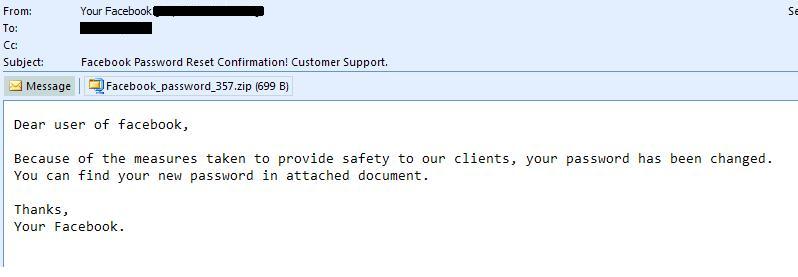
Facebook password reset themed malware campaign in the wild
Facebook is warning its users on an ongoing BredoLab malware serving campaign using the well known "Facebook Password Reset Confirmation Customer Support" social engineering theme.
More details on the campaign:
Subject: Facebook Password Reset Confirmation Customer Support Message: "Dear user of Facebook,Because of the measures taken to provide safety to our clients, your password has been changed. You can find your new password in attached document. Thanks, Your Facebook."
Asked to comment on the inner workings of the campaign, TrendMicro's Ivan Macalintal commented that based on the samples he analyzed, the same campaign was also seen in October, 2009.
“What is troubling is the newer versions of the BredoLab used in this latest attack campaign are not being detected by the majority of anti-virus services — and that means the majority of users who unwittingly click on the bogus attachments linked to fake e-mails are going to have their computers infected".
The Zeus crimeware and Bredolab connection
In a recently published paper "ZeuS: A Persistent Criminal Enterprise" TrendMicro further details the connections between Zeus and BredoLab:
- According to our research, BREDOLAB and ZeuS are individual tools that are freely available in the cybercriminal underground. Their uses complement each other, which is why we very often see them together.ZeuS specializes in stealing information from infected systems. BREDOLAB, on the other hand, is a software that enables cybercriminal organizations to deliver any kind of software to its victims. Once a user’s machine is infected by BREDOLAB, it will receive regular malware updates the same way it receives software updates from the user’s security vendor.
Campaign outbreak graph courtesy of Commtouch.