Republican donor site malware skimmed credit cards for six months

There's bad news if you donated to Senate Republicans in the past six months: criminals have likely skimmed your credit card.
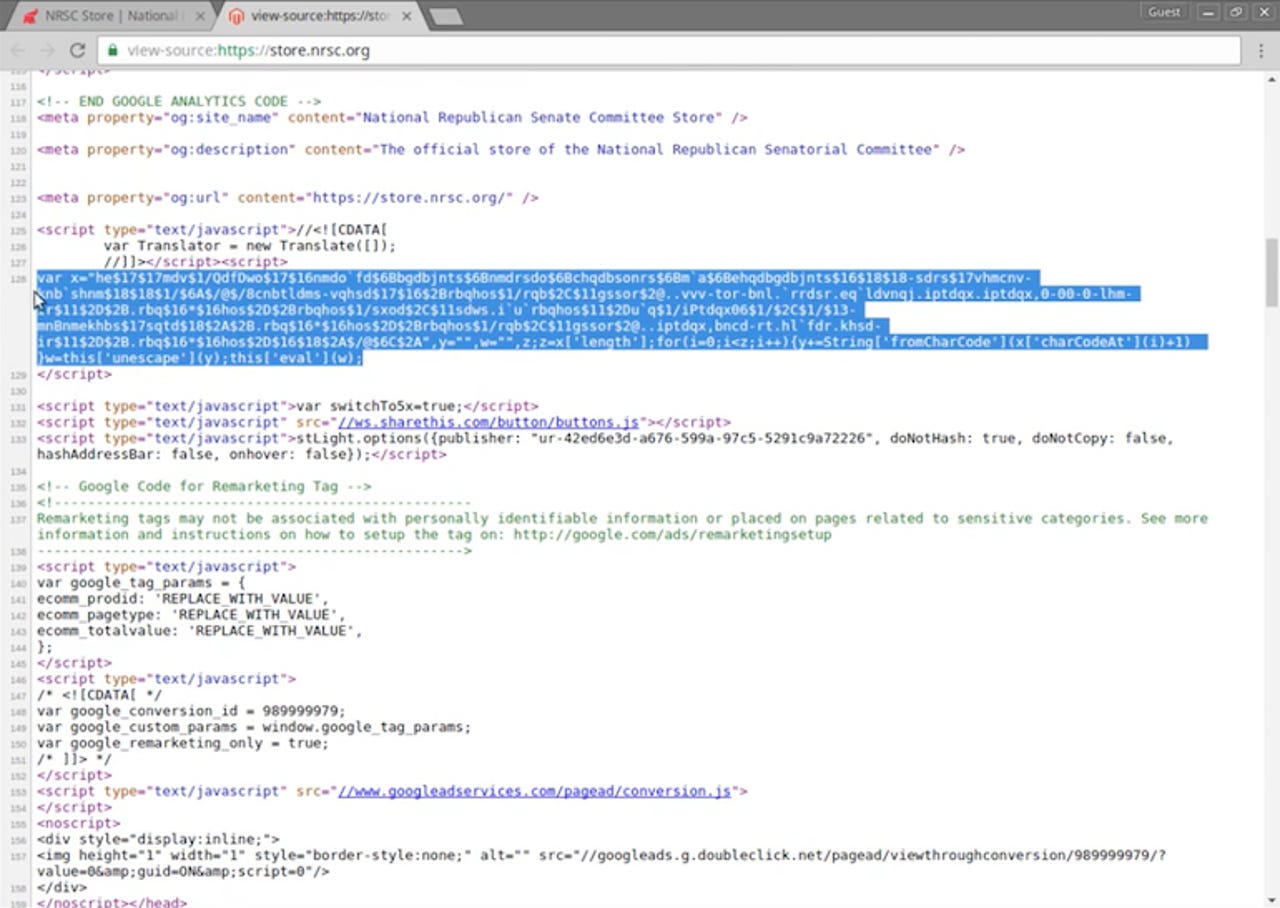
The storefront of the National Republican Senatorial Committee (NRSC) contained malware that siphoned off every credit card number that was entered since March.
The NRSC website was just one of 5,900 ecommerce sites targeted by the same criminal group.
News of the malware was first reported by Dutch security researcher Willem de Groot, who detailed on his blog how the attackers used vulnerabilities and weak passwords to inject the malware into the thousands of sites.
From there, the obfuscated JavaScript "wiretap" could siphon off card information to a collection server, where the data can be sold on the dark web for a going rate of $30 per card.
(Screenshot: Willem de Groot)
A little over just 630 stores have since been fixed, or about one-in-10, according to de Groot.
It's not known how many credit cards were taken in the attack, but estimates show that over 330,000 people may have visited the store in the past 30 days.
The malware isn't just prevalent, it's also persistent, going largely undetected for long periods of time. de Groot said that 754 stores that are skimming today have been since 2015.
What makes it difficult to notice is that the code is silently installed in a webpage's code, and to the untrained eye, looks like regular web code. And because the wiretap code runs on the page, rather than intercepting web traffic, it can run seamlessly over secure HTTPS pages, meaning the user is none the wiser to the malicious code.
"One reason that many hacks go unnoticed is the amount of effort spent on obfuscating the malware code," said de Groot. "Earlier malware cases contained pretty readable Javascript but in the last scan more sophisticated versions were discovered. Some malware uses multi-layer obfuscation, which would take a programmer a fair bit of time to reverse engineer."
A phone call to the NRSC went unanswered Tuesday.