How these fake Facebook and LinkedIn profiles tricked people into friending state-backed hackers

A screenshot of the fake Facebook page used to lure victims of the hacking campaign.
Are you sure you know who that LinkedIn contact really is? They might not be who they really claim but instead a hacker looking to scrape your profile -- or worse, manipulate your actions.
Cyberespionage activity apparently being conducted on behalf of the Iranian government is targeting organisations in the financial, oil, technology, and other sectors, with advanced social engineering based around a single, prolific social media persona that's absolutely fake. Its goal? To install Trojan malware onto the networks of target organisations.
Security
The operation, uncovered by cybersecurity researchers at SecureWorks, is the work of a group, apparently associated with the Iranian government, which uses spear-phishing to compromise targets.
At the beginning of this year, researchers saw an phishing campaign targeting individuals in organisations predominantly in the Middle East and North Africa, with some targets in the US. The emails' general subjects included job offers and requests to reset passwords.
These lures contained shorted URLs, which led to documents that, when opened, installed PupyRAT, an open-source remote access Trojan which can infiltrate Windows, Linux, OSX and Android to give the threat actor full access to the victim's system.
But when fewer targets fell for the scheme than expected, the hacking group tried again with a fake social media profile that had been interacting with some of the targets since the middle of last year.
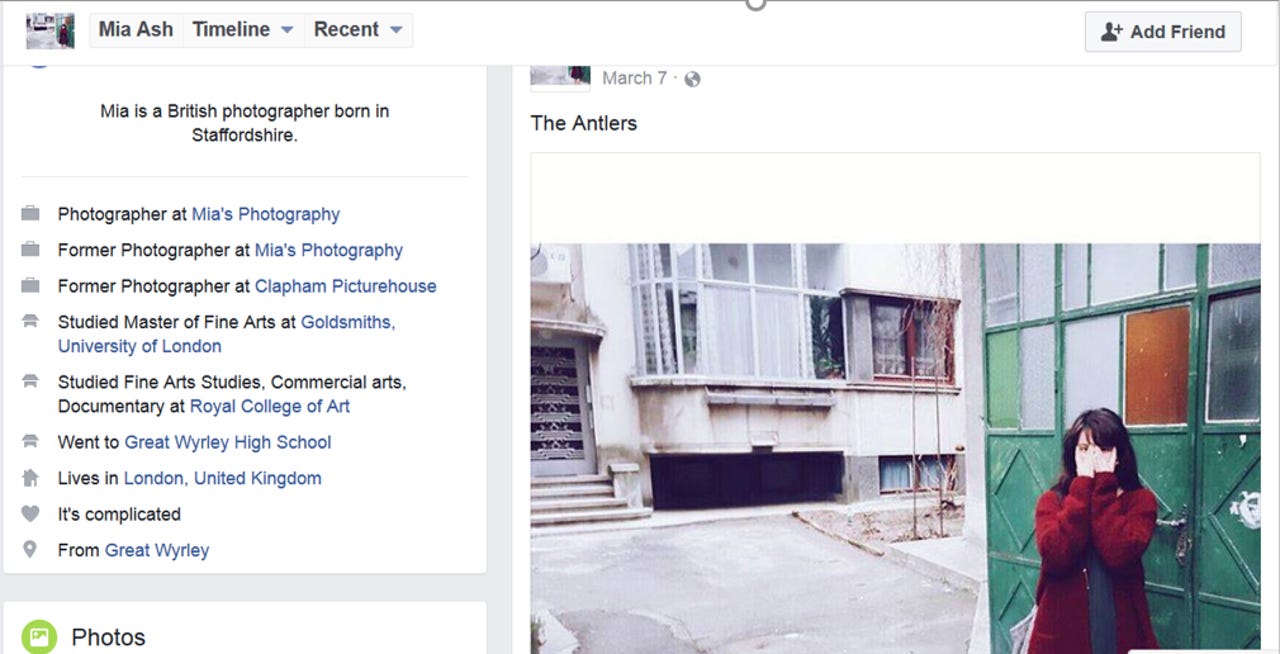
Named 'Mia Ash', the profile purported to be a young woman working in photography in London and struck up a rapport with various targets over social media. However, the persona was completely fake, and used the Instagram photos of a young woman in Eastern Europe.
"Mia Ash was the follow-up activity to an unsuccessful campaign, which is why they brought out the big guns and used the persona to directly target individuals on LinkedIn," Allison Wikoff, senior security researcher at SecureWorks, told ZDNet.
The profile has been active since April 2016 and has over 500 connections on their LinkedIn profile and an even larger number on Facebook. The LinkedIn account has stolen a job description from a legitimate photographer in the US and initially appears to have connected with others in photography in order to look authentic.
The campaign then began adding targets, such as people who work for Middle Eastern or African based companies in the telecommunications, technology, and oil and gas sectors. Hundreds accepted the request, many with roles such as IT support, technicians and engineers -- people who would have higher level access than normal users.
"Most of these folks had job descriptions that would indicate they might have privileged access at their company," said Wikoff. "It shouldn't be surprising, but they were all men -- they're using the 1,000 year-old ploy," she added.
Of course, in this case, there's no real person, just a group of attackers operating a profile, but one which regularly interacts with victims who also react back.
"The Mia Ash Facebook profile was very active, it was publishing new photos regularly and there's quite a few comments from targets which are commenting on these photos. They haven't friended her and never paid attention again, there's lots of likes from the same people," Wikoff explained.
The attack begins with messages over LinkedIn, before moving across to Facebook then eventually email. In one particular instance of the campaign studied by researchers, the email exchange ended up with 'Mia' sending the target an email a Microsoft Excel document 'Copy of Photography Survey.xlsm' and urged them to open it at work in for it to 'function properly'.
This survey continued macros which, once enabled, downloaded the PupyRAT Trojan onto the targeted system, giving the attackers access to the network.
"They really put a lot of effort into this and going into the catfishing," said Wikoff. "They put the P in persistent threat. The initial attack didn't work so the threat actor has a persona they've had built and ready to go to go back to the organisations they want to get into."
The group remains in operation and is still attempting to infiltrate the networks of thousands of organisations across the globe, particularly in the Middle East and Africa. SecureWorks says the operation is by one of the most prolific hacking groups in the world, more prolific than Fancy Bear or various Chinese groups.
As for the woman who was having her photos stolen for this cybercriminal operation, SecureWorks managed to get in touch and she was "shocked" at what was going on -- but the images used in this piece are used with her permission. LinkedIn has removed the fake account.
Not only does this case demonstrate the dangers of highly-sophisticated cyberattack operations and the risks of connecting to unknown social media accounts, it hammers home how you should lock down your own social media accounts, because who knows who might be watching you.
READ MORE ON CYBERCRIME
- Flattering to deceive: Why narcissists are an easy target for hackers
- How to become a master cyber-sleuth [TechRepublic]
- Cybercrime Inc: How hacking gangs are modeling themselves on big business
- A hacker's next target is just a Web search away [CNET]
- Hackers are using this new attack method to target power companies