Does Twitter's malware link filter really work?
Whenever a Twitter user is attempting to post a link to a known malware/phishing URL, a "Oops! Your tweet contained a URL to a known malware site!" message will appear, and prevent this from happening.
Does the feature really work? A five minute test showed disappointing results, making it obvious that it's still in experimental mode.
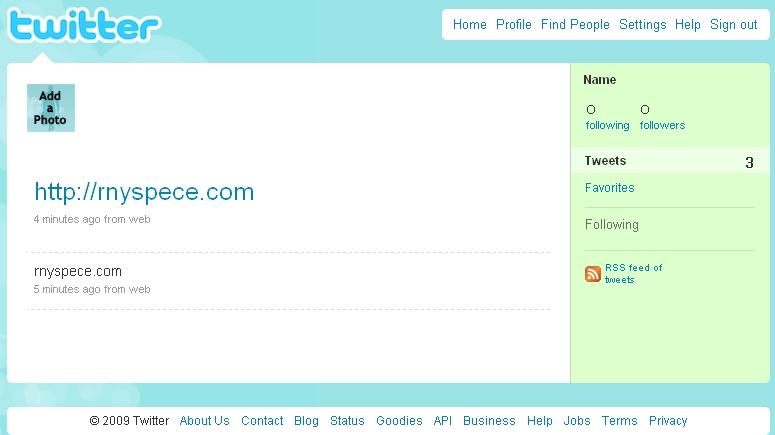
The MySpace phishing page used in the initial test www.rnyspece (dot)com indeed triggered the filter, however, tweeting it without the www or even worse with http://did not trigger the filter as you can see in the attached screenshot. The malware link filter also doesn't appear to be relying on Stopbadware's database of known malicious sites, since I was successfully able to tweet several sites listed as badware without a problem.
- Go through related posts: Commercial Twitter spamming tool hits the market; Cybercriminals hijack Twitter trending topics to serve malware; French hacker gains access to Twitter's admin panel; Spammers harvesting emails from Twitter - in real time; Twitter hit by multiple variants of XSS worm; Koobface worm joins the Twittersphere
Despite that Twitter's own malware filter is clearly still in development, it's an indication that Twitter is finally moving from reactive (blocking Twitter users tweeting malware links once the campaign starts) to proactive (preventing the campaign from ever happening that is only if the cybercriminals are using known malware domains) security practices. The integration of Stopbadware and related databases of known malware domains would not prevent the abuse of Twitter in the long term - cybercriminals in fact maintain blacklisting notifications for their sites. However, not taking advantage of the 381,815 already marked as unsafe sites is clearly a missed opportunity.
It's only a matter of time until they launch another campaign. The question is - can Twitter handle it?