Fake Antivirus XP pops-up at Cleveland.com
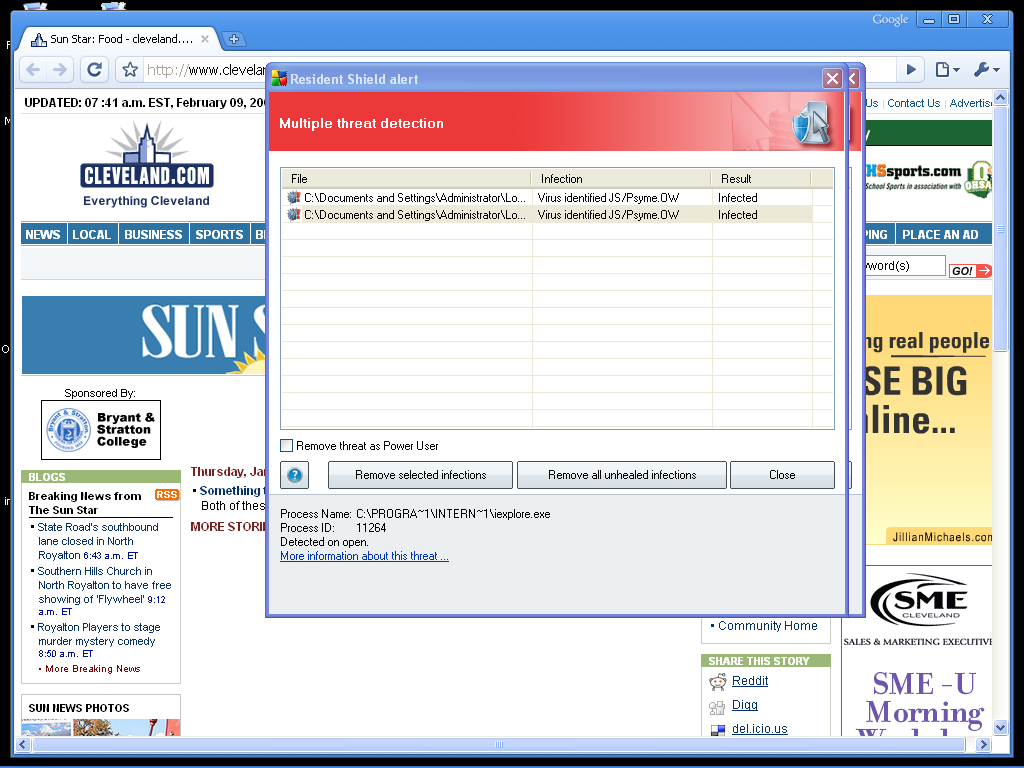
Investigating further reveals that the very same ad network that was used to serve similar Antivirus 2009 pop-ups at AllRecipes.com in November, appears to have been the one (tacoda.net) that cybercriminals once again used in Cleveland.com's case.
With efficiency-centered ad networks in terms of allowing publishers faster access to their networks, every cybercriminal, no matter the ad network in question, can easily become a publisher - the basics of malvertising whose key advantage from the cybecriminal's perspective remains the opportunity to target high trafficked web sites which aren't susceptible to common exploitation tactics.
What ad networks should set as a priority is establishing a more transparent process about what measures -- if any -- have they undertaken to verify that the publisher's sites aren't disseminating malware or client-side exploits. For instance, plain simple cross-checking (for starters) of the rogue security software domains that appeared at Cleveland.com against Google's Safebrowsing database, indicates that they're already marked as harmful.