Man-in-the-middle attacks demoed on 4 smartphones
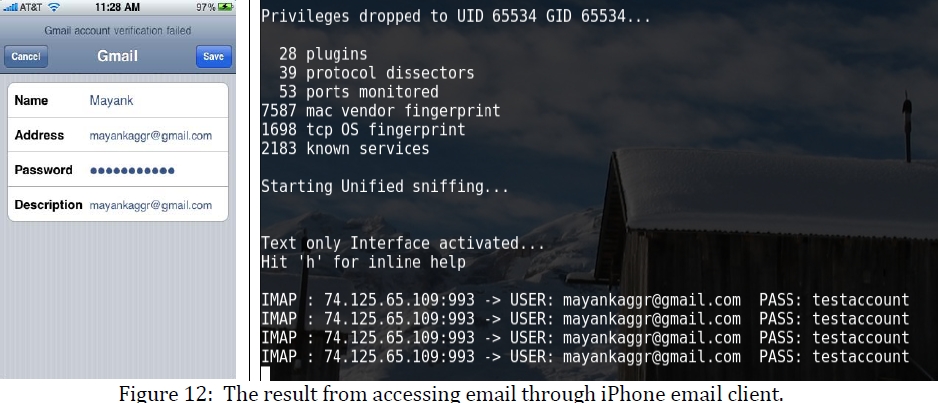
The SSL enabled log in sessions on the tested, Nokia N95, HTC Tilt, Android G1 and iPhone 3GS devices was sniffed using the publicly available SSLstrip tool, with the attack taking place over insecure Wi-Fi network, now prevalent literally everywhere.
Here's the scenario they used, and possible mitigation approaches:
"The attacker visits the same cafe that offers a free Wi-Fi hotspot and decides to employ basic host, network identification and enumeration tools from the laptop to enumerate all the active devices connected to the Wi?Fi hotspot. From the results, the attacker notices a MAC address referring to a Nokia smartphone. The attacker know that there is little to no detection capabilities present on an overwhelming majority of smartphone’s in use today, so the owner would likely never find out about a successful man-in-the-middle- attack (MITM).
The well-informed attacker creates a successful MITM attack. In the meantime, the smartphone owner accesses the online bank website and enters the login credentials required to gain access to the banking information. In this scenario, all of the communication between the smartphone and the online bank site is routed through the attacker’s machine and the attacker can see the login details in plain text, as well as can capture all the sites accessed by the victim."
Anyway, just how insecure or susceptible to compromise are the majority of Wi-Fi networks found on high-trafficked locations such as airports or international cities? The answer is sadly, self-evident with data backing it up available publicly.
- Go through related posts: GPU-Accelerated Wi-Fi password cracking goes mainstream; D-Link router's CAPTCHA flawed, WPA passphrase retrieved; Survey: 88% of Mumbai's wireless networks easy to compromise
Last year, AirTight Networks conducted a major wireless network security study by visiting 14 airports (11 in
The prevalence of such "handy", but easy to compromise Wi-Fi networks internationally, is virtually the same. For instance, similar wardriving tests conducted in Paris; Santiago, Chile; China; Monterrey — Mexico, Sao Paulo – Brazil, Caracas (Venezuela), Warsaw, and London offer similar insights into the "security" of such public networks.
Possible mitigation practices? According to Marlinspike, the author of the tool:
"Cautious users, for example, have been advised to explicitly visit https URLs or to use bookmarks in order to protect themselves from sslstrip, while other SSL/TLS based protocols such as imaps, pop3s, smtps, ssl/irc, and SSL-based VPNs never present an opportunity for stripping. This talk will outline some new tools and tricks aimed at these points of communication, ultimately providing highly effective attacks on SSL/TLS connections themselves."
How often do you face the trade-off of using a public, and possible insecure Wi-Fi hotspot, for the sake of convenience instead of sticking to your 3G data plan, even when traveling abroad?
Have you ever avoided using your mobile device and instead used your laptop at an airport, due to your host-based firewall's better ARP filtering features -- if any -- enabling the detecting of changed MAC address for a (trusted) gateway network adapter in order to detect possible MItM attempts?
How EV SSL-aware is your E-banking provider, especially if you're E-banking over a mobile device? Or do you simply "VPN-and-forget" over a public Wi-Fi network?
TalkBack.