Microsoft Office malware: Banking trojan downloads if you hover over PowerPoint hyperlink

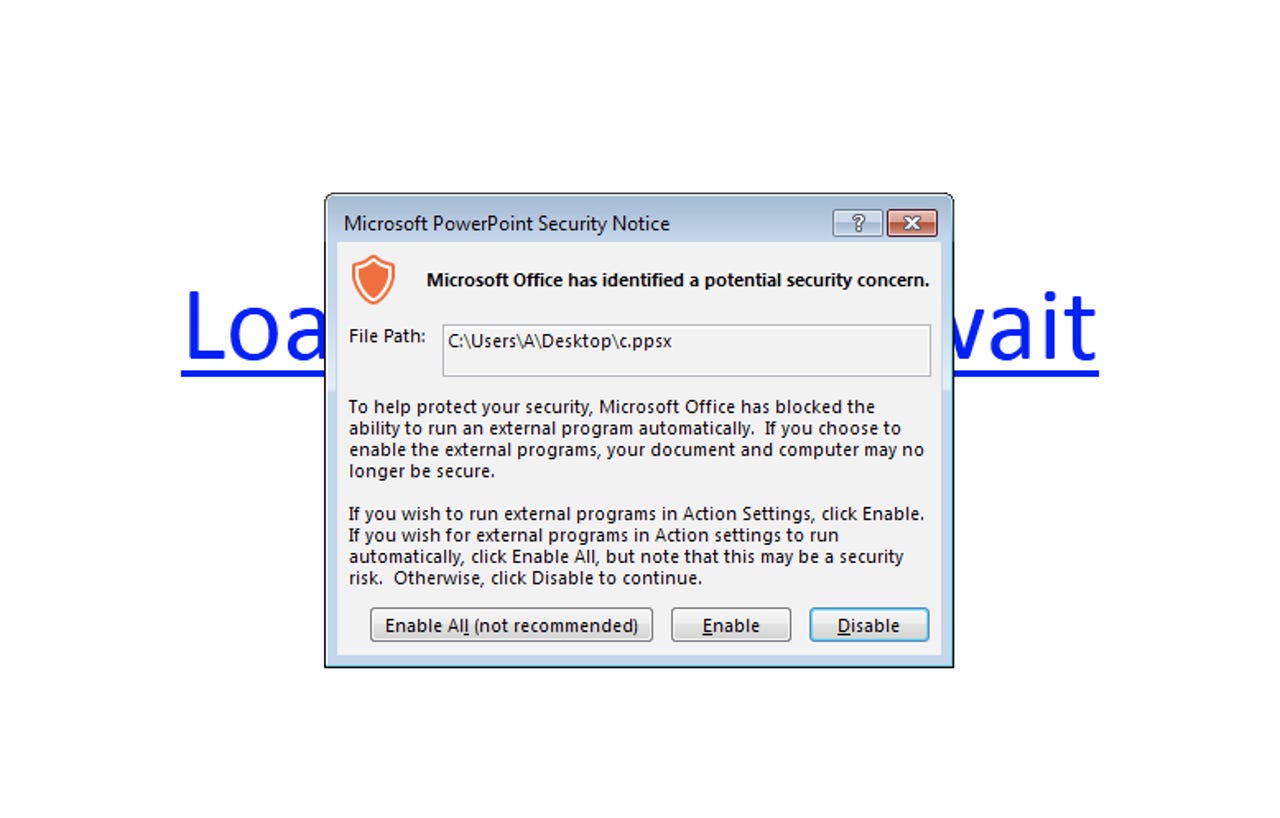
Ignore this warning from Microsoft at your peril.
Spammers are testing a new way to trick victims into installing malware that downloads after the user hovers over a link in a PowerPoint slide show.
The new infection method adds a twist to the common advice not to click on links from suspicious sources and evolves the Office macro malware threat that re-emerged in 2015, which tricks email recipients into running a malicious macro, or a script, that downloads and installs malware.
BleepingComputer recently discovered the new twist on Office malware, which doesn't require macros, but rather abuses a hover action in PowerPoint slide show mode to install malware. If the recipient opens the PowerPoint file and hovers over hyperlinked text in the document, it will run a PowerShell command that connects to a malicious domain and downloads malware files.
The malware is delivered as spam email with subject headers and attachment file names that suggest an invoice or purchase order. The attached file formats are the open-source version of Microsoft PowerPoint slide show (PPSX), which are only for viewing, and can't be edited like normal PPT or PPTX files.
The PPSX examples seen so far display the hyperlinked text "Loading... Please wait". Hovering over it will download malware automatically unless Office Protected View is enabled. Fortunately, Protected View was enabled by default in Office 2010, in which case Office displays a security warning that blocks the download.
The PowerPoint file downloads a banking trojan it calls Gootkit or Otlard. SentinalOne calls the malware Zusy.
Trend Micro detected a spam campaign with the malicious PowerPoint files in late May aimed mostly at organizations in the UK, Poland, Netherlands, and Sweden. The gang behind this spam has previously used macro malware documents to deliver different payloads.
The current campaign was not widespread, but Trend Micro researchers believed it is a "dry run for future campaigns", which may include a ransomware payload.
"While features like macros, OLEs, and mouse hovers do have their good and legitimate uses, this technique is potent in the wrong hands. A socially engineered email and mouse hover -- and possibly a click if the latter is disabled -- are all it would take to infect the victim," wrote Trend Micro.
More on security
- Linux server attack: Patch Samba or risk cryptocurrency mining malware
- Want ransomware-proof Windows? It won't work against Windows 10 S, claims Microsoft
- This Android malware features a 'dangerous' new attack
- Microsoft buys security-automation vendor Hexadite
- Windows firewall dodged by 'hot-patching' spies using Intel AMT, says Microsoft