Router flaws put AT&T customers at hacking risk

(Image: Victor Gevers)
Thousands of routers, many of which belong to AT&T U-verse customers, can be easily and remotely hacked through several critical security vulnerabilities.
Five flaws were found in common consumer Arris routers used by AT&T customers and other internet providers around the world. The flaws were detailed in a blog post by Joseph Hutchins, who described some of the them as being as a result of "pure carelessness."
The report said Arris NVG589 and NVG599 modems with the latest 9.2.2 firmware are affected, but it's not clear who's responsible for the bugs.
Hutchins said that some of the flaws may have been introduced after the routers were delivered to the internet provider, which often adds customized code for remote interactions, such as customer support and diagnostics.
"Some of the problems discussed here affect most AT&T U-verse modems regardless of the OEM, while others seem to be OEM specific," said Hutchins. "So it is not easy to tell who is responsible for this situation. It could be either, or more likely, it could be both."
Among the vulnerabilities are hardcoded credentials, which can allow "root" remote access to an affected device, giving an attacker full control over the router. An attacker can connect to an affected router and log-in with a publicly-disclosed username and password, granting access to the modem's menu-driven shell. An attacker can view and change the Wi-Fi router name and password, and alter the network's setup, such as rerouting internet traffic to a malicious server.
The shell also allows the attacker to control a module that's dedicated to injecting advertisements into unencrypted web traffic, a common tactic used by internet providers and other web companies. Hutchins said that there was "no clear evidence" to suggest the module was running but noted that it was still vulnerable, allowing an attacker to inject their own money-making ad campaigns or malware.
Buggy routers don't always lead to unauthorized network access, but can instead be hijacked as part of botnet operations, like Mirai, which when powered up can target and throw websites and services offline.
Rapid7 reported the vulnerability as an 8/10, on the higher end of the severity scale.
It's not known exactly how many devices are affected, however.
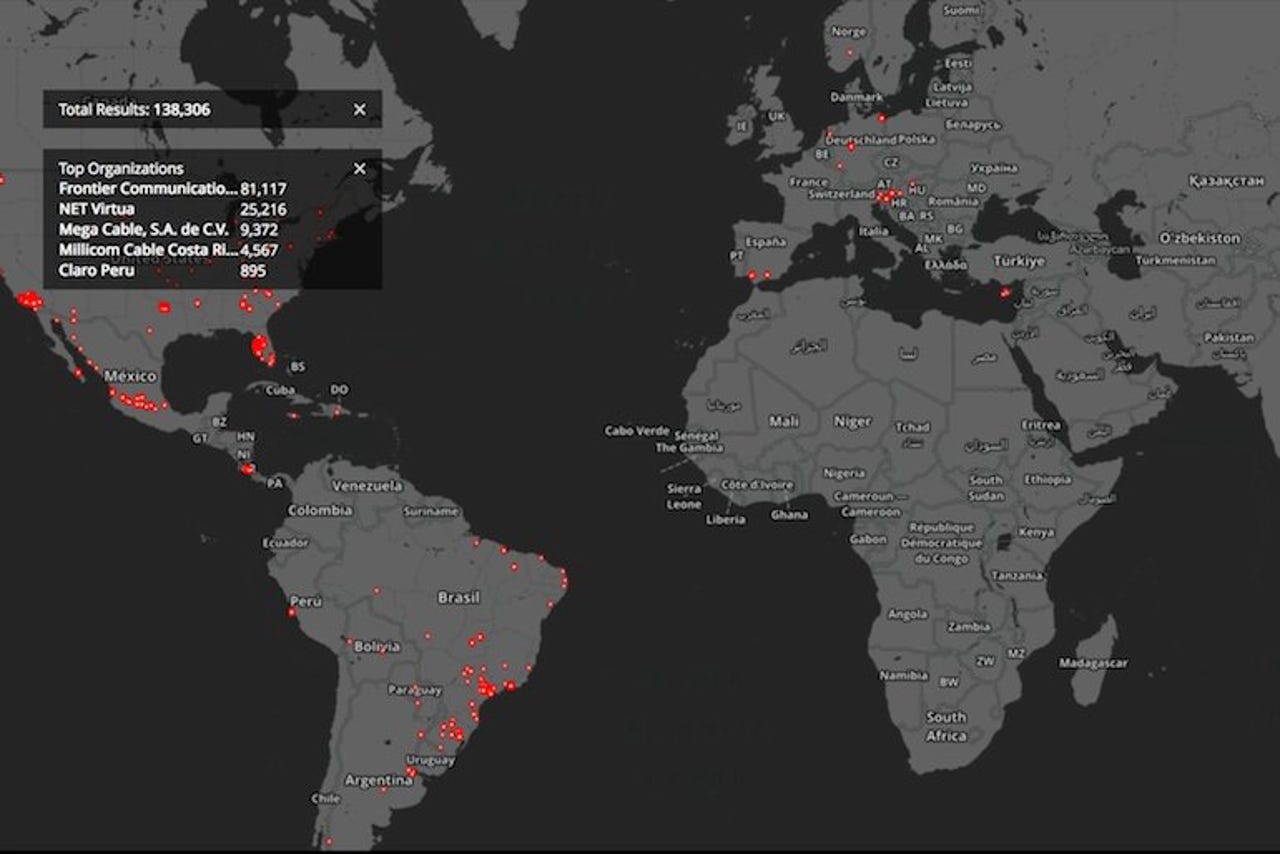
One estimation said as many as 138,000 routers are vulnerable to attackers, according to a tweet by Victor Gevers, chairman of the GDI Foundation, a Dutch non-profit organization dedicated to internet security. The numbers are more nuanced, he explained, and the vulnerabilities are not limited to the hardcoded credentials flaw.
Another bug affects "every single" Arris-built AT&T U-verse device, according to Hutchins, putting potentially millions of customers at risk.
An attacker can bypass the firewall on the device by brute-forcing the half-completed MAC address on the device. Hutchins said that he believes the bug allows AT&T staff to connect to an AT&T-issued television digital recorder on the same network, but the implementation went "terribly wrong."
He said that this "most widespread vulnerability" has the easiest fix. Hutchins has published several self-mitigation methods on the blog.
Hutchins said it was "hard to believe" that the flaws are not being actively exploited.
A spokesperson for Arris said the company wouldn't comment on specifics as it was "currently verifying" the report. "We can confirm ARRIS is conducting a full investigation in parallel and will quickly take any required actions to protect the subscribers who use our devices," the spokesperson said.
AT&T did not respond to a request for comment outside business hours. (Monday is a US national holiday.) We'll update if that changes.