Google sponsored links spreading (scareware) rogue AV

Malware hunters at Websense Security Labs have discovered legitimate Google sponsored links being used to plant scareware programs (rogue anti-virus applications) on the computers of Windows users.
In a blow-by-blow description of the rogueware attack, Websense researcher Elad Sharf shows how an innocent Google search for the Winrar file archiver and data compression utility can lead to a fake C|Net downloads.com page hosting a legitimate version of Winrar, with a nefarious twist:
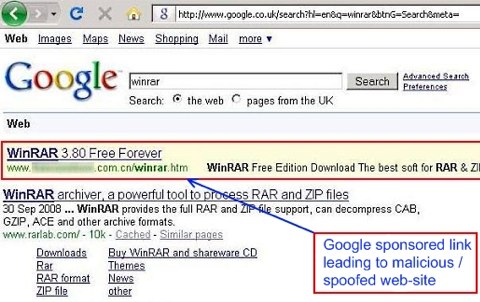
According to Sharf, the installer also drops a malicious file named explore.exe in the Windows system32 folder, and then runs the executable. The malicious file is associated with the icon used by Winrar SFX archives, and it binds to the system's start-up.
The malicious explore.exe file proceeds to change the hosts file to point popular home page sites to a fake Microsoft Security Center site and displays displays a message box at one minute intervals.
This is how the scam works: after installing the infected program, users are interrupted with message boxes at one minute intervals. Thinking that the system has been infected, and irritated at the constant interruption, they might next search for information about the infection using the text that appears in the pop-up message. Finding legitimate forums discussing this infection, they will find confirmation that they are infected. The malware itself offers a fake remedy in the form of a pointer to a fake site. Users with any of the sites in the modified hosts file as their home page, or users who try to access any of those sites, are redirected to a site that pretends to be a Microsoft security center alert.
The end result is the user is tricked into running a security scan using this rogueware and receiving confirmation that the machine is indeed infected. The criminals then attempt to sell a disinfection tool to remove the malware they installed on the victim's machine.
Ugly stuff.