iHacked: jailbroken iPhones compromised, $5 ransom demanded
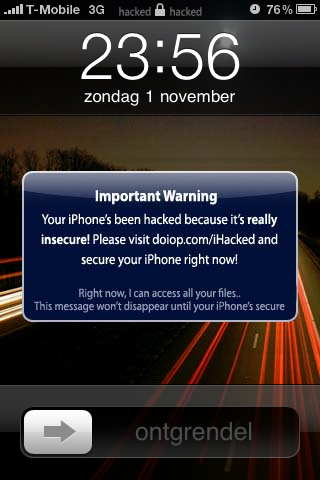
Through a combination of port scanning and OS fingerprinting of T-Mobile's 3G IP range, a Dutch teenager has for the first time automatically exploited a known security vulnerability introduced on jailbroken iPhones - the SSH daemon which unless modified remains running with default users root and mobile, using the same password on each and every device.
Here's what he demanded, and how he changed his attitude following the suspension of his PayPal and the spamvertised URL:
The now taken offline site was featuring the following message:
"Dear iPhone user,
Your iPhone is not secure. That's the reason your visiting this page, isn't it? Well you can pay me $4,95 at my paypal account PureInfinity92@mailinator.com, and I'll mail you very easy instructions on how to secure your iPhone. You can also contact me at PureInfinity92@gmail.com
If you don't pay, it's fine by me. But remember, the way I got access to your iPhone can be used by thousands of others. And they can send text messages from your number (like I did..), use it to call (or record your calls), and actually whatever they want, even use it for their hacking activities! I can assure you, I have no intention of harming you or whatever, but, some hackers do! It's just my advise to secure your phone (: Have a nice day!"
Why is this automatic exploitation not a surprise?
- Go through related posts: iBotnet: Researchers find signs of zombie Macs; iPhone's anti-phishing protection offers inconsistent results; Snow Leopard's malware protection only scans for two Trojans; New Mac OS X DNS changer spreads through social engineering
The exploitability of the default SSH root login combined with the ease of OS fingerprinting an iPhone's, and the descriptive and well known 3G IP ranges for certain service providers, has already been discussed as an opportunity for automatically exploiting jailbroken iPhones running the SSH daemon with default passwords.