Google on Android ransomware: You're more likely to be hit twice by lightning than get infected

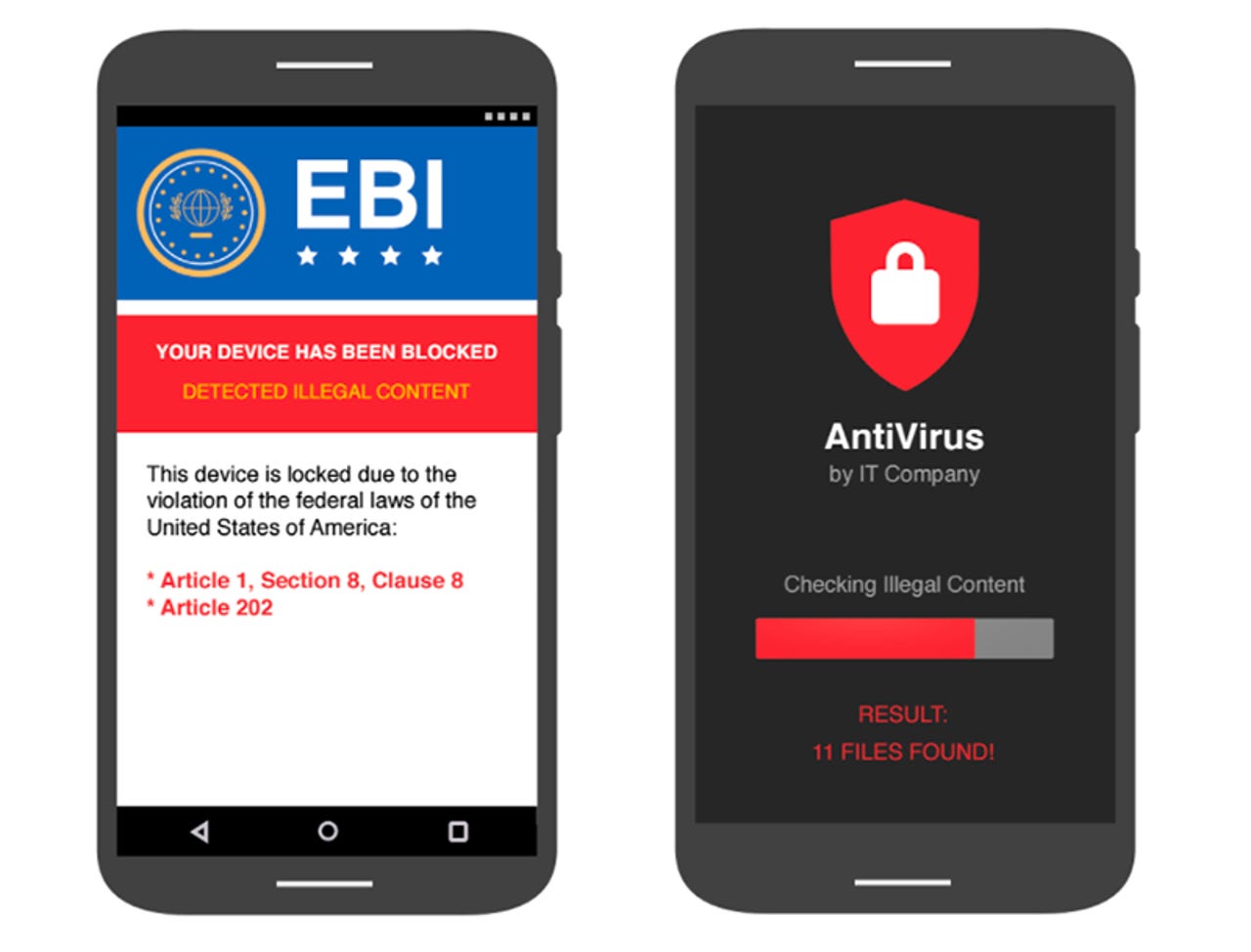
Google argues that Android's application sandboxing offers protection against common types of ransomware such as these.
It was only in January that Google had to remove Android ransomware from Google Play, but the company is now attempting to reassure Android users that ransomware really isn't that much of a threat.
Both police-themed browser lock ransomware and the nastier file-encrypting variety have migrated from PCs to Android. The threat isn't as widespread on mobile as it is on desktops, but it is still worth watching out for.
Verizon Wireless has, for example, posted a support page detailing the different types of ransomware targeting some Android models.
The ransomware app that slipped by Google's Play Store checks in January was cloaked in an alluring but bogus battery-enhancing app called Chargr. The app attempted to steal user data and threatened to sell the information to other cybercriminals unless the victim paid $180 in bitcoin.
Symantec recently found another Android app posing as a porn app that uses 'clickjacking', which attempts to trick users into giving the app administrator rights with bogus system popups. If that's achieved, the app has the power to lock the screen and reset the device's PIN.
Clearly, if your Android smartphone does get infected with ransomware it can be a headache. But, according to Google, ransomware apps are so rare that you're more likely to be struck by lightning twice in your lifetime than your Android device becoming infected with ransomware.
"Since 2015, less than 0.00001 percent of installations from Google Play, and less than .01 percent of installations from sources other than Google Play, were categorized as ransomware," writes Jason Woloz, a senior program manager with Google's Android security team.
Woloz points to a US government source about lightning safety to back up his claim.
He also highlights that Android's application sandboxing offers protection against ransomware. A malicious app on a device without sandboxing technology would have free access to user data and system resources, whereas a sandboxed app prevents this access.
"Sandboxes require apps to mutually consent to sharing data, a protection which limits ransomware's ability to access sensitive information like a contact list from another app," Woloz writes.
In other words, the data that the bogus battery-enhancing app would attempt to trade would not be accessible on Android.
Of course, the older the Android device, the less likely it has the latest defenses that stop ransomware in its tracks. Android 7.0 Nougat has these, but less than three percent of all Android devices have this version.
Google highlights three key protections exclusive to Nougat that do thwart common ransomware techniques.
'Safety binders' prevent apps from seeing what other apps are active, which stops attackers from using current activity to instruct their chosen attack method. Nougat also prevents ransomware from using the device's permissions to change a device PIN.
Nougat also tackles the clickjacking attack. "Clickjacking tricks people into clicking something, often by obscuring permission dialogs behind other windows. You're now protected from ransomware attacks that use this tactic to sneakily gain control of a device," writes Woloz.
If your Android phone does, despite these protections, get infected with ransomware, Woloz offers a two tips: start the device in safe mode and if that fails, do a factory reset.
"First, you can try to boot into safe mode. Starting your device in safe mode means your device only has the original software and apps that came with it. If an app is misbehaving but the issues go away in safe mode, the problem is probably caused by a third-party app downloaded on your device. If you can boot into safe mode, try to uninstall the app and then reboot the device. On a Pixel, you can get into safe mode with a keyboard combination that PHAs can't touch," he writes.
"If safe mode doesn't work, then you might have to reset your phone to factory settings. Many devices running Android allow you to remove dangerous apps by resetting it to factory settings, also referred to as formatting the device, or doing a 'hard reset',
"This should be your last resort, but if you've backed up your files, resetting your device should be easy. Check with your carrier or device manufacturer for instructions on how to reset your phone."