Maldrone: Malware which hijacks your personal drone

Malware is no longer limited to PCs, mobile devices, corporate networks and Internet of Things (IoT) gadgets -- your drones are now also vulnerable to hijacking.
The use of drones, also known as unmanned aerial vehicles (UAVs), has expanded into the commercial consumer sector within the past few years. Now relatively cheap to produce, tiny, personal UAVs can be purchased and used for a variety of purposes -- from advanced photography to capturing sports and spying upon Apple construction sites.
UAVs are no longer held within the domain of war, government surveillance and the like -- and now, a backdoor in popular consumer devices has been discovered which could allow hackers to hijack Parrot AR drones.
AR drones, developed by French firm Parrot, are reportedly vulnerable to hacking due to a backdoor discovered by security researcher Rahul Sasi this week. As reported by Hacker News, the AR quadcopter helicopter drone -- controllable via smartphone, tablet, Nvidia Shield console and Epson Moverio display, among others -- is vulnerable to a newly-created malware strain, dubbed Maldrone.
Featured
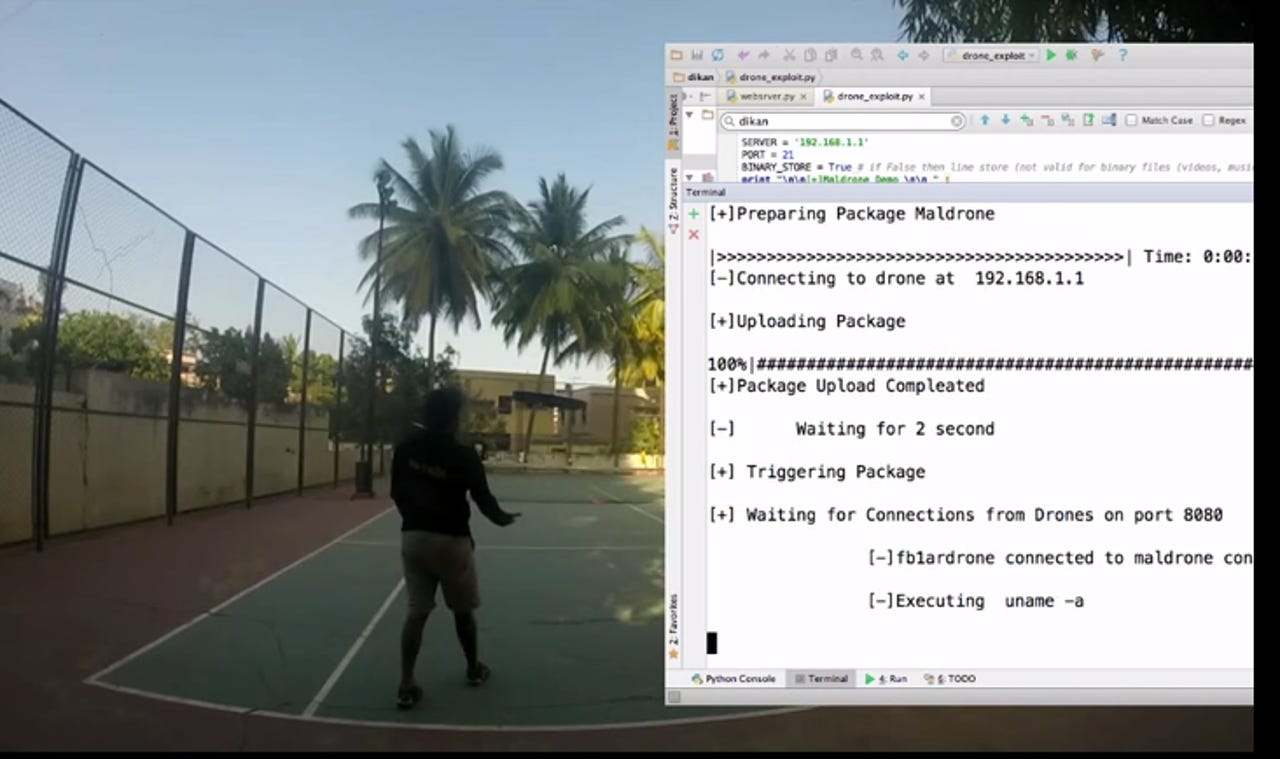
According to the researcher, Maldrone can be used to remotely hijack drones via entry through the backdoor. Developed for the AR drone's ARM Linux system, the malicious code is able to kill a drone's autopilot and take control remotely.
"In this we would show infecting a drone with Maldrone and expecting a reverse tcp connection from drone. Once connection is established we can interact with the software as well as drivers/sensors of drone directly. There is an existing AR drone piloting program. Our backdoors kills the autopilot and takes control. The Backdoor is persistent across resets."
In an educational demo video explaining the security vulnerability, Sasi says the malware is silently installed on a drone, and allows hackers to control the device remotely -- and able to conduct surveillance. The security researcher writes [spelling edited]:
"There are over 70 nations building remotely controllable drones. Most of these drones are capable of making autonomous decisions. Countries buy drones from their neighbors. What are the possibilities that there could be a backdoor in the drone you brought? What are the possible ways you can backdoor a drone? What would be the impact if security issues are found in computer devices that make decisions of their own?"
Malware isn't the only problem related to the increased use of UAVs. This week, the White House's radar system -- designed to detect threats to the presidential building such as flying objects and aircraft -- failed to detect a tiny, personal drone entering the grounds. The tiny, two-foot drone's flight ended when it crashed into the White House's lawn, according to law enforcement officials. The UAV was being operated by a government employee recreationally.
ZDNet has reached out to Parrot and will update if we hear back.
Read on: In the world of innovation
- Google hunts for self-driving car partners
- Samsung hopes to secure top spot in Internet of Things revolution
- FAA to impose restrictions on commercial drone use
- "="" rel="follow">Pentagon to sharpen tech edge with robotics, 3D printing, weaponry
- Waze unveils government data exchange program
- Google readies Android for the connected car