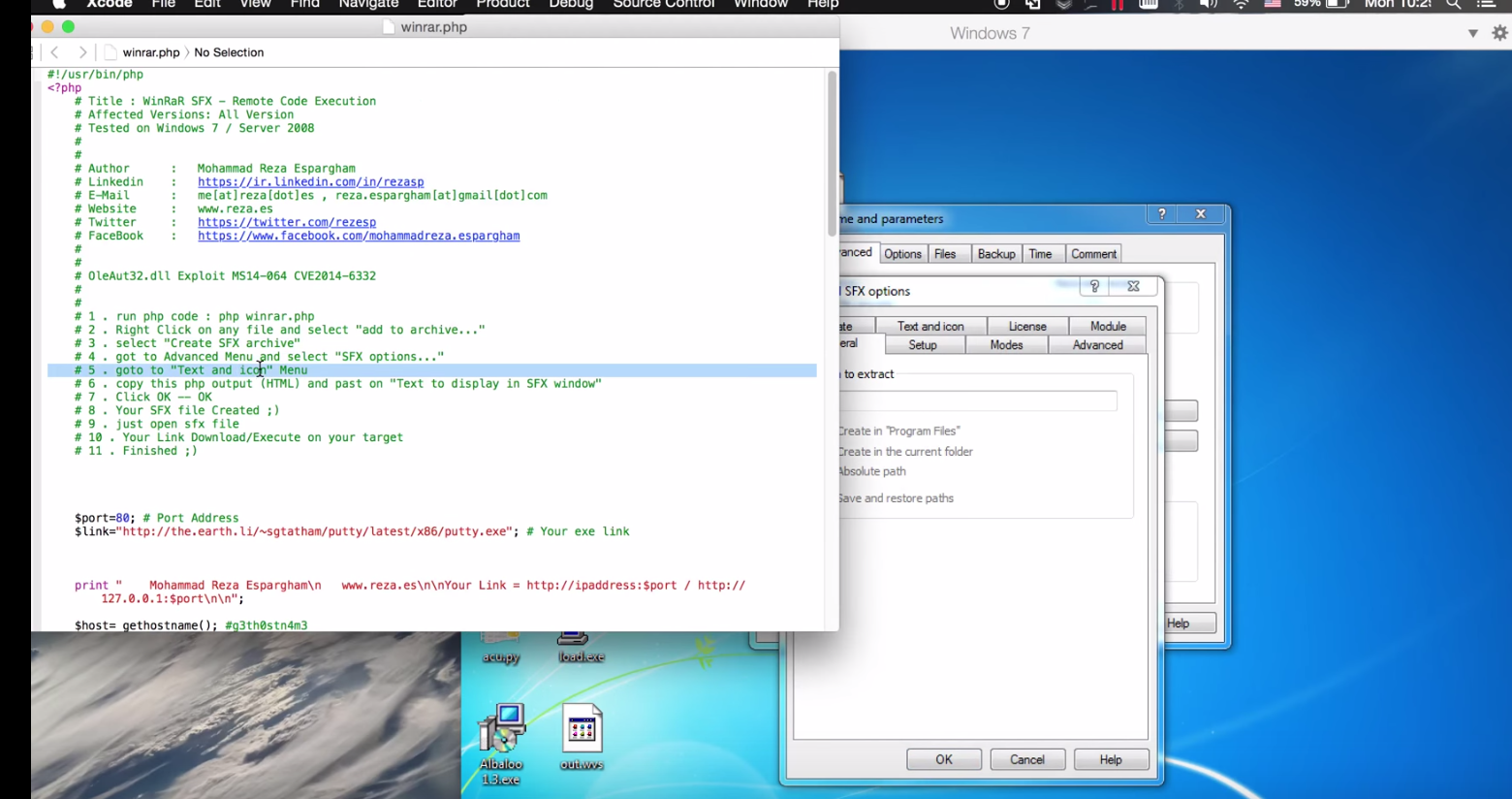
Iranian researcher Mohammad Reza Espargham posted his findings on Full Disclosure. Granted a CVSS score of 7.4, the vulnerability could allow hackers to remotely execute system code and compromise victim machines, leading to control, surveillance and potentially data theft. A CVE score is yet to be issued.
According to Espargham, the flaw is located in the text and icon function of the "Text to display in SFX window" module. Attackers can generate compressed archives with malicious payloads embedded within, complete with specific commands designed to compromise a PC through Perl code.
"Thus results in a system specific code execution when a target user or system is processing to open the compressed archive," the researcher says.
The vulnerability is deemed critical as the exploit requires low user interaction -- merely the opening of a file -- without reference to user account privileges.
Espargham included a proof-of-concept exploit, and the researcher believes it affects all versions of WinRAR. Such a critical but easy to utilize exploit is a gift for cyberattackers, who likely would use such a vulnerability in phishing campaigns.
Malwarebytes researcher Pieter Arntz said in a blog post the proof-of-concept code needs some "trivial" changes to work, but is ultimately sound.
WinRar's team refutes the flaw discovery, telling ZDNet that as SFX archives can run contained executable files -- and is required by installers -- any SFX archive is potentially dangerous for users. WinRAR said in a statement:
"We can say that limiting SFX module HTML functionality would hurt only those legitimate users, who need all HTML features, making absolutely no problem for a malicious person, who can use previous version SFX modules, custom modules built from UnRAR source code, their own code or archived executables for their purpose. We can only remind users once again to run .exe files, either SFX archives or not, only if they are received from a trustworthy source."
Safari browser extensions you never knew you needed
Read on: Top picks
- How to access Wi-Fi anonymously from miles away
- Flic: The wireless button which brings the connected world into your home (hands-on)
- Adblock Plus Google Play exile ends, launches iOS, Android browser
- One password gifts hacker with hundreds of Firefox bugs, vulnerabilities
- Fiat Chrysler recalls 8,000 extra Jeeps over remote control hacking worries