How to remove Superfish adware from your laptop

UPDATED: No one likes crapware--the adware and trial software that PC and smartphone vendors put on their devices. Until recently, though we rarely got actual malware installed on new computers. Now, thanks to Lenovo and Superfish Visual Discovery adware, we didn't merely get injected ads in our search engine results, we also had our computer doors opened to man-in-the-middle Secure-Socket Layer/Transport Layer Security (SSL/TLS) attacks.
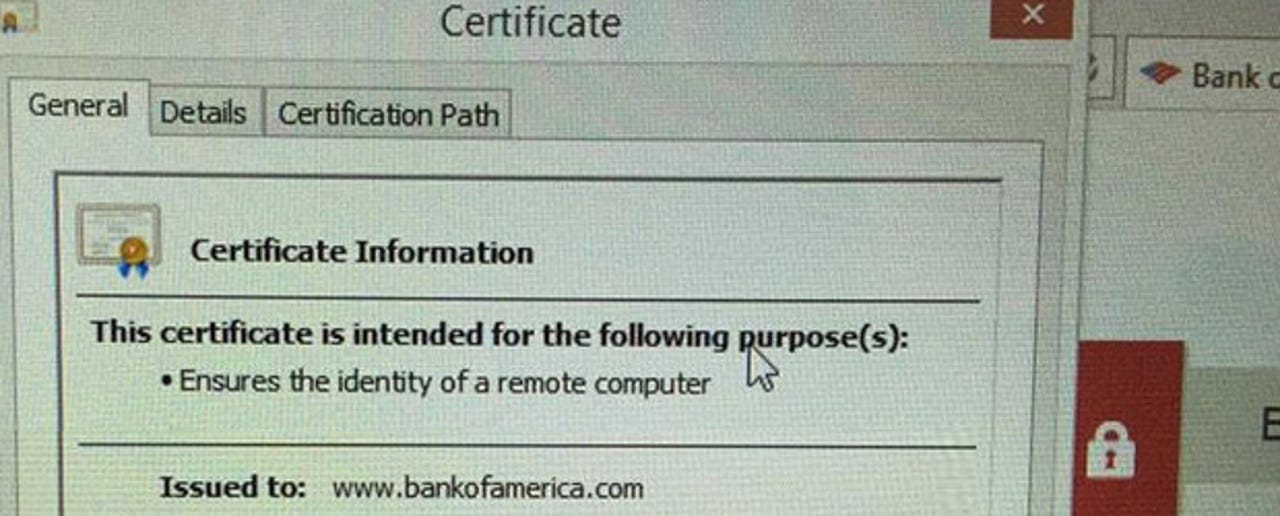
What Lenovo didn't say was that Superfish was installing its own self-signed root certificate authority (CA), This enabled the Superfish software to void SSL/TLS connections and gave hackers a hole to be used in man-in-the-middle (MITM) attack and view the contents of any "encrypted" connections.
This hole was discovered on January 21 by a Lenovo user. Lenovo, however, while no longer installing it on new systems, didn't alert users of the potential danger. This hole can be used against you no matter which Web browser you're using.
Then, the problem with Lenovo consumer laptops running Windows 8.1 sold between September 2014 and January 2015, was shown to be even worse than expected. Google security engineer, Chris Palmer, showed on Twitter that Superfish was intercepting SSL/TLS connections and injecting its own self-signed certificates for all sites on his Yoga 2 laptop. This included such sites as the one for Bank of America.
On February 19th, the problem went from merely terrible security practice and a potential problem to being a real security hole. Robert Graham, a security hacker, extracted the password that Superfish uses for its CA and published it. This means that, as Graham put it, "I can intercept the encrypted communications of SuperFish's victims (people with Lenovo laptops) while hanging out near them at a café wifi hotspot."
So, since if you're in a coffee shop right now using your new Lenovo to look at a secured Web site open in another tab, you could be having your password stolen at this moment, here's how to zap Superfish.
First, you need to get rid of the program. To do that, first take the following steps:
- Go to Control Panel > Uninstall a Program
- Select Visual Discovery > Uninstall
According to Lenovo, that's all you need do and besides"We have thoroughly investigated this technology and do not find any evidence to substantiate security concerns." In part, Lenovo states this because "Superfish has completely disabled server side interactions (since January) on all Lenovo products so that the product is no longer active. This disables Superfish for all products in market."
I don't buy it. If that's the case then Palmer never should have been misdirected while browsing with his Lenovo laptop on February 18th.
This issue aside, the bad certificate will still be on your Windows system. To get rid of it, run the Microsoft Management Console, Mmc.exe (you need an administrator's credentials to do this), and do the following:
- Go to File -> Add/Remove Snap-in
- Pick Certificates, click Add
- Pick Computer Account, click Next
- Pick Local Computer, click Finish
- Click OK
- Look under Trusted Root Certification Authorities -> Certificates
- Find the one issued to Superfish and delete it.
You can't just rerun CertMgr.msc directly because that only shows the user account, not the Computer Account cert store. The bad Superfish certificate lives at the Computer Account level.
Even after this, there will still be some Superfish registry entries left behind, but they are not likely to be dangerous.
To get rid of those you may want to try a registry cleaner, although, as ZDNet resident Windows expert Ed Bott puts it, "registry cleaners are the 21st Century equivalent of snake oil." Still, if you want to be do your best to clean out every last remnant, you should use Piriform's Ccleaner registry cleaner.
It may also be possible that if you're using Firefox or Chrome there may be a cached copy of the bad certificate. To check on this, with Firefox enter:
about:preferences#advanced
on the address bar. On the menu that comes up, choose Certificates and then View Certificates. Once there, look for Superfish in the list of Authorities. Once you find it, delete it.
On Chrome, go to Settings/Advanced Settings/HTTPS/SSL/Manage Certificates. In the Certification Manager, go to Authorities and look for Superfish. If you find it, delete it. If the delete button is not active, choose edit instead and uncheck all the "Trust this certification" radio buttons.
To make sure that Superfish is no longer intercepting your secure communications, go to the Superfish CA test Website.
Last, but not least, do these steps now. If you don't, every time you go to a "secure" Website with your new Lenovo laptop, you're telling the world to steal your IDs and passwords.
Related Stories: