If this "personalized spam" can scale, we and the Net are in very big trouble

It's been quite a while since I covered the topic of spam from a technical point of view. I used to go deep on the issue. I would propose potential solutions, vet other ones, and tell readers why most of the ideas they were coming up with -- for example, a National Do-Not-Spam Registry -- were well-intentioned, but ultimately, unworkable. I even formed an event (JamSpam) that pulled all the major vendors together in hopes of getting them to produce some anti-spam standards. But it was too no avail. For the most part, vendors see big money in being the one who can best stop spam. And so, there's no incentive to collaborate in a way that produces some standards that would ultimately mean no one makes money on stopping spam (which is the way it should be). It's a long story.
The bad news? There are still no such standards. More bad news? There's no sweet spot in today's anti-spam systems. What I mean by this is that all anti-spam systems have some knobs and levers that are controlled by the e-mail recipients (or administrators) and there's no way to perfectly tune them so that all spam is kept out and all the good e-mail is let in. The sweetest spot that can be found is one where some spam still gets through, and some good e-mail gets tagged as spam (known as a false positive). The result is that we have to double check our anti-spam or junk e-mail folders (known as "honey pots", these are the places where our anti-spam solutions are dumping suspected spam) anyway. I now do it twice a day because of the number of legitimate e-mails that are somehow getting dumped there -- some of them important ones. If we have to double check our honey pots, we might as well not have anti-spam systems at all. That's because the whole point of these systems to save us the time it would normally take to manually decide if something is spam or not.
So, why write about spam again now? Because I've noticed a new kind of spam that's quite amazing in how it can probably beat most anti-spam systems and I'm wondering if robots are doing the work or if some human is doing this by hand. I suspect it's robots which is why it has me worried because it looks like there are humans at work (not a scalable system). This new form of spam appears to be very personalized to me. For example, the subject lines in a lot of the spam I've been getting appears extremely targeted to my interests. The last such spam to show up (promoting penny stocks) had the following subject line:
Creating the Portlet ClassAs a first step, create the portlet class and name it MashupMapPortlet, as described in this section.
Then, the body of the spam includes the following text:
In tests, Sun's Java Enterprise Performance team has found that the two operations take about the same amount of time. In the future, you might expect deployment through annotation processing to improve more than deployment through XML parsing. Externaldependencies that cannot be injected through resource injection, suchas JDBC or message queue connections, can still be cached while yourbeans are active. In the future, you might expect deployment through annotation processing to improve more than deployment through XML parsing. You could solve this problem by making the MBean a Dynamic MBean rather than a Standard MBean and by implementing the DynamicMBean. DefinitionFirst, define the portlet class in MashupMapPortlet. Another potential problem appears when trying to determine stringequality.Keys and certificates stored in MS Windows key containers and certificate stores, known as keystores, can be accessed by using the java. Working within the Swing toolkit, I've learned to pick up things from source code. Defining a Type for the Bundle of ValuesAn alternative approach is to define a Java class that represents the relevant bundle of values. But you can write first-rate Swing applications that are very quick and perform well.MXBeans are used in the java.
jsp page contains an HTML scripttagrendered by the renderer, Compiling a ProjectOnce you have finished modifying the code, you can either compile classes individually or compile and build the entire project. In particular, the MemoryUsage example in the previous section is inspired by the MemoryUsage class from that package and by the MemoryMXBean interface that uses it.More than one provider supports RSA cryptographic services: The SunRsaSign provider offers the RSA KeyPairGenerator and Signature services and the SunJCE provider offers the RSA Cipher service. jsp is mostly JavaScript code....
For the most part, this passage makes no sense and there is no connection to the subject line. But what's scary is that this is the sort of stuff that I'd normally read. And I'm pretty certain that someone, or worse, some machine knows that. This isn't the only spam I've gotten like this. I'm getting a lot of spam that indicates somebody or some thing has some how picked up on my areas of interest, and, as a result, is sending spam to me that includes text that easily gets by the watchful eyes of any anti-spam system I've set up. I'd say about then of these have found their way into my inboxes in the last week. All of this work to sneak the following graphic onto the display in front of my face:
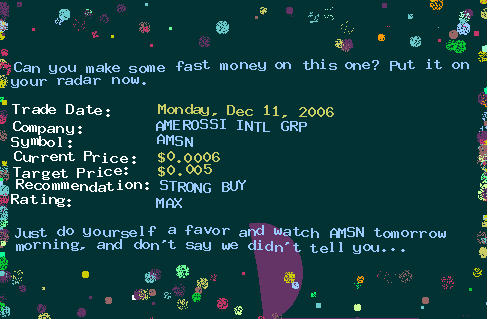
First, the reason spammers use graphics is because graphics are a means of presenting text that can't be examined by anti-spam technologies that normally inspect an e-mails text. Many anti-spam technologies just throw graphics since not much can be determined by their presence. Second, take a closer look at this graphic. Not only was the text in the main e-mail designed to fool most anti-spam systems, the text in the graphic is designed to fool any software that tries to scan graphics for offending text. Because the characters are "wavey", most scanning software won't even realize there is text in this graphic.
The level of sophistication in this spam -- and the fact that it's getting by two anti-spam technologies that I rely on (a centrally managed version of Spam Assassin and Outlook's built-in anti-spam tech) is quite scary.