Dogspectus ransomware targets Android devices in the quest for Apple iTunes gift cards

An exploit kit which is delivering the Towelroot exploit kit to Android users is leveraging leaked exploits from Hacking Team's servers to infect victims' mobile devices.
Researchers from Blue Coat Labs said the exploit kit is using a number of vulnerabilities to install malware silently onto Android devices, and malvertising -- the use of fraudulent ads -- is a key component in infection vectors.
In a blog post on Monday, the security team said the attack was discovered when a test Android device, an older Samsung tablet running the Cyanogenmod 10 version of Android 4.2.2, was hit with ransomware after a malicious ad loaded up malicious Javascript pointing to the malware.
According to researcher Andrew Brandt, this is the first time the cybersecurity firm has seen an exploit kit able to install malicious apps onto a mobile device without any user interaction.
"During the attack, the device did not display the normal "application permissions" dialog box that typically precedes installation of an Android application," Brandt says.
The attack in question uses an exploit leaked during the Hacking Team breach in 2015. The Italian exploit seller's databases were breached, leading to the full release of the firm's corporate innards, communication, and cache of zero-day vulnerabilities.
The exploit kit uses one of the leaked exploits which targets libxslt as well as le the Towelroot exploit kit. If successful, the payload delivers and installs an Android application containing the Dogspectus ransomware.
Blue Coat says attacks have been going on from at least mid-February but may have started earlier. At least 224 mobile devices running Android versions 4.0.3 to 4.4.4 have connected to the exploit kit's command and control (C&C) servers since this time period.
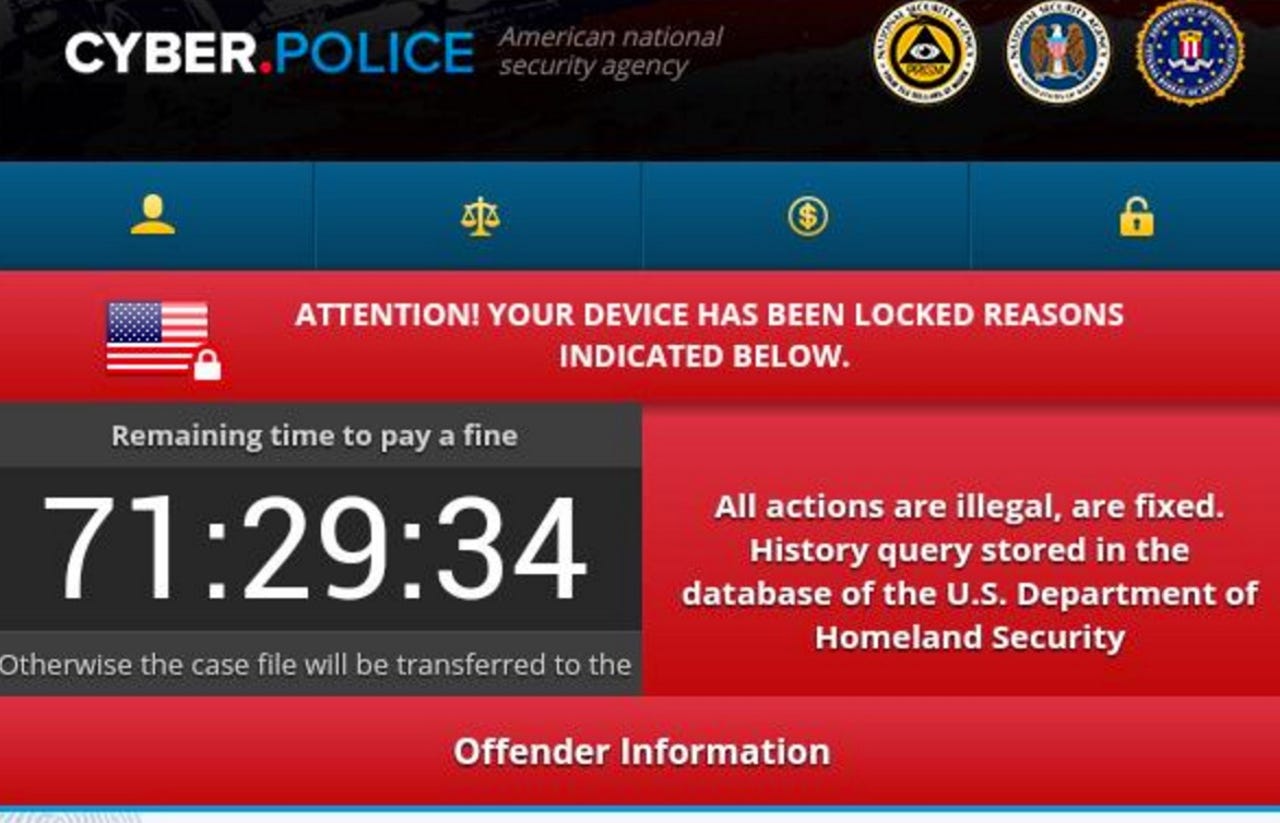
The Dogspectus ransomware, which calls itself Cyber.Police, claims to be a US law enforcement agency spying on the victim's online browsing habits. The ransomware does not, however, encrypt user files, but instead simply locks the device.
All other mobile applications are killed and Dogspectus sets itself up to boot with the device, as well as establishing a link to the C&C server.
While many forms of ransomware then present a lock screen and demand payment in virtual currency, such as Bitcoin, which is hard to track, this particular strain requires a ransom payment of two $100 Apple iTunes gift card codes.
"In theory, it might be possible for Apple (or its iTunes gift card partners) to track who used the gift cards provided to the criminals, which may help investigators identify them," the researchers note.
The only way to remove the ransomware is to perform a factory reset of the device. Better still, keeping your Android smartphones and tablets up-to-date will help you stay protected.
10 steps to learn how to hack
Read on: Top picks