DoS vulnerability hits Google's Chrome, crashes with all tabs
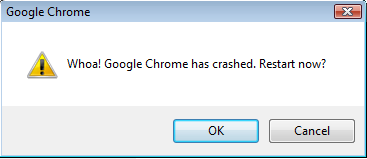
"An issue exists in how chrome behaves with undefined-handlers in chrome.dll version 0.2.149.27. A crash can result without user interaction. When a user is made to visit a malicious link, which has an undefined handler followed by a 'special' character, the chrome crashes with a Google Chrome message window "Whoa! Google Chrome has crashed. Restart now?". It crashes on "int 3" at 0x01002FF3 as an exception/trap, followed by "POP EBP" instruction when pointed out by the EIP register at 0x01002FF4."
Nothing's impossible the impossible just takes a little longer.
Also see: Google Chrome vulnerable to carpet-bombing flaw
Whenever a new product is in its introduction stage, it would logically attract a lot of attention from security researchers trying to a make a point that it's vulnerable, and that some of the vulnerabilities are pretty trivial. For instance, yesterday David Maynor from Errata Security pin pointed possibilities for exploitation in Google's Chrome, saying that :
"Google just released Chrome, their own web browser. We decided to run it through Looking Glass and it doesn't look half bad. They at least have ASLR enabled on a few of their libraries, no NX though. Chrome is not as bad as some apps I have seen but that is not saying much."
What's important though, is whether or not the browser release would also start attracting the attention of cybercriminals.
Would the level of exploitability change? In the fist quarter of 2009, Google would presumably release stats of the number of people who downloaded Chrome, demonstrating nothing else but the introduction stage of their browser. The question is, how many of those who downloaded it would actually stick with it, and would companies embrace it if it does gets popular enough, potentially increasing the exploitability level of any upcoming vulnerabilities?
Considering the fact that according to public statistics of usage share of web browsers, IE6 users are just as many as IE7 ones, converting from Firefox or IE to Google's Chrome is not going to happen overnight.