Korea attacks force DDoS bunker creation

South Korea has installed digital "bunkers" to prevent a repeat of the massive distributed-denial-of-service (DDoS) attacks that crippled parts of the country last year.
The nation was floored after huge streams of junk internet data poured across South Korea's networks last year, targeting the infrastructure of government and businesses in what is known as a DDoS attack.
It took-out parts of the communications networks for up to a week, also hitting US targets, before the malware behind the DDoS attacks self destructed.
"We were caught off-guard," Jinhyun Cho of the Korea Computer Emergency Response Team (KrCERT) told ZDNet Australia. "It was on the mouths of everyone; the whole country knows what a DDoS attack is."
The attacks forced blasé telcos to cooperate with KrCERT and forge "DDoS bunkers" to protect the nation's small-to-medium enterprises from attack.
Simply-put, a "bunker" is a new IP address served to a business that is under persistent DDoS attack but lacks the funds or resources to protect itself. Traffic from the DDoS attack continues to hit the original IP address (2.2.2.2 in the image) while the business remains in operation under a new address (1.1.1.1 in the image).
Cho said it is an effective, but temporary measure and expects businesses would revert to their original address after about a week.
KrCERT is also using anti-DDoS technologies such as sinkholes (PDF) and tarpits.
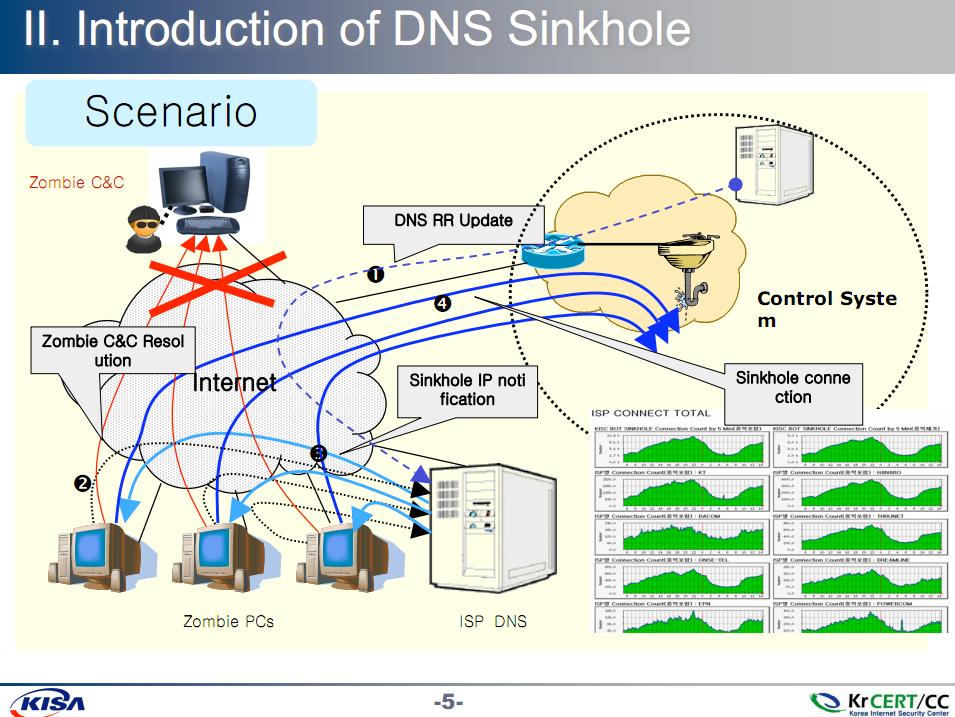
KrCERT's Botnet sinkholes.(Credit:KrCert)
South Korea is continuously under DDoS attack, Cho said, and the bunkers are hoped to help mitigate part of the problem.
He said there have not been further DDoS attacks on the scale of the 2009 assaults, but that attacks have increased in size.
Cho wouldn't be drawn on the origin of the attacks because the government is still investigating.
The attacks have peaked the interest of government and police, which have thrown cash, brains and people into KrCERT. The organisation has gained more staff and meets regularly with industry and government to discuss cyber security.
Cho was a delegate and speaker at the Asia-Pacific Telecommunity cyber security forumheld in Sydney this week.
Frontpage image credit: bunker image, by Ramorli, CC BY-SA 2.0