Locky ransomware is back from the dead again - with new 'Diablo' and 'Lukitus' variants

Locky is back.
One of the most successful families of ransomware has returned once again, with a new email spam campaign designed to infect victims with the file-encrypting malware.
Locky was one of the first major forms of ransomware to become globally successful and at one point was one of the most common forms of malware in its own right.
Security
However, attacks distributing Locky have declined this year, and while it was once the king of ransomware, its title has been usurped -- Cerber now dominates the market.
But that doesn't mean Locky no longer poses a threat. After going dark for a few months -- even to the point where it wasn't being distributed at all -- the ransomware is once again being spread through the Necurs botnet.
But this campaign, which began on August 9, time is being distributed with a new file extension called Diablo6, according to Malwarebytes researchers who've observed it. The new Diablo variant calls back to a different command and control server than previous Locky campaigns.
A new variant which adds the extension '.Lukitus' to encrypted files is also being distributed. Lukitus is the Finnish word for 'locking'.
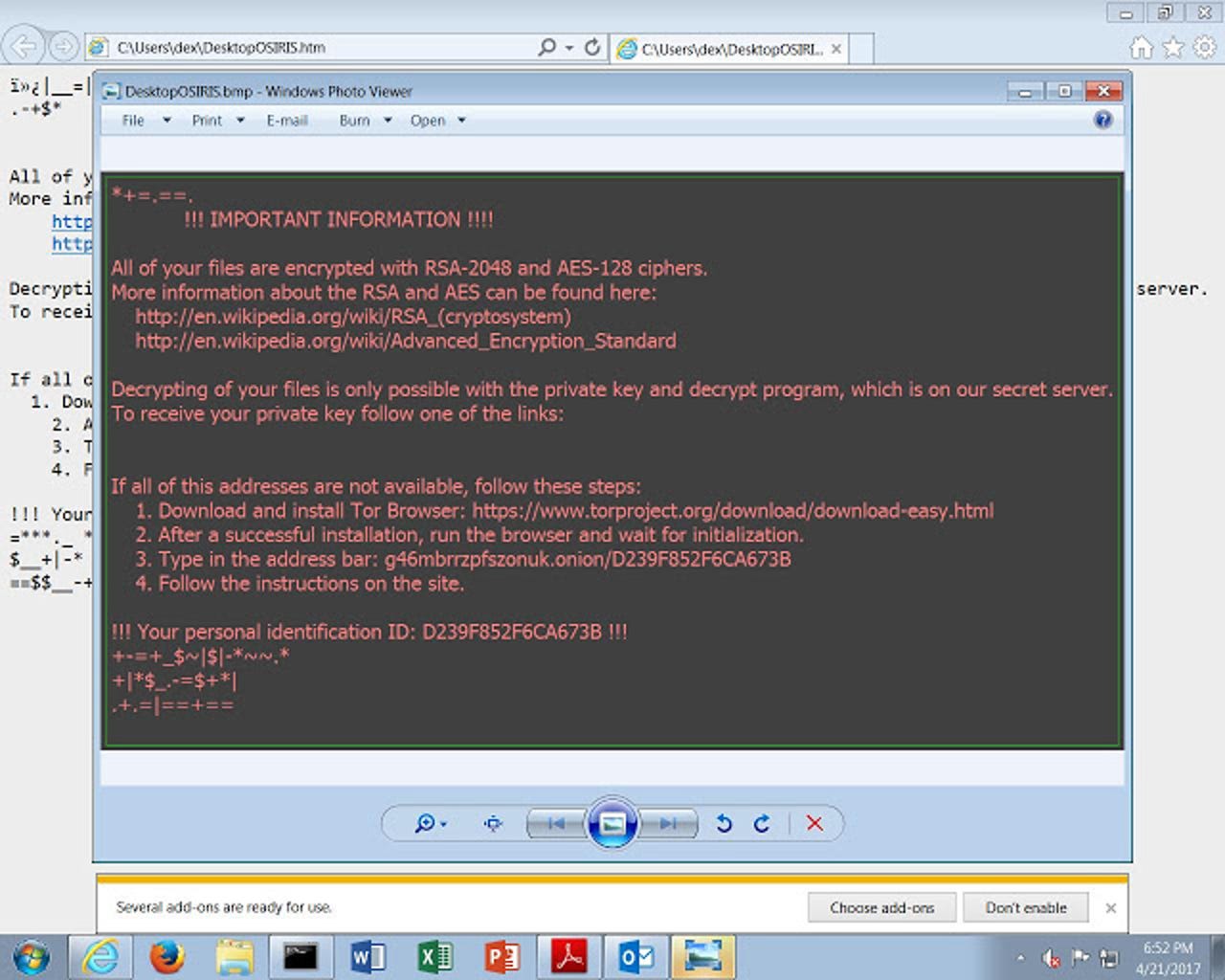
Like other ransomware families, Locky is distributed via the use of spam emails; this particular campaign sends them in the form of PDF attachments with embedded .DOCM files.
If the user downloads the attachment and enables macros as the payload requests, they'll soon find that they've lost access to the files on their computer and are told that they need to pay a ransom in order to get the "private key" from the "secret server" of the attackers.
While Locky is far less prevalent than it has been, it remains a risk to organisations because of its strong cryptography and the fact that those behind it still update and alter the payload and the tactics used to deliver it.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
"The ups and downs of Locky remain shrouded in mystery. One thing time has taught us is that we should never assume Locky is gone simply because it's not active at a particular given time," said Marcelo Rivero, intelligence analyst at Malwarebytes.
It isn't the first time Locky has reappeared after seemingly disappearing. It appeared to cease activity over Christmas 2016, leading researchers to speculate that its developers had taken a break over the holiday season. Sure enough, it re-emerged in January and infections have been spiking and dropping ever since.
The sudden reappearance of Locky could potentially be attributed to decryption tools for Jaff ransomware being made available for free in June. Jaff appeared in May and was spread by the same Necurs botnet used to distribute Locky.
Cybercriminals deploy ransomware because it allows them to reap high rewards using little effort. Therefore, it could be the case that once Jaff -- which demanded a ransom of $4,000 and used a decryptor almost identical to that of Locky -- was cracked by security professionals, the criminals behind it have simply gone back to using Locky.
While those behind Locky have yet to be identified, researchers have noted that the ransomware will delete itself from the infected machine if the local language is Russian, possibly pointing towards the geographic location of the developers.
Previous coverage
The godfather of ransomware returns: Locky is back and sneakier than ever
After a mysterious disappearance, Locky has reemerged -- and is borrowing attack techniques from Dridex.
Locky ransomware: How this malware menace evolved in just 12 months
Malware gets multiple updates as it tries to evade detection by security companies.
Locky ransomware campaign exploits fears of data stolen in OPM hack
Emails tell victims they need to download an attachment to view "suspicious activity" - then infects them with ransomware.
READ MORE ON CYBERCRIME
- Ransomware: The smart person's guide [TechRepublic]
- No more ransomware: How one website is stopping the crypto-locking crooks in their tracks
- After WannaCry, ransomware will get worse before it gets better
- Malware now comes with customer service [CNET]
- Cybercrime Inc: How hacking gangs are modeling themselves on big business