Photobucket's DNS records hijacked by Turkish hacking group
Yesterday, Photobucket the world's most popular photo sharing site according to Hitwise had its DNS records hijacked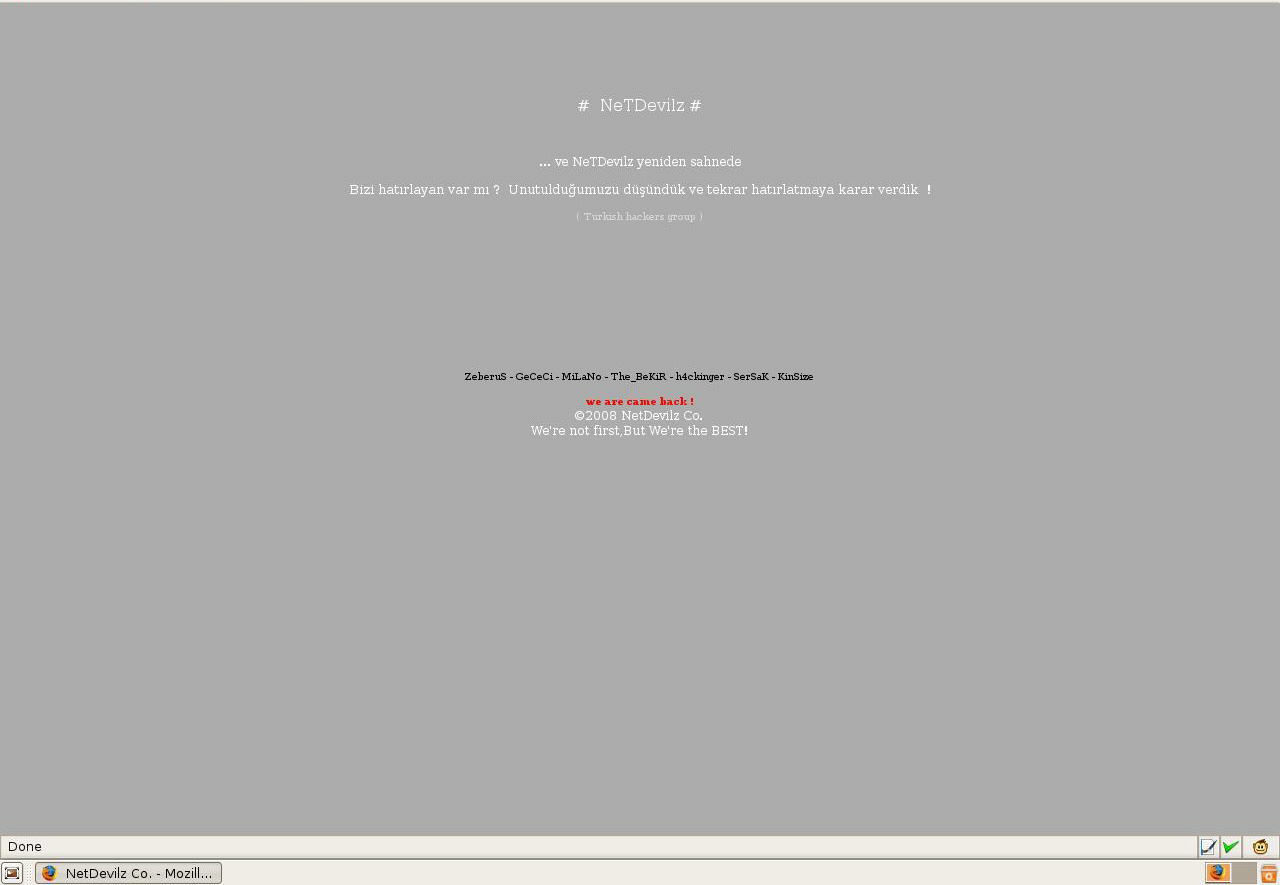
Third-party site monitoring services indicate that the site was down for 15 minutes yesterday, from from 17:39:39 to 17:55:10, whereas according to a comment left by a Photobucket Forum Support representative, the downtime due to the propagation of the corrected DNS entries was longer :
"On Tuesday afternoon, some users that typed in the Photobucket.com URL were temporarily redirected to an incorrect page due to an error in our DNS hosting services. The error was fixed within an hour of its discovery, but due to the nature of the problem, some users will not have access to Photobucket for a few hours as the fix rolls out. It is important to note that only a portion of Photobucket users encountered the problem and that no Photobucket content, password information or other personal information was affected by the redirect."
The NetDevilz hacking group left the following message, that appears to have been loading from a third-party domain,
"... ve NeTDevilz yeniden sahnede
Bizi hat?rlayan var m? ? Unutuldu?umuzu dü?ündük ve tekrar hat?rlatmaya karar verdik ! ( Turkish hackers group )
ZeberuS - GeCeCi - MiLaNo - The_BeKiR - h4ckinger - SerSaK - KinSize
we are came back ! ©2008 NetDevilz Co. We're not first,But We're the BEST!"
The hacking group appears to have been using the hosting services of atspace.com, the web hosting service of Zetta hosting solutions, and users of Photobucket attempting to access the site with the old DNS entries are still being redirected to a default hosting ad page within atspace.com. The effect of the redirection can also be seen by taking a peek at the publicly obtainable stats for atspace.com, where the sudden peak in traffic resulting in 118,864 visitors for today came from the default ad page used in the redirection.
With the second DNS hijacking attack against a high-profile domain in the recent months, it seems that adaptive malicious parties unable to directly compromise a site will continue taking advantage of good old-fashioned DNS hijacking. At least to prove that it's still possible even on a high-profile domain using the services of a Tier 1 domain registrar.