Exploit code released for unpatched IE 7 vulnerability

Another day, another gaping hole affecting fully patched versions of Microsoft's Internet Explorer browser.
According to a warning from US-CERT, proof-of-concept exploit code has been published for a new zero-day bug that can be used for a variety of malicious attacks against Windows users running IE 6, IE 7, and IE 8 beta 1.
The code, published here by 'sirdarckat', shows how the vulnerability can be exploited to hijack an iFrame in a legitimate site and capture a target's keystrokes. This occurs because Internet Explorer fails to properly restrict access to a document's frames, allowing an attacker to modify the contents of frames in a different domain.
[ SEE: Zero-day flaw haunts Internet Explorer ]
This screenshot (of a proof-of-concept created by researcher Aviv Raff) shows the Google home page in a frame hijacked from Microsoft's Windows Update site. The security implications are rather frightening: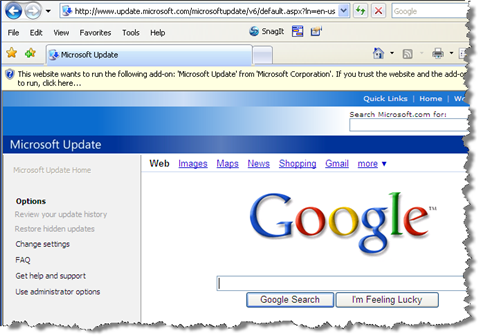
Can you imagine if someone spoofs this page with their own rigged Microsoft Update download page?
From the US-CERT advisory:
Microsoft Internet Explorer fails to properly restrict access to a document's frames. This can allow an attacker to replace the contents of a web page's frame with arbitrary content. Internet Explorer still appears to enforce the cross-domain security model, which limits the actions that a malicious frame can take with the parent document. For example, a frame that exists in a different domain should not be able to access the parent document's cookies or HTML content, or other domain-specific DOM components. However, components that are not tied to a specific domain, such as the onmousedown event. By monitoring this particular event, an IFRAME can capture keystrokes from the parent document. Other actions may be possible.
...By convincing a user to view a specially crafted HTML document (e.g., a web page or an HTML email message), an attacker may be able to access non-domain-specific elements from a web page that exists in a different domain. For example, the attacker may be able to capture keystrokes while a user is interacting with a web page in a different domain.
[ ALSO SEE: Internet Explorer ‘feature’ causing drive-by malware attacks ]