LinkedIn panics, legal threats fly into hacker search engine inbox

LinkedIn's legal threats have successfully stopped a hacker database keeping the data of millions of users up for public searches, but it is likely to only be a temporary fix.
LinkedIn suffered a data breach in 2012, with what was believed to be 6.5 million user account passwords posted online. However, four years later, the cyberattack has come back to haunt LinkedIn with hackers selling data belonging to 167 million users on the dark web, 177 million of which contain both email addresses and passwords protected by a weak security protocol.
The passwords were protected using the SHA1 algorithm which without salt made cracking the information easy.
LeakedSource claims to have a copy of data belonging to 167,370,910 accounts, many of which were emails and passwords only.
The website is best described as a compiler of data and is not somewhere you can find hackers for hire. Over the past few months, the group says it has acquired "hundreds" of databases through "scavenging" for stolen data across both the clear and dark web.
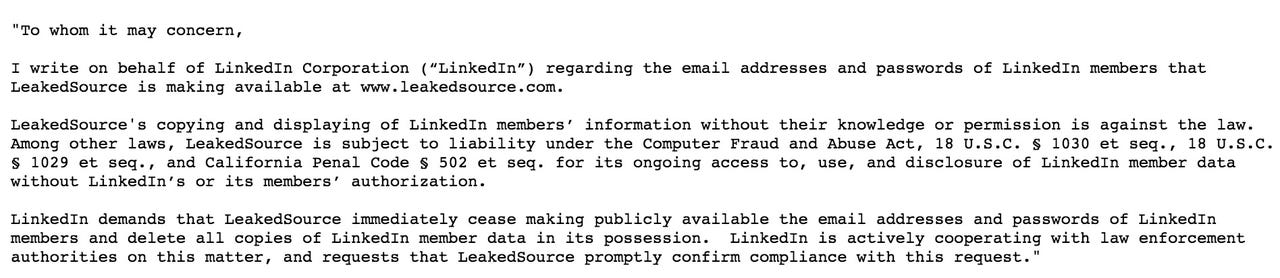
LeakedSource says it received a typical cease and desist letter from LinkedIn, revealing the exchange and commenting:
"Even though we think they're blowing steam out their ass, for the next couple of days we are going to censor hashes from that particular data set while we consult with our legal team from our jurisdiction."
The exchange is below:
While LeakedSource has chosen to remove the data for the moment, the organization took the opportunity to pick apart the professional social network's letter, noting that the group had never accessed LinkedIn or any computer without authorization, the data came from sources outside of LinkedIn, and there is no intent to defraud anyone by hosting data which has been made public.
LeakedSource works on a subscription basis for the average user, but insists another of the complaints, extortion, is unfounded.
"No extortion here, we would give you our data for free if you asked for it," the firm says.
It shouldn't come as a surprise that some of the worst passwords were "123456," "linkedin," "password" and "123456789." LinkedIn users potentially impacted by the breach have received an email informing them that there will be a forced password reset the next time they log in.