Inside the botnets that never make the news - a gallery
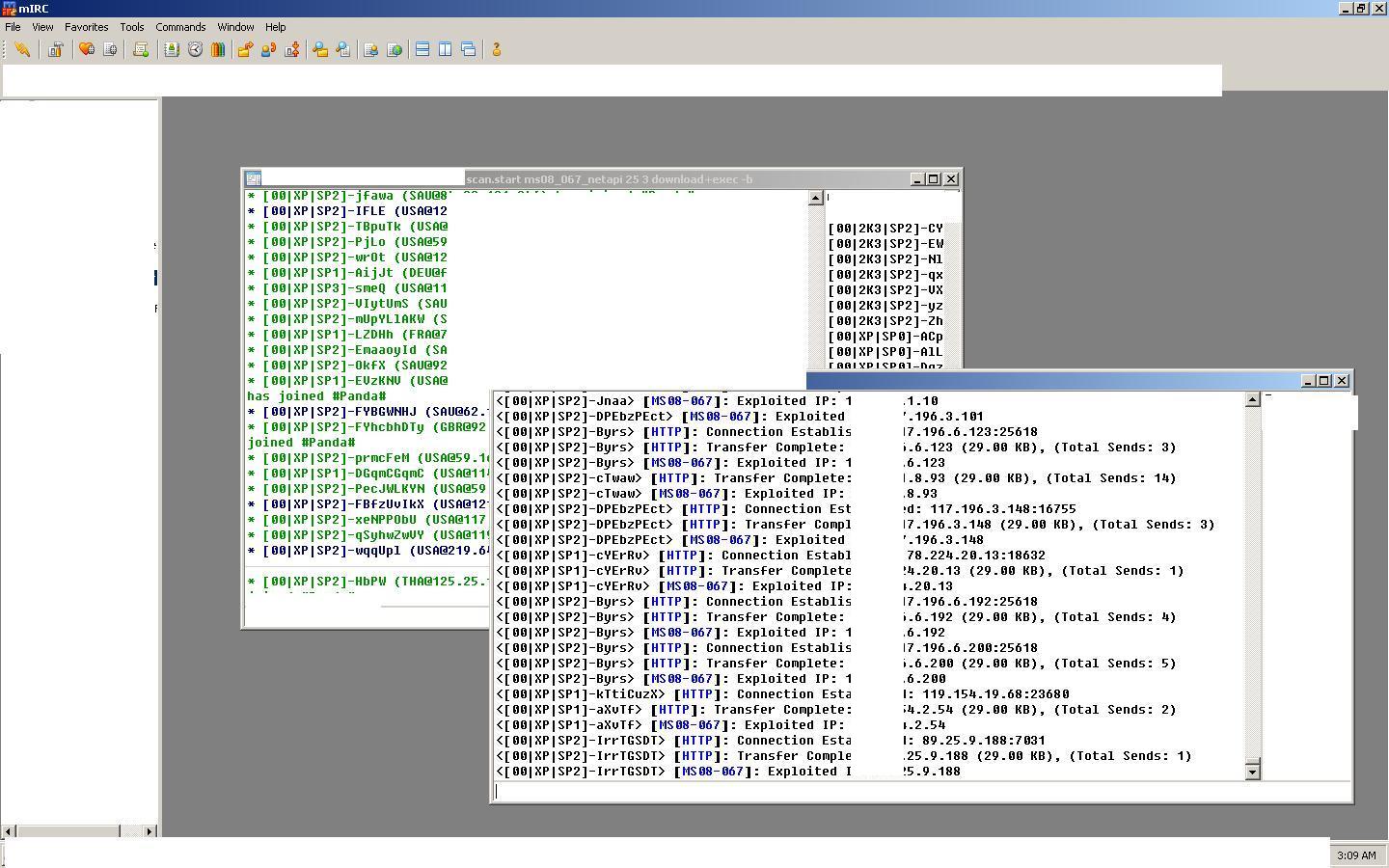
It offers an inside view of those "beneath the radar" botnets that never make the news. The images have been collected throughout the past year by using open source intelligence, namely, by either joining the command and control IRC channel upon infection, or monitoring ongoing communications between the botnet masters.
Why are small botnets so important anyway, and shouldn't we keep an eye on the big ones such as Conficker, Torpig or the rest of the eye-popping ones? Smaller botnets are usually underestimated ones, however, they're perfectly suitable for targeted attacks such as the recently exposed GhostNet espionage network. Moreover, despite the massive botnets run by sophisticated cybercriminals, evidence in the past (Storm Worm Hosting Pharmaceutical Scams; Money Mule Recruiters use ASProx's Fast Fluxing Services; Inside the Srizbi Botnet Business Model) clearly indicates that they're partitioning the botnets and reselling pieces of the pie to other cybercriminals, which would then simply remove the original malware and introduce one of their own.
These small botnets are also exclusively used for some of the sophisticated managed spam services currently offered on the underground marketplace. For instance, the managed spamming service exclusivelly profiled by Zero Day last year, was using only 5000 infected hosts for the purpose of sending 1 million spam messages. Another variation of it was offering only 1672 infected hosts, and was still capable of spamming 3215 emails per minute.
For the time being, the massive botnets we're used to seeing aren't going away, but in the long term the cybercriminals behind them could easily start splitting/partitioning them for operational security, and in order to avoid potential mass hijacking from competing cybecriminals or security researchers - the malicious economies of scale that cybercriminals achieve by standardizing the exploitation process also means that their crimeware botnets are vulnerable to the logical monocultural insecurities.
What do you think?