OpenDNSSEC to the rescue

Trouble is BIND is insecure. As security expert Dan Kaminsky discovered in 2008 the cache can be poisoned, people redirected to malware sites.
So do you go with something proprietary, like Skye? You could, but there is another option, OpenDNSSEC, which hit Version 1.0 this week.
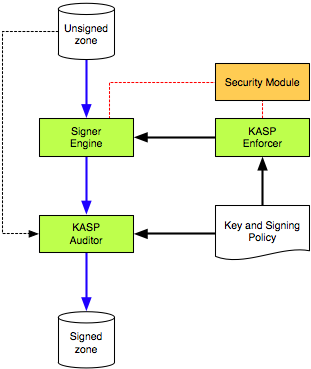
OpenDNSSEC adds digital signatures to DNS requests before they are acted upon. It's still not perfect. Until standards are developed you need to connect with your parent zone registrar periodically to assure security.
But it's a lot better than nothing. Nothing is, unfortunately, what a lot of sites are offering.
The release of a working version of OpenDNSSEC gives the open source process another shot at getting DNS right. Big companies are earning big money keeping customers' DNS secure. If you are a big company such protection will look cheap.
If you are not a big company, however, you may not be able to afford that kind of security. The fact so many companies can't afford it also helps the bad guys.
Like everyone else I don't know everything, and I do make mistakes. But I try to fix my mistakes and when I don't know something I know who to call, or how to find who to call.
OpenDNSSEC should be on every good security manager's bookmarks.