Researchers: Lenovo laptops ship with adware that hijacks HTTPS connections

Lenovo has been pilloried by a number of security experts for shipping software in its consumer Windows devices that not only injects advertising into search engine results, but also has the capability to intercept and hijack SSL/TLS connections to websites, thanks to the installation of a self-signing certificate authority on affected machines.
The issue has remained latent since Mark Hopkins, a Lenovo social media program manager, confirmed in January that the company was installing the Superfish Visual Discovery software on some of its products in order to serve ads.
"Due to some issues (browser pop-up behavior, for example) with the Superfish Visual Discovery browser add-on, we have temporarily removed Superfish from our consumer systems until such time as Superfish is able to provide a software build that addresses these issues. As for units already in market, we have requested that Superfish auto-update a fix that addresses these issues," Hopkins wrote in a Lenovo forum.
"To be clear, Superfish comes with Lenovo consumer products only, and is a technology that helps users find and discover products visually. The technology instantly analyzes images on the web and presents identical and similar product offers that may have lower prices, helping users search for images without knowing exactly what an item is called or how to describe it in a typical text-based search engine."
Hopkins said that the software does not monitor user behaviour, with each session being independent.
"When using Superfish for the first time, the user is presented the Terms of User and Privacy Policy, and has option not to accept these terms, ie, Superfish is then disabled," Hopkins said.
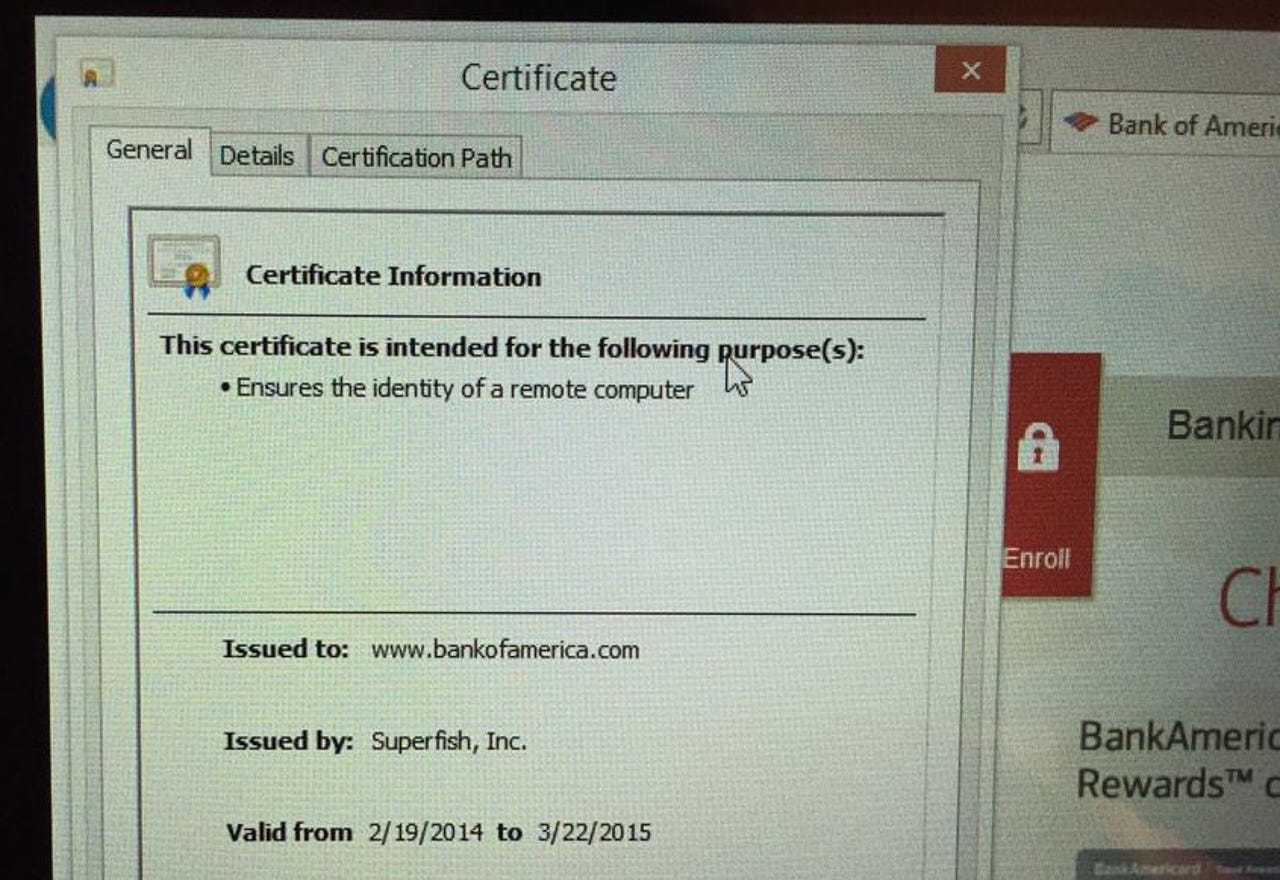
However, another user on Lenovo's forums discovered that Superfish was installing its own self-signed root certificate authority, allowing the Superfish software to conduct a man-in-the-middle (MITM) attack and view the contents of any connections that should be encrypted.
A Google security engineer, Chris Palmer, confirmed on Twitter that Superfish was intercepting SSL/TLS connections and injecting its own self-signed certificates for all sites on a Yoga 2 laptop, including for Bank of America.
The installation of Superfish onto new Lenovo laptops has seen a number of customers complain that the software was interfering with other digital certificates, as well as smart card readers.
Potentially most damaging of all, Palmer has confirmed with one other affected user that the certificates used share the same key, which leaves any impacted Lenovo user vulnerable to an attack from anyone able to extract the certificate's private key, with the user left without any warning or notice of such an attack.
The only remedy to removing Superfish appears to be reinstalling Windows from a non-Lenovo image, or moving to another operating system -- uninstalling the Superfish software can reportedly leave the root certificate authority behind.
Lenovo was approached for comment, but had not responded by the time of writing.