Malware Watch: Rogue Facebook apps, fake Amazon orders, and bogus Adobe updates
This week's Malware Watch features four campaigns, spamvertised fake Amazon orders, followed by ZeuS crimeware serving email campaign using "Adobe Security Update" as a theme, Adult content themed "Watch Video" campaign, and an overview of the "sexiest video ever" rogue application campaign, spreading across Facebook.
- Fake Amazon order emails malware campaign
This currently spamvertised campaign, attempts to trick the end user into executing the attached .zip, which when executed drops a copy of the ZeuS crimeware, next to additional malicious payload:
In the latest scam, the message appears to be an order confirmation from Amazon.com for the purchase of an expensive consumer electronics item, or a contract (spelled, tellingly, “conract“) for expensive home improvement work, purportedly to be done on the recipient’s home.
Although they've switched to a new theme, the campaign is launched by the same gang which was behind last week's "Look at my CV", and the "iTunes gift certificate" campaigns.
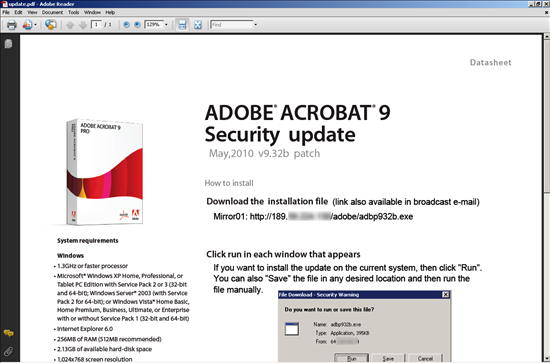
- ZeuS crimeware serving "Adobe Security Update" themed emails
Yet another spamvertised campaign, which significantly differentiates itself from the others in the sense that, the social engineering theme, as well as the actual PDF file, would look and sound pretty convincing to a potential victim.
The messages appear to be forwarded from a Director of Information Services who apparently received update instructions directly from an associate at Adobe. The message from the Adobe associate states that the update link is to patch CVE-2010-0193. There are two links in the message which lead to the same IP address hosting a PDF file for instructions and an executable which is meant to be the patch to apply.
Moreover, according to WebSense, in an attempt to avoid detection, instead of sticking to the well proven tactic of using a malicious PDF, the actual PDF file is clean from exploits, and only included the actual download link for the malware, which the gullible end user is supposed to execute manually. And with millions of users opening spam emails, and clicking on links found within, the malicious attackers will easily succeed.
- Massive Facebook rogue application campaign serving adware campaign
According to AVG, the campaign was achieving 40,000 hits per hour, demonstrating just how fast a well organized from a social engineering perspective, campaign can spread across Facebook. Although the application was shut down, the cybercriminals behind it quickly introduced a new one, once again tricking the end user into installing a bogus video player, which in reality is adware.
- Watch Video adult content themed malware campaign
This currently ongoing spam campaign, is also related to the gang behind the fake Amazon orders. The social engineering theme once again relies on the popular adult theme, offering naked videos of celebrities and related adult themed topics.
Opening spam emails, and clicking on the links within is one thing. But falling victim into a video scam that's redefining the process of video encoding, and archive compression by sending small sized .zip files, is entirely another.