Linux ransomware rising? Linux.Encoder.1 now infects thousands of websites

Over 2,000 websites have already been compromised by the newly-discovered Linux.Encoder.1 Linux crypto-ransomware, according to a security firm.
Earlier this week Russian security company Dr Web revealed the first case of crypto-ransomware for Linux web servers, which encrypted numerous directories and file types.
At the time, the company reported that "tens" of websites were infected. However, in the past few days infections have increased to thousands, it now says.
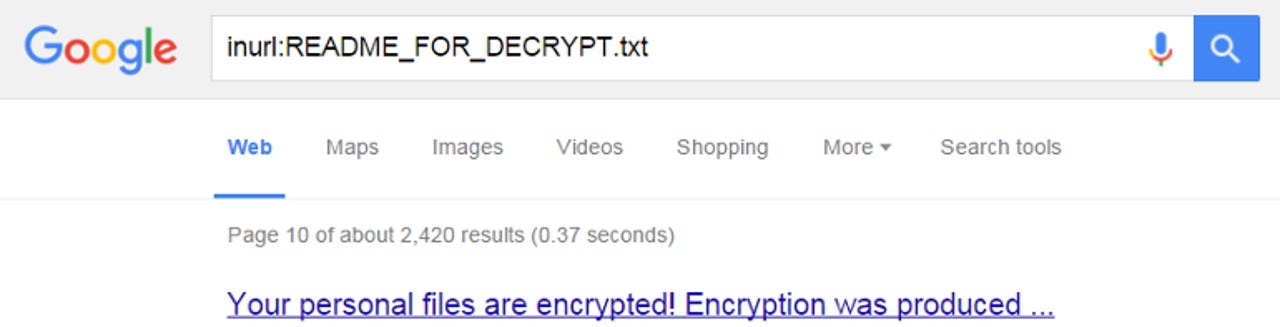
Today the company reported that about 2,000 sites have been infected by Linux.Encoder.1. The estimate is based on a Google search for the string README_FOR_DECRYPT.txt, which is the file in the malware that contains decryption instructions and the ransom demand for one Bitcoin.
Dr Web ran its query on Thursday, November 12. A search by ZDNet for the same string today returned 2,400 results, suggesting infections are climbing.
The security firm said the ransomware was infecting Linux web servers by exploiting unpatched instances of the widely-used Magento CMS.
Magento is not currently exposed to any known vulnerabilities, having released a series of patches in late October. Dr Web added today that cybercriminals distributing the Linux.Encoder.1 malware are also targeting WordPress systems.
Fortunately, the current version of the Linux ransomware is flawed, failing to generate a random private RSA key.
This slip has allowed security firm BitDefender to release a free tool to unlock the encrypted files without having to resort to payment to criminals. Dr Web also offers a tool for its paying customers.
It's still likely to be a hassle for web administrators to resolve the issue even with the free decryption tool. And it's a reminder that administrators should apply the latest patches to CMS installations.
"The attack scheme shows that cybercriminals do not actually need root privileges to compromise web servers running Linux and encrypt files. Moreover, the Trojan still poses a serious threat to internet resources owners, especially taking into account that many popular CMSes have unfixed vulnerabilities, and some webmasters either disregard the necessity of timely updates or just use outdated versions of CMSes," Dr Web noted.
The company urged admins not to pay the criminals and stressed they should not change the content of directories with encrypted files, nor delete any files from the server. It also urged its own customers to contact it for assistance.
And as Dr Web rightly points out, while this version of the ransomware contains flaws that make it easy to resolve, the criminals behind it may fix those issues in future, making it ultimately a more serious threat.