Microsoft Patent App would add "trust system" to some cut-and-paste operations

There's a newly published Microsoft Patent application that - at least the way I read it- seems to both alter and add significant options to the way in which cut-and-paste is performed between various Windows-compatible documents and utilities.
That's not to say you will have to reprogram your brain to c&p from say, Word into a PowerPoint presentation. That's not going to need to happen.
Instead, the concept here seems to be that Microsoft is saying that under-the-hood coding can make cut-and-paste a messy affair- and here are some solutions for these issues.
The specific solutions described in this Patent app offer various "trust levels" for objects that can be cut and pasted. Examples would be secured documents that might need varied rules for what ought to be cut-and-pasteable.
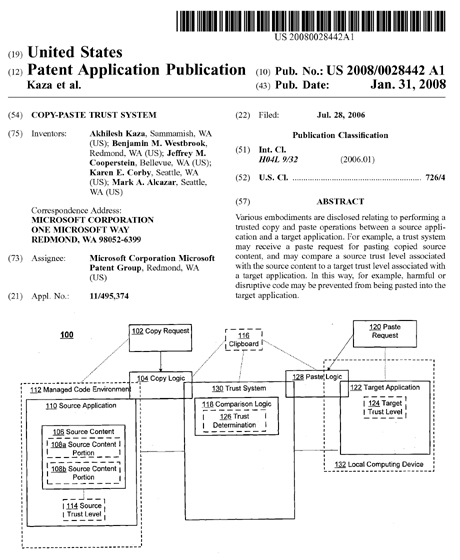
The Patent Application we're going to look at here is entitled, Copy-paste Trust System.
The Abstract gives us a sample of what's being proposed:
Various embodiments are disclosed relating to performing a trusted copy and paste operations between a source application and a target application. For example, a trust system may receive a paste request for pasting copied source content, and may compare a source trust level associated with the source content to a target trust level associated with a target application. In this way, for example, harmful or disruptive code may be prevented from being pasted into the target application.
For a deeper understanding of the issue, I am going to show you Figures 2 and 3 from the Patent App, as well as its accompanying documentation.
FIG. 2 is a flow chart 200 illustrating example operations of the system 100 of FIG. 1. In the example of FIG. 2, source content associated with a source application is determined in response to a copy request (210), wherein the source content includes one or more source content portions.
For example, as referenced above, a user may decide to copy content from the source application 110. Thus, upon receiving the copy request 102, copy logic 104 may copy source content 106, including source content portions 108a,b, from source application 110, and store this information on the clipboard 116.
The source content may be associated with a source trust level, and this source trust level may be determined (220). For example, source content 106 may be associated with source trust level 114.
When copy logic 104 copies source content 106 to clipboard 116, copy logic 104 may also store source trust level 114 in association with source content 106 on clipboard 116. In an example embodiment, source trust level 114 may be stored as a private data member on clipboard 116.
A paste request may then be received, the paste request associated with a target application (225). For example, a user of the target application 122 may initiate the paste request 120, using one of the techniques described above.
A target trust level may then be determined (230). For example, after a user selects source content 106 to copy, the user may attempt to paste the source content 106 to a target application 122.
Consequently a paste request 120 associated with the target application 122 may be received by trust system 130, as just described. Then, for example, comparison logic 118 may determine the target trust level 124 associated with the target application 122 associated with the paste request 120.
In an alternative embodiment, a user may drag source content 106 from source application 110 and may try to drop the source content 106 into target application 122, thus also generating paste request 120.
After determining a target trust level, a trust determination may be made based on the target trust level and the source trust level (240). For example, comparison logic 118 may retrieve the source trust level 114 from clipboard 116 and compare source trust level 114 to target trust level 124 to make trust determination 126, as described above.
Based on the trust determination, a first source content portion of the one or more source content portions associated with the source content may be determined. For example, paste logic 128 may determine which source content portion 108a or 108b is safe for providing to target application 122, based on trust determination 126.
Finally, the first source content portion of the source content may be provided to a target application (260). For example, paste logic 128 may select source content portion 108a and then may paste source content portion 108a of source content 106 into target application 122.
Now, let us go to Figure 3 and its corresponding literature.
FIG. 3 is an example embodiment of the system 100 of FIG. 1 in a managed code environment 322. In the example of FIG. 3, the copy request 102 may be received by the trust system 130a, where the trust system 130a is representing a variation of the trust system 130 of FIG. 1.
Specifically, in the trust system 130a, the comparison logic 118 is included in the trust system 130a, but the copy logic 104 is included in an internet application 308, while the paste logic 128 is included in a word processing application 320, as shown.
By distributing the various components in this manner, the trust system 130 may have wide applicability and be available to a large number of users, and may operate in a redundant and reliable manner.
The copy request 102 may include a user selecting content from a source application 308, such as an internet application of the managed code environment, and copying the selected content for later pasting to a target application, as described above with reference to FIG. 1.
As also referenced above, the copy request 102 may include included as part of a drag-and-drop request. For example, a user may select text from a first document of the internet application 308, and drag the text to a word processing application 320 to be dropped. In an example embodiment, the drag-and-drop request may include the copy request 102 and the paste request 120.
For example, the copy request 102 may include a request to copy selected information from the source application 308. Then, for example, the paste request 120 may include a request to paste (i.e. drop) the selected content into the target application 320.
As discussed above, the trust system 130a may be aware of the copy request 102. For example, the trust system 130a may receive the copy request 102, and determine which content is to be copied, receive the paste request 120, make a trust determination based on the source content and target application, and then paste the source content, based on the trust determination.
In FIG. 3, the copy logic 104 may handle the copy request 102. For example, the copy request 102 may include a request to copy a document 306 from the internet application 308.
The copy logic 104 may then copy the document 306, including any document portions 310a,b and a source trust level 312, from the internet application 308, or from an application domain 321 associated therewith.
The internet application 308 may include a program, code, applet, website, or other application associated with the internet that may provide content configured to be cut, copied and/or dragged-and-dropped. For example, the internet application 308 could be an internet website providing a document 306, or portion thereof, that may be copied or dragged-and-dropped by a user.
The document 306, for example, may be a document containing text 312 and active code 314. The document 306 may also include one or more document portions 310a,b. A document portion 310a,b may be at least a partial representation of the document 306.
A document portion 310a,b may assume a level of fidelity of the document 306. For example, the document 306 as requested to be copied by the copy request 102 may contain both text 312 and active code 314. Then, for example, the document 306 may include the two document portions 310a,b.
Document portion 310a may assume a high fidelity of the document 306, and may include both the text 312 and active code 314 of the document 306. Document portion 310b may assume a lower fidelity of the document 306 and may include only the text 312 of the document 306.
In another embodiment, a document portion 310a,b may include one or more formats of how document 306 may be stored on internet application 308.
For example, if document 306 contained only text 312, then document portion 310a may include the text 312 in a rich text format (RTF), while document portion 310 may include the text 312 in a Unicode text format.
The active code 314 may be a set of code of the document 306 configured to perform an action and/or function. For example, the active code 314 could be a link to another website, or perhaps an object that if instantiated may reformat a user's local machine. In an example embodiment, the active code 314 may include eXtensible Markup Application Language (XAML) code.
XAML code generally refers to code based on the eXtensible Markup Language (XML), and that is used to support graphics-intensive environments. The XAML code, for example, may create and instantiate a live object on a target application, such as the word processing application 320, when copied and pasted thereto.
For example, the active code 314 may create and instantiate an object, perhaps represented to the user as a button or other visual element, that may reformat a hard drive.
]The document 306 may also be associated with a source trust level 114. The source trust level 114, as discussed above, may be a measure of the level of trust associated with the document 306. Alternatively or additionally, the source trust level 114 may be associated either directly or indirectly with a source application 308 of the document 306, with one or more document portions 310a,b, or with a user.
For example, if internet application 308 was a Microsoft application, then for example all Microsoftapplications may be fully trusted and associated with the highest source trust level 114. In another example, perhaps a user is a guest user of the system 300, the user may always be associated with the lowest trust level 114.
Also as discussed above, the source trust level 114 may be a value on a possible range of trust values, may be a set of allowed functions, and/or may be any other applicable measure of trust.
In the example of FIG. 3, the internet application 308 is associated with an application domain 321, which is associated with the source trust level. The application domain 321 refers to an object and/or process that is associated with an application, e.g., the internet application 308, and that is stored and that contains information about its associated application(s).
Thus, the application domain provides a convenient technique for associating a (source) trust level with the source application 308, since, e.g., the copy logic 104 may simply store the copied content (e.g., document 306) to the clipboard 316 and may obtain and store the source trust level from the application domain 321, as shown.
Thus, the source trust level 114 is associated with the source content 306, inasmuch as the source content is part of the source application 308 and therefore part of the application domain 321. Moreover, the target application 320 also may be associated with the application domain 321, or with a different (i.e., its own) application domain.
As shown in FIG. 3, some or all of the trust system 130a may be implemented on, or in conjunction with, the clipboard 316.
In this way, for example, the trust system 130a may easily receive and respond to the paste request 120 by populating the private data member 318 with the source trust level 114 (and/or the source content portions 310a, 310b).
Thus, upon receiving the drag-and-drop 302 request, the copy logic 104 may copy document portions 310a,b and source trust level 114 from internet application 308 and application domain 321, respectively, and store this information on the clipboard 316.
The copy logic 104, as discussed above, may also store additional information on the clipboard 316 as well, for example, the name of the source of the document 306, user information, and or any other accessible information.
As discussed above, the clipboard 316 may be a memory unit configured to store information relating to the system 300. As will be appreciated, the clipboard 316 may have associated application program interfaces (APIs) that are used (e.g., by corresponding APIs of the source application, target application, and/or trust system 130a) to call into, and provide data out from, the clipboard 316.
Thus, for example, the clipboard 316 may store document portions 310a,b. The clipboard 316 may also store the source trust level 114 as a private data member 318. The private data member 318 may be a memory unit associated with the clipboard that may not be accessible to systems and/or programs outside of trust system 130a.
For example, if the source trust level 114 has been stored on the private data member 318 of the clipboard 316, then for example a user may not be able to access the source trust level 114.
For example, the user may paste document portion 108b to a target application (that is stored outside of private data member 318), but not source trust level 114 that is stored inside private data member 318.
After the copy logic 104 stores the information associated with the copy request 102 on the clipboard 116, the paste request 120 may cause the comparison logic 118 of the trust system 130a to make a trust determination 126.
As discussed above, upon receiving the paste request 120, the comparison logic 118 may make a determination as to the trustworthiness of the document 306 based on the source trust level 114 and a target trust level 124 for the target application 320.
For example, the comparison logic 118 may retrieve the source trust level 114 from the clipboard 116 and the target trust level 124 from the target application 320 (which in this example may be a word processing application, as shown).
As discussed above, the comparison logic 118 may compare the source trust level 114 to the target trust level 124 to make a trust determination 126. The trust determination 126, as discussed above, may be a determination as to the safety or trustworthiness of the document 306 to be copied (or cut) and pasted.
The trust determination 126, for example may include a value of trust amongst a range of possible values, may include a set of allowable content, a function for determining trust, or may include any other acceptable measure of trust.
In some example embodiments, all applications within the managed code environment 322 may be assigned a trust level, such as "no trust," "partial trust," or "full trust." In this way, the trust system 130a may make fast trust determinations within the managed code environment 322.
In another example embodiment, if two or more portions of document 306 are deemed safe based on the trust determination 126, then the paste logic 128 may select the document portion that assumes the highest fidelity.
For example, if trust determination 126 indicates that both the text 312 and active code 314 from the internet application 308 may be safely pasted, then both document portion 310a and document portion 310b may be safely pasted.
As such, the paste logic 128 may select document portion 310a for pasting, as document portion 310a may assume a higher fidelity in including both text 312 and active code 314.
As discussed above, the paste logic 128 may then select a document portion 108a,b to paste to the word processing application 320 based on the trust determination 126. The paste logic 128 may be configured to select and paste a portion of the document 306 to the word processing application 320, based on the trust determination 126.
For example, trust determination 126 may indicate that only the text 312 may be safely pasted from document 306 to word processing application 320. Then for example, the paste logic 128 may select document portion 310b from the clipboard 116 to be pasted, as document portion 310b contains only text 312 while document portion 108a contains both text 312 and active code 314.
While the paste logic 128 may select a document portion 310a,b to paste based on the trust determination 126, a user may choose to override the selection.
As discussed above, the paste logic 128 may be configured to allow a user to override a selection of a portion of the document 306 based on the trust determination 126. For example, paste logic 128 may select document portion 310b as being safe because trust determination 126 may indicate that the active code 314 is unsafe.
A user, however, may decide the user still wants the active code 314 despite the trust system's determination of being unsafe, and, as such, the user may override the selection of document portion 310b, in favor of document portion 310a.
The paste logic 128 may then paste the selected document portion 310a,b (either selected based on the trust determination 126 or by a user override) to the word processing application 320.
The word processing application 320 may be any word processing application configured to accept a paste of at least a portion of the document 306. For example, the word processing application 320 may be configured to accept text 312 and/or active code 314 content.
Trust system 130a, clipboard 316, and word processing application 320 may all be within the managed code environment 322, as shown. As discussed above, a managed code environment may automatically handle program and/or memory management.
The managed code environment 112 may also, for example, support any programming language that is managed code compliant and provide a unified programming model to write applications using managed code.
For example, a managed code environment 322, such as Avalon.TM., may support C#, C++ or any other programming language(s) that may be managed code compliant. Also an application within the managed code environment 322 may have permissions an application outside the managed code environment 322 does not.
For example, as discussed above, the word processing application 320 may be able to override the trust system 130a determination that document portion 310a is unsafe and paste document portion 310a regardless of the trust determination 126, while an application outside of the managed code environment 322 may not have such permission, or may not be allowed to use the trust system 130a at all.
Bet you didn't think cut-and-paste could have all those layers of complexity.