Microsoft to ratchet IE8 security another notch in Beta 2

Sometime in August, Microsoft plans to release Beta 2 of Internet Explorer 8. Yesterday, I spoke with Austin Wilson, Director of Windows Client Product Management at Microsoft, about some of the security-related changes due in this milestone, and got a preview of the changes announced today.
The most noticeable change is the SmartScreen Filter, which replaces the Phishing Filter found in IE7. It uses the same reputation-based filter as its predecessor, but adds a few tweaks to make it easier to spot social engineering attempts. IE8 adds domain highlighting (as shown below) to frustrate phishing attempts that use long, complex URLs to make a link appear to go to a legitimate domain.
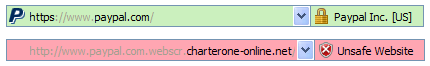
Part of the work involves simplifying the interface for displaying potentially dangerous websites. In IE7, for example, the address bar turns yellow when you encounter a suspicious site and red when you attempt to visit a site that is reported as unsafe. In IE8 the yellow bar is gone, replaced by a dialog box. The green address bar for sites that use Extended Validation certificates remains.
When you try to visit a site that is listed in the database of known unsafe sites, the background of the browser window turns blood red and this stern warning appears:
The SmartScreen filter in IE8 also extends protection to download attempts, blocking access to servers that are known to be serving up malware
The concepts behind that work should be familiar to anyone who's used a competing browser, such as the just-released Firefox 3. Corporate customers and security professionals should be more interested in architectural changes designed to block access to vulnerabilities in ActiveX controls and take advantage of Data Execution Prevention features.
The ActiveX changes (some of which were announced in May) allow controls to be locked to a specific site and to be offered on a per-user basis. The former prevents a hostile website from being able to call an existing ActiveX control (such as one installed by the system builder or with another program, or one downloaded from a different, presumably safe web page). The user (or a system administrator, using group policy) has to opt-in to those controls and can lock them for use only on a specific site.
ActiveX controls can also be offered on a per-user basis, bypassing the need for UAC prompts and lessening the possibility that one user can install a control that compromises the entire system or other user accounts.
In IE7, Data Execution Protection is disabled for the browser process by default, primarily for compatibility reasons. IE8 enables DEP on Windows Vista SP1, Windows XP SP3, and Windows Server 2008. As a result, any page or add-in that tries to use a buffer overflow or other exploit to write executable code to an area of memory that is reserved for data will crash that browser tab (but shouldn’t take down other tabs).
Finally, IE8 is designed to protect from some forms of server-based attacks as well. The most noteworthy change is code that blocks common forms of cross-site scripting exploits. According to Wilson, IE8 will detect Type-1 (reflection) attacks and block script from being injected to web a server via URL.
I’ll have a more detailed look at these changes when the beta code is available next month.