Ransomware targets victims through Visa deals

If you have a Visa credit card, be careful not to fall for a new ransomware phishing campaign which offers you benefits and rewards, researchers say.
A new and unusual phishing campaign has caught the eye of Symantec. Tthe scheme relates to credit cards -- but attempts to lure consumers to download ransomware instead of handing over their financial details.
While fraudulent credit-card based spam is nothing new, the introduction of ransomware into the mix is a new avenue cyberattackers are using to try and force people out of their hard-earned cash to keep their system files and content.
The news follows the latest high-profile infection case to hit the headlines; that of two German hospitals which became victims of ransomware which booted the organizations out of their servers and IT systems. Neither hospital has bowed to the cyberattacker's demand for payment.
According to researchers from Symantec, the new phishing campaign pretends to offer Visa rewards and benefits as bait to lure victims into downloading malicious files containing ransomware.
The emails are crafted to appear from Visa Total Rewards and include information pertaining to the credit card's reward schemes. An archived file is attached to these emails as a whitepaper which contains additional information about rewards for customers -- however, if the file is opened, the victim will see nothing more than an obfuscated JavaScript file.
If a victim opens the file, the JavaScript downloads TeslaCrypt 2.0, a well-known Trojan which was upgraded in 2014 to 2015 and is still not crackable through free encryption tools.
Older versions stored decryption keys in files and used weak encryption algorithms which gave researchers the opportunity to develop tools to remove the malware -- but, unfortunately, the latest version uses the system registry instead and there is no cracking software currently available.
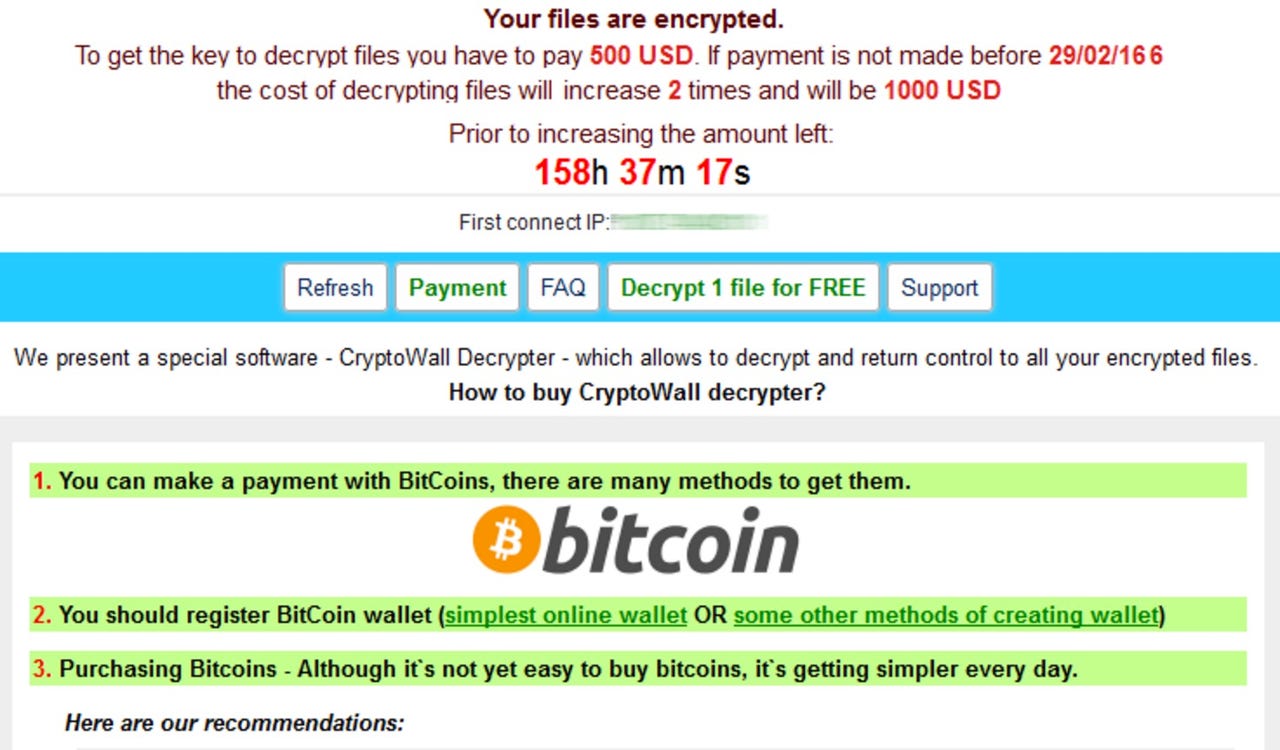
Once downloaded, the ransomware encrypts all user files and locks the system. TeslaCrypt then launches a holding screen and demands a payment of 1.2BTC -- approximately $500 -- to be paid within 160 hours if users wish to retrieve access to their files. If this does not happen and the user refuses, the fee doubles to $1000.
Security
The ransomware offers users the chance to select and decrypt a single file for free to place additional pressure on them to pay -- as well as prove the other files are out of reach if the ransom is not paid.
Your friendly neighborhood cyberattacker also provides a contact form to help victims struggling to make the payment.
Symantec says the campaign began as early as 17 February and remains ongoing. The cybersecurity firm's tracking suggests the peak may have already passed, but cyberattackers who utilize ransomware are nothing if not persistent, and so it would not a surprise if more spikes and ramped-up activity appears in the months to come.
The phishing campaign is targeting English-speaking countries, with the majority of spam being sent to the UK and the United States.
See also: New Cryptowall ransomware makes locked files even harder to recover
In order to limit the damage ransomware and other strains of malware can cause to your PC, you should backup your files on a regular basis. If you are unfortunate enough to become a victim of ransomware, the first thing to do is pick up another device and do some research -- as some security companies offer free unlocking software for some ransomware families.
If not, consult a professional to see if there is the possibility of eradicating the malware without being forced to pay the ransom.
Top gadgets and apps to protect your mobile devices
Read on: Top picks
- How to increase your Bitcoin mining profit by 30 percent with less effort
- SMS Android malware roots and hijacks your device - unless you are Russian
- Bug bounties: Which companies offer researchers cash?
- Shodan: The IoT search engine privacy messenger
- What happens when you leak stolen bank data to the Dark Web?