Phishing remains a data breach weapon of choice, says Verizon

Eighty-nine percent of the data breaches tracked by Verizon were either financially or espionage motivated and conducted within minutes courtesy of phishing and stolen credentials.
Those are some of the key takeaways from Verizon's 2016 Data Breach Investigations Report (DBIR), which analyzed 100,000 incidents of which 2,260 were confirmed data breaches.
Verizon's 2016 DBIR doesn't veer much from the findings from the previous year. Accommodation, retail and financial services remain big topics. "It was a bad year for hospitality," said Bryan Sartin, one of the authors of the report. Point-of-sale breaches were common and Web app breaches took the baton from crimeware. Sartin, however, noted that the decline in crimeware was largely due to better classification.
One stunning item in the DBIR is how effective phishing attacks remain.
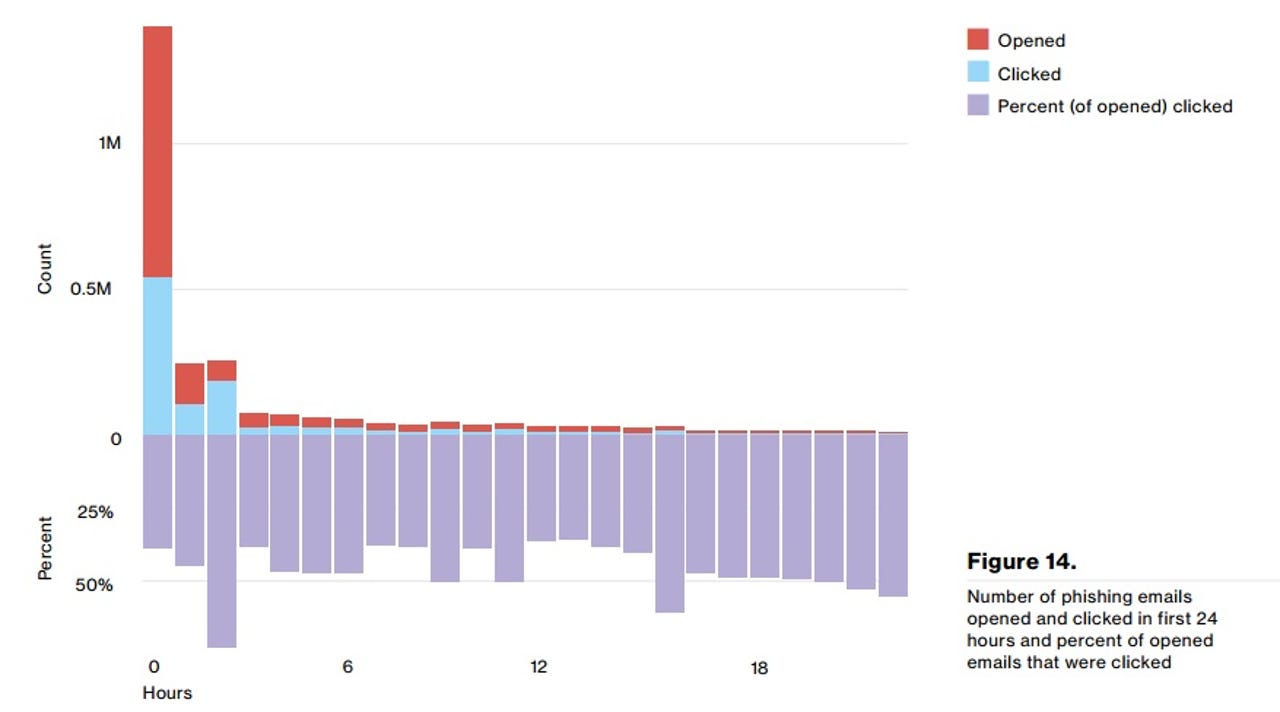
Verizon said in its report:
Apparently, the communication between the criminal and the victim is much more effective than the communication between employees and security staff. We combined over eight million results of sanctioned phishing tests in 2015 from multiple security awareness vendors aiming to fix just that. In this year's dataset, 30% of phishing messages were opened by the target across all campaigns.10 "But wait, there's more!" (in our best infomercial voice) About 12% went on to click the malicious attachment or link and thus enabled the attack to succeed. That indicates a significant rise from last year's report in the number of folks who opened the email (23% in the 2014 dataset) and a minimal increase in the number who clicked on the attachment (11% in the 2014 dataset). The median time for the first user of a phishing campaign to open the malicious email is 1 minute, 40 seconds.
Another tidbit is how phishing fits into a larger pattern of stealing credentials.
Here's a look at the time to compromise and time for an attacker to bail.
Meanwhile, law enforcement is finding more breaches along with third party providers.