Did this ransomware threat drop away because cybercrooks went on holiday?

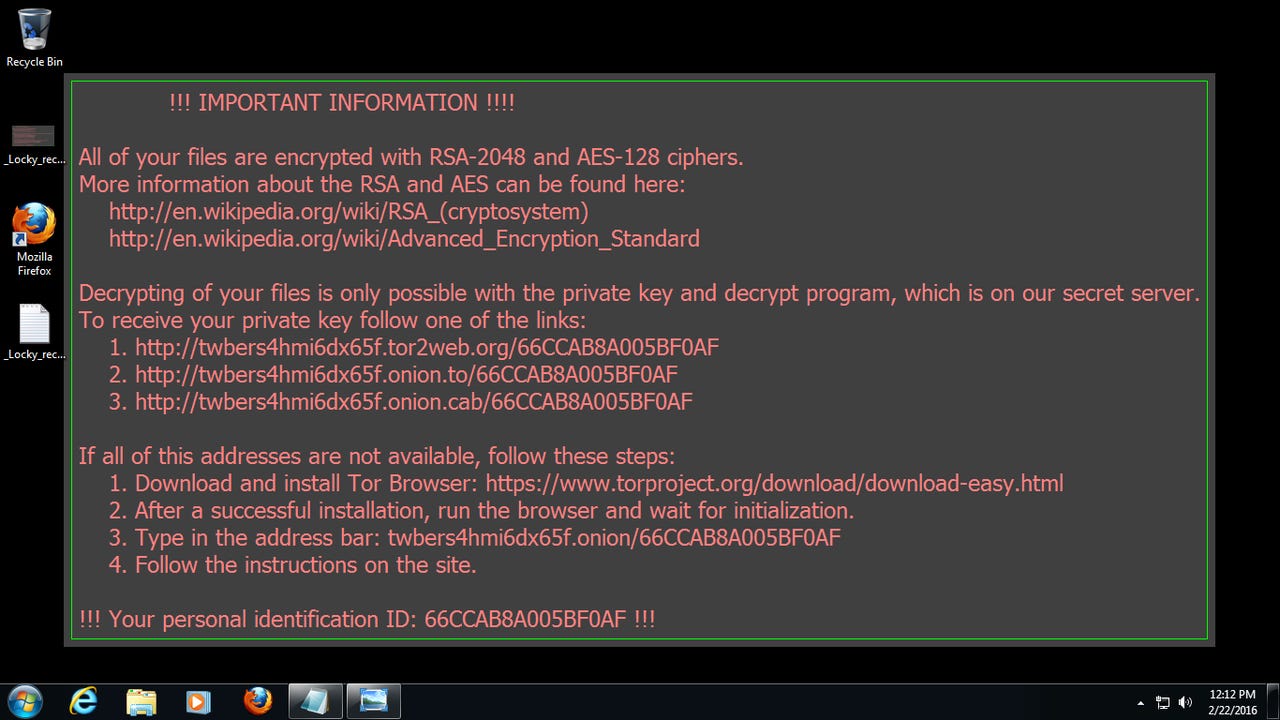
Locky attacks dropped significantly during December -- but don't expect this to be the end of it.
As cybercriminal groups have become ever more organised and professional, some are beginning to operate as if they were legitimate businesses -- to such an extent that those behind one of the most notorious forms of ransomware appear to close for business over Christmas, leaving their malicious work behind over the festive period.
Ransomware boomed during 2016, with Locky becoming by far the most notorious variant of the file-encrypting, ransom-demanding malicious software. In the past year Locky took a Hollywood Hospital offline until it paid a $17,000 ransom and even became the second most common malware threat by November.
Perhaps it was because the ransomware was so successful that those behind the cybercriminal scheme seemingly took Christmas off. According to the latest Global Threat Index by cybersecurity researchers at Check Point Software, there was an 81 percent drop in the average number of Locky infections during December.
Nathan Shuchami, head of threat prevention at Check Point, said: "The massive decrease in Locky attacks during December is part of a wider trend which saw malware attacks decrease by around eight percent compared to the previous months.
"The most likely cause genuinely is that cybercriminals have opted to take a Christmas holiday too -- perhaps to spend some of the fruits of their labours. Ransomware remains a threat that businesses need to take seriously into 2017."
The 81 percent drop in Locky infections during December is ten times more than the average drop for other types of malware, which is 8 percent and close to the 9 percent average decline in malware attacks in December 2015.
Instances of Locky dropped by so much that the ransomware even fell out of the top ten ranking of most prevalent malware families for the first time since June.
The Conficker worm, despite being over eight years old, held its position as the most prevalent malware during December. It accounted for ten percent of all malware attacks during the 30-day period, down from 15 percent during November.
Replacing Locky as the second most common form of malware and accounting for five percent of known attacks was Nemucod. It's a JavaScript or Visual Basic Script downloader most commonly used to download variants of ransomware and other malicious payloads.
Slammer, a memory resident worm targeting Microsoft SQL 2000 and causing denial-of-service attacks against victims, was the third most common malware attack in December, accounting for four percent of attacks.
In total, the top ten malware variants accounted for 42 percent of all known attacks during December, with familiar names such as Cryptowall ransomware and Sality, a virus which allows remote operations and downloads of additional malware to infected systems, in the mix.
Check Point's Global Threat Index also details the most significant malware threats to businesses via mobile devices, with the HummingBad Android malware once again representing the most common cybercriminal threat to smartphones and tablets.
Second on the mobile threat list was Triada, a backdoor for Android which grants super-user privileges to downloaded malware and spoofs URLs. Third was by Ztorg, a Trojan which downloads and installs applications on the phone without the user's knowledge.
But while malicious cyberattacks dropped during December, they're likely to rise once again as cybercriminals get back to work.
January has already seen a variety of new malware variants in the wild, including the data-stealing Merry Christmas ransomware and a phishing scam which targets financial institutions and uses Visual Basic Script to install keylogging malware.
Read more on cybercrime
- This ransomware targets HR departments with fake job applications
- How Bitcoin helped fuel an explosion in ransomware attacks
- How to tell if your Android phone has the HummingBad malware [CNET]
- Ransomware: The smart person's guide [TechRepublic]
- Ransomware-as-a-service allows wannabe hackers to cash-in on cyber extortion