Ransomware springboards from WordPress to Joomla domains

Strains of ransomware have been detected on Joomla domains, revealing a disturbing evolution of the malware's attack vectors.
According to Brad Duncan, a security researcher at Rackspace and contributor to the Internet Storm Center, attacks based on the "admedia" campaign have shifted from the traditional target of websites supported by the WordPress content management system (CMS), and instead, have graduated to also hunt down vulnerable Joomla CMS Web domains.
Back in January this year, Securi Labs spotted "a spike in WordPress infections" impacting .js files hosted on websites. The strings revealed an admedia iframe injection which led not only to the installation of multiple backdoors, but the admedia malicious domains generated on these sites sent unwitting visitors to an exploit kit containing the TeslaCrypt ransomware.
Ransomware is a particularly virulent and potentially devastating form of malware. Strains include WinLocker, TeslaCrypt and CoinVault, but all of which have something in common -- the intention to swindle users out of their money.
Once an infection is released onto your system -- usually through phishing campaigns and malicious downloads -- the malware locks PCs, encrypts files, and demands a ransom in virtual currency in return for victims being issued a key to decrypt their content.
While cybersecurity firms are working hard to produce software which decrypts files for free, they are up against the challenge of continual updates and a family of malware which is constantly evolving and spreading.
The TeslaCrypt ransomware campaign not only is now found on vulnerable Wordpress domains, but Joomla is also at risk. Duncan said last week that since the original report earlier this year, "admedia" gate URLs to exploit kits have also used the term "megaadvertize," and the exploit kit containing the ransomware, in some cases, has been switched from Nuclear to Angler.
"In the past 24 hours, I saw a Joomla site generate an admedia gate, so this campaign is no longer limited to WordPress sites," Duncan says.
The researcher says that compromised Jooma websites are vulnerable to the same techniques as WordPress. If a website is successfully compromised, the domain will end up hosting malicious scripts injected into legitimate .js files -- used to run JavasScript code on website pages -- which then leads to the admedia gateways.
While checking out the code, Duncan found an Angler exploit kit loading page:
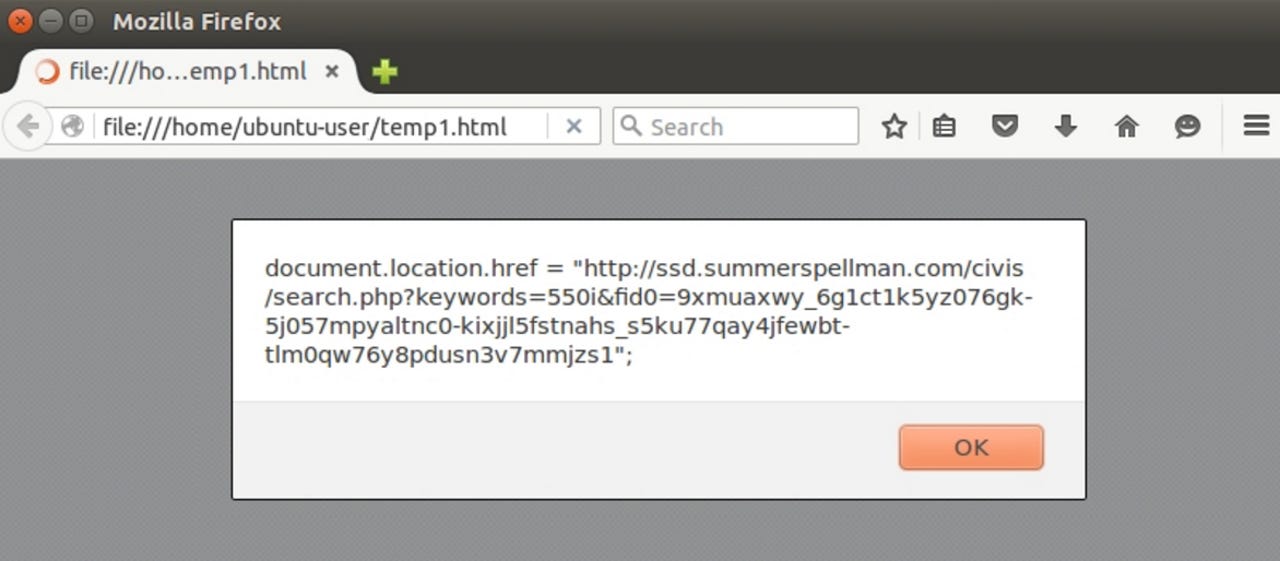
Some of the callback traffic tracked from the malware included:
Security
- 178.62.122.211 - img.belayamorda.info - admedia gate
- 185.46.11.113 - ssd.summerspellman.com - Angler EK
- 192.185.39.64 - clothdiapersexpert.com - TeslaCrypt callback traffic
This is bad news for webmasters who are running Joomla. Using legitimate Internet domains as an attack vector is a popular method due to traffic and exposure, and the only way operators can keep their domains safe is to keep website CMS systems fully patched and up-to-date, as well as stay informed of any new developments that may risk website visitors.
10 things you didn't know about the Dark Web
Read on: Top picks
- How to increase your Bitcoin mining profit by 30 percent with less effort
- SMS Android malware roots and hijacks your device - unless you are Russian
- Bug bounties: Which companies offer researchers cash?
- Shodan: The IoT search engine privacy messenger
- What happens when you leak stolen bank data to the Dark Web?