New ransomware variants spotted in the wild
Security researchers from TrendMicro, F-Secure and Dr. Web have intercepted two new ransomware variants currently circulating in the wild.
TrendMicro intercepted a new ransomware variant that compared to previous releases is infecting the Master Boot Record (MBR), thus, preventing the operating system from loading. Upon execution, the infected PC restarts and displays the ransom message requesting a payment in order for them to receive the unlock code.
Both F-Secure and Dr.Web have intercepted an identical ransomware variant. Upon execution it encrypts all files, by adding a .EnCiPhErEd file extension. End users are given the option to have 5 attempts to try and enter the unlock code, in between the malware deletes itself and leaves the files encrypted.
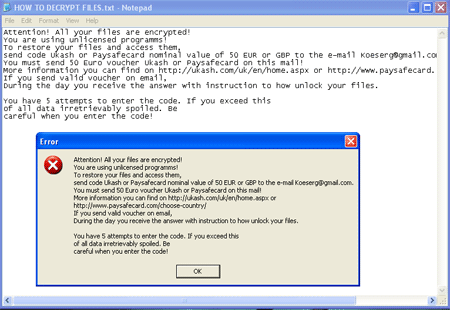
The ransomware displays the following message to infected users:
Attention! All your files are encrypted! You are using unlicensed programms! To restore your files and access them, send code Ukrash or Paysafecard nominal value of EUR 50 to the email koeserg@gmail.com. You have 5 attempts to enter the code. If you exceed this of all data irretrievably spoiled. Be careful when you enter teh code!
Moreover, the vendors are emphasizing on the fact that the encryption in the ransomware variants (SHA1: b8f60c64c70f03c263bf9e9261aa157a73864aaf) is not as strong as the encryption used in previous versions of the infamous GPCode.
See related posts:
- Localized ransomware variants impersonate law enforcement agencies
- Microsoft themed ransomware variant spotted in the wild
- Copyright violation alert ransomware in the wild
- New ransomware variant uses false child porn accusations
- Mac OS X SMS ransomware - hype or real threat?
- Who's behind the GPcode ransomware?
Ransomware attacks are becoming increasingly prevalent across multiple countries, thanks to the added localization and better market segmentation of the prospective victims. Cybercriminals taking into consideration quality assurance as a process, and constantly looking for new ways to socially engineer end and corporate users into infecting themselves with ransomware variants.
End users are advised to avoid interacting with suspicious links found in spam emails, and t o ensure that they're running the latest version of their third-party software, and browser plugins.