Microsoft disables AutoRun on Windows XP/Vista to prevent malware infections
With hundreds of thousands users still running Windows XP despite the security considerations of doing so, in a largely anticipated move by the security community, Microsoft has decided to disable the AutoRun feature on Windows XP. The "non-security update" doesn't affect shiny media" such as CDs or DVDs that contain Autorun files, and is targeting other removable media.
The move aims to limit the number of AutoRun infections, with the feature itself now an inseparable part of every modern and modular malware bot.
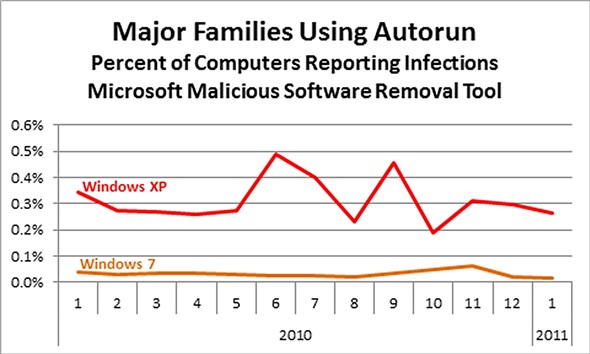
According to Microsoft's data, Win32/Autorun remains within the most popular malware families, with Windows XP users more likely to experience such an infection, compared to Windows 7 users.
A similarity all of these worms share is a common propagation method. They all abuse the autoplay feature of Autorun, many by creating or manipulating Autorun.inf files on network drives and removable media, so that when a user connects, the malware is automatically executed on their system. On average in 2010, about 9% of Windows 7 Security Essentials users reported seeing one of these families at least once per month in comparison to 13% of Windows XP users. In other words, a Windows XP user was 43% more likely to report one of these Autorun detections in any given month in comparison to a Windows 7 user..
Should Linux users worry about AutoRun infections? From theory into practice a security researcher has recently demonstrated a similar scenario, where the AutoRun functionality is successfully exploited on Linux host.
Why do you think so many users are still running Windows XP? What about the millions of users who would not receive this update taking into consideration the fact that they're running pirated Windows software, whose least worry are AuroRun infections?
Talkback.