Google Safe Browsing beats rivals but still only flags up 10 percent of hacked sites

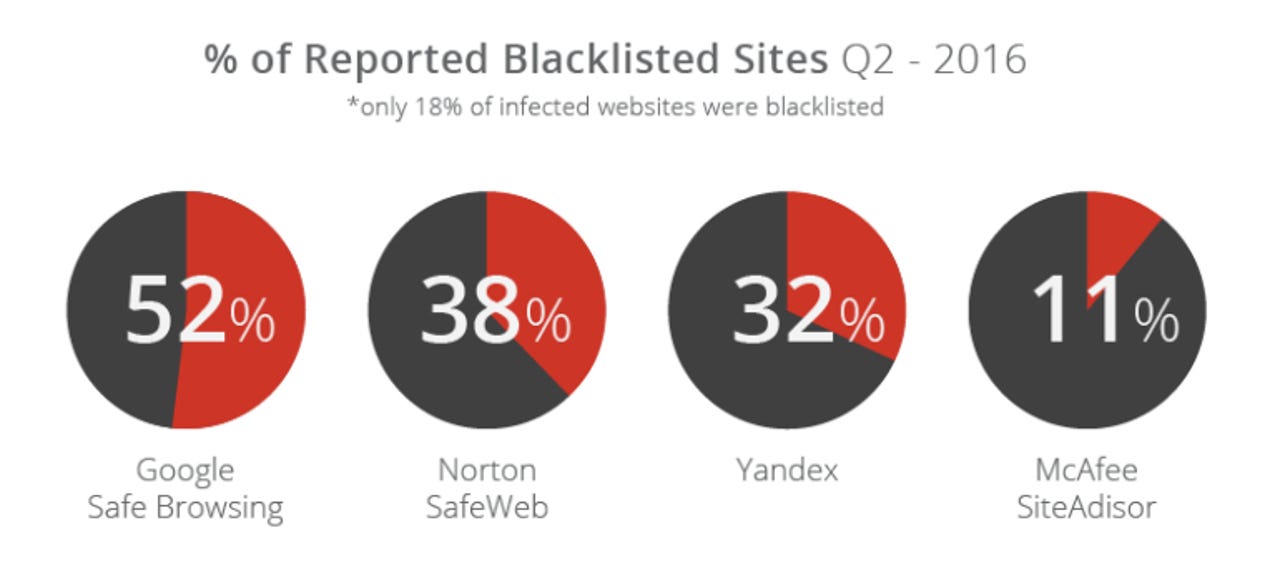
Google's service far outperformed the others, accounting for 52 percent of the roughly one-fifth of sites that have been blacklisted.
Thousands of websites have been hijacked in the past three months, but just 18 percent were blacklisted by four major security services, including Google's Safe Browsing system.
Sucuri's Hacked Website Report for the second quarter of 2016 contains a rundown of 9,771 infected sites that it has recovered in the past three months on behalf of customers.
Security
Only 18 percent of these infected sites have been blacklisted by Google's Safe Browsing, Symantec's Norton SafeWeb, Yandex's Safe Browsing service, or McAfee's SiteAdviser, according to Sucuri, meaning the vast majority have been spreading malware without users being warned about them.
However, Google's service far outperformed the others, accounting for 52 percent of the roughly one-fifth of sites that have been blacklisted. Symantec account for 38 percent, Yandex 32 percent, and McAfee 11 percent. Sucuri notes that Google blacklisted 10 percent of sites it cleaned up in the quarter.
Yet whether this figure spells poor performance is another matter. Google's Safe Browsing technology blacklists tens of thousands of malware and phishing sites each week, warning Chrome, Safari, and Firefox users against visiting them until a site operator has made them safe.
In the week beginning September 4, Google detected 23,100 new sites spreading malware, and 23,500 potential phishing sites, according to the search company's transparency report.
In total, Safe Browsing considers about 500,000 sites unsafe to visit due to malware and a similar number because of phishing threats. Attempts by users to visit these sites result in about 50 million warnings delivered in browsers each week.
Sucuri also noted in its first quarter report that Google doesn't, for example, block spam search-engine optimization (SEO), since it doesn't have a direct impact on users. Spam SEO made up nearly a third of infections in Sucuri's first quarter report, rising to 38 percent in the second quarter.
Backdoors hidden on a site constitute the most common infection type this quarter, giving the attacker a way to gain access to a compromised web server and from there plant other malware, such as redirects to other malicious sites, or launching a so-called drive-by-download infection by exploiting vulnerable software.
This technique accounted for 68 percent of malware, followed by malware used to attack browsers at 60 percent. Meanwhile, phishing and site redirects made up just three percent each of all malware Sucuri encountered.
The figures exceed 100 percent because hijacked sites may have multiple infections. Sucuri noted that on average it cleaned 80 files per compromised site this quarter.
Seventy-four percent of websites it cleaned up were WordPress sites, probably because it's the most widely used content management system, followed by Joomla, which represented 16 percent. Also in the analysis were Magento and Drupal, representing five percent and two percent respectively.
However, the most telling figure for security is the proportion of sites running out-of-date versions. Here, 55 percent of WordPress sites were out of date, while the proportion of out-of-date Joomla and Magento sites jumped to 86 percent and 96 percent, respectively. Similarly, 84 percent of Drupal sites were out of date.
"The challenge of being out of date stems primarily from three core domains: highly customized deployments, issues with backward compatibility, and the lack of staff available to assist in the migration," Sucuri said.
"These tend to create upgrade and patching issues for the organizations that leverage them for their websites through incompatibility issues and potential impacts to the website's availability."
Read more on Google and security
- Google Allo: Don't use it, says Edward Snowden
- Google fixes final 'Quadrooter' flaws with new security patch
- Google offers enterprises Verified Access for Chrome OS devices
- Squished Gmail, Inbox messages? Google readies prettier-looking email for mobile
- Google launches Project Zero bug hunting competition
- TechRepublic: How to migrate Google two-step verification to a new device
- CNET: Google will pay you $200,000 to hack a Nexus 6P and 5X