Ransomware in disguise: Experts say Petya out to destroy not ransom

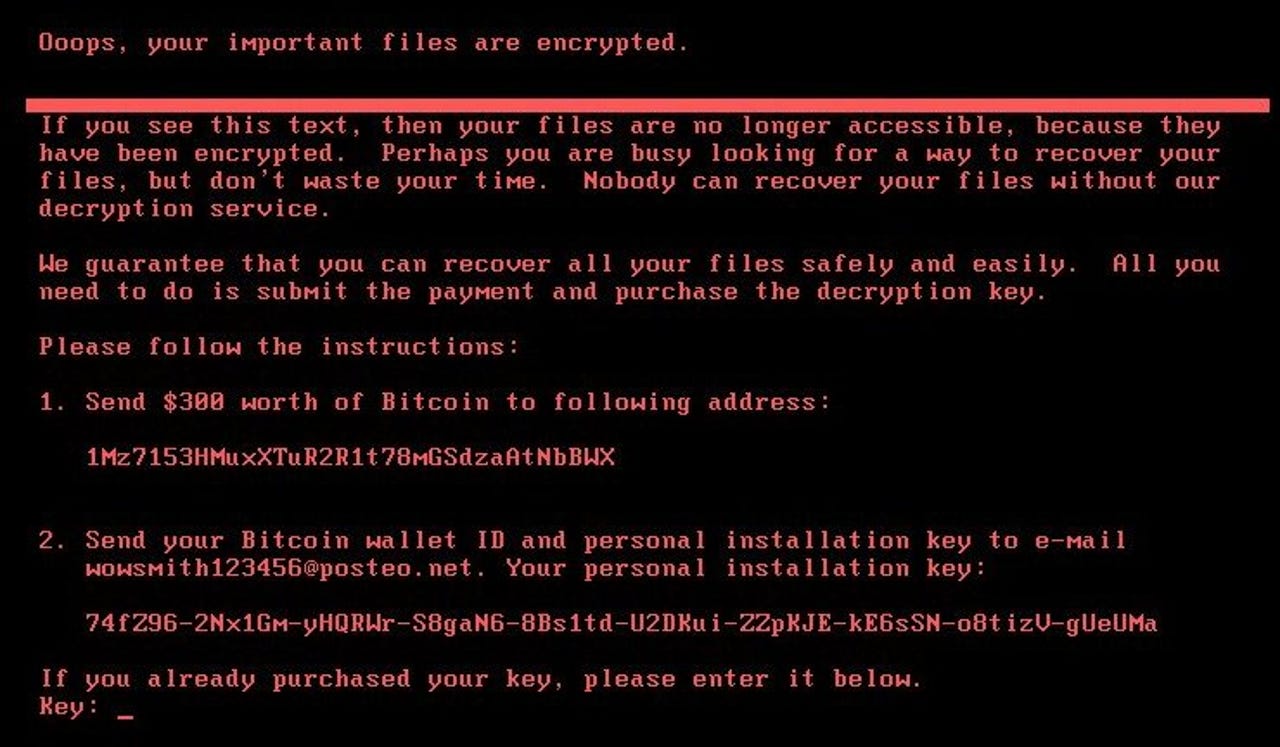
Petya ransom note
Victims of this week's Petya outbreak are being given one more reason to not pay up -- the malware is not able to restore files.
Researchers from Comae Technologies and Kaspersky Lab have independently arrived at the same conclusion that Petya is a wiper, not ransomware.
Anton Ivanov and Orkhan Mamedov of Kaspersky Lab said the malware is meant to disguise itself as ransomware, and the "installation key" the user is shown on a Petya ransom note is merely randomised data.
"That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID," the pair said.
"What does it mean? Well, first of all, this is the worst-case news for the victims - even if they pay the ransom they will not get their data back. Secondly, this reinforces the theory that the main goal of the ExPetr attack was not financially motivated, but destructive."
Infected users are shown a now defunct email address in the ransom note after it was shut down on Tuesday by email provider Posteo. At the time of writing, the bitcoin wallet tied to the malware had collected around $10,300 in ransoms.
Matt Suiche of Comae Technologies said the malware was purposely overwriting the first 25 blocks on a disk.
"We believe the ransomware was in fact a lure to control the media narrative, especially after the WannaCry incidents to attract the attention on some mysterious hacker group rather than a national state attacker like we have seen in the past in cases that involved wipers such as Shamoon," he wrote.
According to Suiche, whereas the earlier versions of Petya were able to be recovered from, in its latest guise, Petya does permanent damage.
A day after Petya outbreak began, at least 2,000 attacks have been recorded in over 64 countries.
Microsoft confirmed yesterday via its telemetry data a number of initial infections occurred via Ukraine-based tax accounting software MEDoc.
"Although this vector was speculated at length by news media and security researchers -- including Ukraine's own Cyber Police -- there was only circumstantial evidence for this vector. Microsoft now has evidence that a few active infections of the ransomware initially started from the legitimate MEDoc updater process," Microsoft said.
On Wednesday, NATO Secretary General Jens Stoltenberg said the collective defence article in the North Atlantic Treaty could be invoked in the face of a cyber attack.
We have also decided that a cyber attack can trigger Article 5 and we have also decided -- and we are in the process of establishing -- cyber as a military domain, meaning that we will have land, air, sea, and cyber as military domains," he said.