Hackonomics: 'Cyber Black Market' more profitable than illegal drug trade

RAND Corporation's newest report tells us the black market for cybercrime, a "varied landscape of discrete, ad hoc networks of individuals motivated by ego and notoriety, has now become a burgeoning powerhouse of highly organized groups, often connected with traditional crime groups (e.g., drug cartels, mafias, terrorist cells) and nation-states."
In its blog post about the report, Hackonomics: A First-of-Its-Kind Economic Analysis of the Cyber Black Markets, Juniper Networks concluded that the "Cyber Black Market" is more profitable than the global illegal drug trade.
Commissioned by Juniper Networks and released this week, the RAND Corporation's new report Markets for Cybercrime Tools and Stolen Data is both a cabinet of curiosities for armchair cybercrime aficionados, and an interesting collection of observations about the zero day market as told to RAND by its handpicked experts.
To be glib, the report says Twitter accounts are more valuable than stolen credit cards, the hacker's black market is more profitable than the illegal drug trade, bug bounties may not be all that, botnets are still what all the girls are wearing this Spring, reputation is everything, and loose lips still sink ships.
It's not a highly technical paper, though it's steeped in RAND's thoroughness and discipline.
RAND's and Juniper's paper raises a lot of questions and is well worth reading. But RAND is clear about what it doesn't know about the hacker's black market, and I'd be remiss not to mention a few criticisms.
RAND report on markets that was researched by interviewing people…who are not market participants. http://t.co/1hVH8gSeO3
— the grugq (@thegrugq) March 26, 2014
While RAND accessed experts within law enforcement (as well as other handpicked experts), the report didn't appear to be able to include equally the other side of that equation—criminal hackers, their fences, and most importantly, the buyers.
RAND is up front about this, saying:
These experts included academics, security researchers, reporters, security vendors, and law enforcement, each bringing a unique perspective.
(…) Although we sought details, we could not avoid generalities. Many experts did not want to give details lest they interfere with ongoing investigations, alert criminals to what the security industry knows, compromise current clients of security vendors, or provide a “how-to handbook” for getting involved in the black market.
Almost a quarter of the experts spoke on condition of anonymity.
Additionally, the media sources are weighted to one corner of cybercrime reporting, which is fine if all your recent news about malware comes from Brian Krebs. That said, I'll be following this piece with another article, an examination of the prices and cost of goods cited in RAND's paper, versus some places RAND apparently didn't look.
Most interesting is RAND's overall takeaways. Namely, that the black market can't be stopped, and so-called "mom and pop" internet businesses will suffer the most.
RAND's experts agreed in conclusion that in the hacker's black market:
Twitter is becoming a channel of choice; Tor and VPN services are finding increased use.
Additionally, in the wake of Edward Snowden’s actions with the National Security Agency, more of society is concerned with privacy and implementing encryption and protection measures, which will lead to an increase in the number of efforts to break those communications.
The ability to attack will likely outpace the ability to defend.
Attackers can be hedgehogs (they only need to know one attack method, but do it well) while defenders must be foxes (they need to know everything; not just technical knowledge, but knowledge of networking, software, law enforcement, psychology, etc.).
Better than drugs
One point repeated three times in "Markets for Cybercrime Tools and Stolen Data" is that that hacker's black market is poised to surpass the global illegal drug trade in profitability.
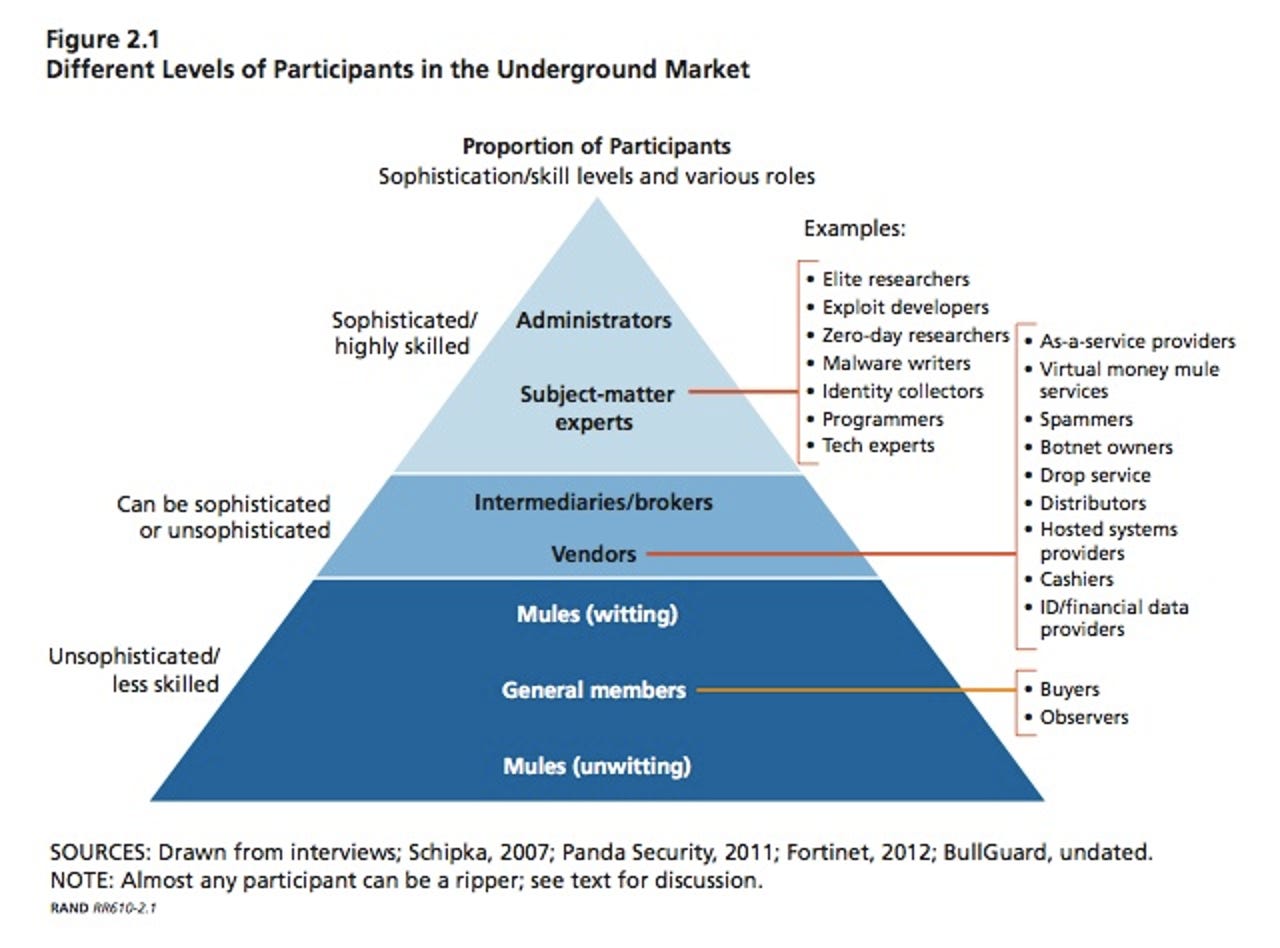
The hacker market -- once a varied landscape of discrete, ad hoc networks of individuals initially motivated by little more than ego and notoriety -- has emerged as a playground of financially driven, highly organized, and sophisticated groups.
(…) The black market can be more profitable than the illegal drug trade: Links to end-users are more direct, and because worldwide distribution is accomplished electronically, the requirements are negligible.
This is because a majority of players, goods, and services are online-based and can be accessed, harnessed, or controlled remotely, instantaneously. “Shipping” digital goods may only require an email or download, or a username and password to a locked site. This enables greater profitability.
In the U.N.'s 2011 Illicit Financial Flows (.PDF) report and analysis, the largest income for transnational organized crime comes from illicit drugs, which account for some 20% (17%-25%) of all crime proceeds; $2.1 trillion or 3.6 per cent of GDP in 2009, with cocaine coming in at $85 billion alone.
Tech Pro Research: Security
But can you really compare a botnet to coke? Perhaps it's like coke for some (I jest), but no one dies when a condom full of exploits bursts open in their stomach while they're on a plane to Miami.
What I mean is that surely a different set of costs, supply, and demand is at work here.
Though to elaborate on RAND's drug trade analogy, apparently those crazy kids are always making new things in their college science labs. RAND noted, "There has been a steady increase in the availability of goods and services offered, from stolen records and exploit kits to “stolen-to-order” goods, such as intellectual property and zero-day (more commonly, half-day) vulnerabilities."
Honor among thieves
RAND's experts had some interesting things to say about the nature of its subjects.
Vendors often guarantee their products’ lifespan or value -- for example, guaranteeing a particular malware variant is good for ten hours before detection by antivirus products, or that a credit card is good for a certain amount of money -- and some can track what a customer does with their product to make sure “terms of use” are not broken -- a sort of “digital rights management."
Unlike the Netflix series House of Cards, where a computer illiterate editor goes on the darknet for the first time ever and instantly finds a black hat ninja to do his dirty deeds, unsolicited approaches are seen as unwelcome on the black market—and if you can get scammed, you will. "As awareness of zero-days has increased, access to them has not. One still needs to be sophisticated and certainly needs to know the right person (…) but even those 'right people' stay quiet."
It’s all about operational security and reputation, just as we'd expect. RAND suggested that scams are rife, but also described the world as a self-policing community.
The black market continues to put great stock in reputation, at least within the harder-to-access tiers. Thanks to an increase in takedowns (of sites, groups, tools, or individuals), participants have labored to loosen the correlation between virtual identities and real identities. Thus, markets have seen more anonymous currencies and encrypted and stealthy communications.
More of the market is hosted on darknets and through VPN services. While this trend does not affect reliability of products (some say it will make it stronger because only the highly vetted make it in), it reduces the accessibility and availability of the market. It also leads to much more intense personal vetting.
RAND added, "The harder-to-access tiers where participants are highly vetted—are often well structured and policed, with their own constitution-like rules and guidelines to follow. That said, plenty of the market does not have rules and regulations—one reason experts say the black market can outpace the legitimate world."
Sorry about your bug bounty
"Markets for Cybercrime Tools and Stolen Data" was compiled during November and December 2013, around six months after Microsoft launched a bug bounty program aimed at shifting the black market. Katie Moussouris, Senior Security Strategist Lead at Microsoft, said the program's goal was "to disrupt the black market for security bugs, as opposed to competing with it."
Critics said that Microsoft was paying too little, though it expanded the program in November to pay $100K to, well, snitches.
RAND still heard it wasn't enough. "Some sources say a researcher could earn 10–100 times what a software vendor with a bug bounty would pay."
RAND observed that the increased attention to the zero day market from media and forward-facing bug bounty programs "could better regulate the prices, but could be negative in other aspects (i.e., drain the funds of security vendors, cause more nefarious actors to buy the more reasonably priced zero-days)."
But again, the caveat: "Currently, there are too little data to suggest the trend in prices."
Maybe that's because successful hackers working in the black market today aren’t the ones talking about it in press and media.
It is debatable whether there is more openness about buying and selling zero-days. There certainly is more chatter about zero-days: There are more news reports and articles; companies that deal with zero-days are rising; and bug bounty programs are burgeoning.
But one result of this increased attention is that brokers and those who interact in this market have closed ranks and become more reticent in talking about zero-day markets.
Reading between the lines is always fun.
Despite my hesitations, I found "Markets for Cybercrime Tools and Stolen Data" useful, entertaining and interesting, and I'm looking forward to Juniper's next report.