Ransomware attack: The hunt for the hackers begins

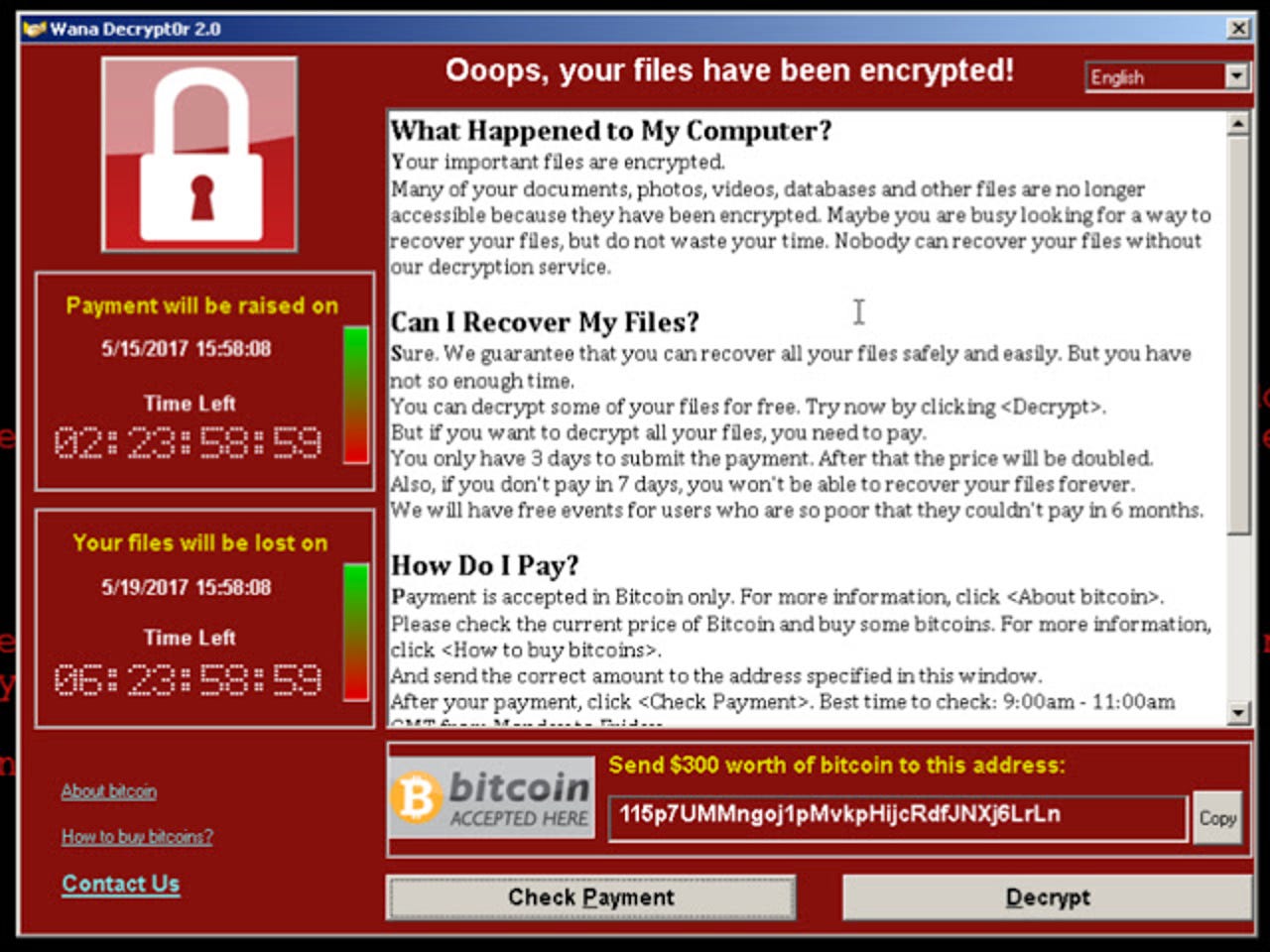
WannaCry ransomware has infected Windows XP systems across the globe.
Authorities are on the hunt for those behind the Wannacry ransomware -- the largest ransomware attack there's ever been.
Organisations across the globe were crippled by a ransomware attack which claimed more than 200,000 victims in over 150 countries, including the UK's National Health Service and businesses and government institutions in Russia, China and the US.
PCs which become infected by the ransomware are locked and users are issued with a ransom $300 in Bitcoin for unencrypting their files. That doubles to $600 if the demand isn't met within three days and if a week goes by without payment the victims are threatened that their files could be deleted forever.
While organisations are slowly returning to normal in the aftermath of the weekend's attacks, investigators and law enforcement are looking into the attack in an effort to identify the perpetrators.
"We're trawling through huge amounts of data associated with the attack and identifying patterns," said Lynne Owens, Director General of the National Crime Agency, the UK's organised crime fighting taskforce.
The NCA is working alongside international law enforcement partners including Europol, Interpol and the FBI to investigate the attacks.
"We are actively sharing information related to this event and stand ready to lend technical support and assistance as needed to our partners, both in the United States and internationally. DHS has a cadre of cybersecurity professionals that can provide expertise and support to critical infrastructure entities," the Department of Homeland Security said in a statement.
But the sheer number of infections across the globe and the fact the attackers rely on anonymous Bitcoin payments to receive ransoms means they're going to be hard to track down.
The attackers have also only made around $50,000 in ransom demands so far, indicating that the vast majority of victims simply aren't paying up.
"Because of the quantity of data involved and the complexity of these kinds of enquiries we need to be clear that this is an investigation which will take time," said Owens.
"But I want to reassure the public that investigators are working round the clock to secure evidence and have begun to forensically analyse a number of infected computers," she added.
Specialist cybercrime officers from both the NCA and regional police organised crime units are speaking with victims - including those in the NHS - to "help protect victims and secure and preserve evidence".
While the initial threat of a second round of attacks appears to have died down for now, the NCA has warned organisations not to be complacent, because "that doesn't mean there won't be one".
In the meantime, the NCA has advised organisations to make sure security software is up to date, run anti-virus software, back up data and avoid unknown email attachments. ZDNet has also provided a guide on how to defend yourself against the WannaCrypt global ransomware attack
MORE WANNACRY RANSOMWARE NEWS
- WannaCrypt ransomware: Microsoft issues emergency patch for Windows XP
- Ransomware attack: The second wave is coming, so get ready now
- Ransomware attack: Hospitals still struggling in aftermath of WannaCrypt's rampage
- Ransomware: An executive guide to one of the biggest menaces on the web
- How Bitcoin helped fuel an explosion in ransomware attacks