Repeat after me: "Reusing passwords is BAD!"

a hacker group going by the name of Gnosis compromised the Gawker Media network (made up of popular websites such as Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin, Fleshbot, and Gawker itself) and liberated not only the source code for the site, but also the entire user database consisting of about 1.3 million usernames, email addresses, and password hashes. In an ideal world, this wouldn't be a problem, but we don't live in an ideal world, but this is far from an ideal world, so it has the scope to be a pretty big deal.
"Reusing passwords is BAD!"
So, what can you do? Well, by far the best thing to do is make sure that you have a unique username and password for each and every web logon you have. That way if one is compromised, the rest are safe.
Note: It might not always be possible to have a unique username as many sites and services use your email address as the username, but I've found it useful to try to do this because you can also easily spot companies that are passing on your email address to third-parties.
"Reusing passwords is BAD!"
Once you decide that you're going to have a different password for every account, you'll quickly get to the point where you'll need a password manager to keep track of things. Not only will a password manager act as a secure repository for your passwords, but it should also make managing and creating new passwords for accounts easy. For years I went with a free, open source application called Password Safe. This worked great until I started using iOS powered iPhones and iPads more, then I needed something that was cross-platform. After a lot of testing I went with an application called SplashID on both the desktop and mobile devices. It's a great program that allows easy syncing of passwords between desktop and mobile devices.
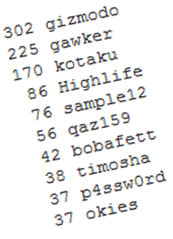
302 gizmodo 225 gawker 170 kotaku 86 Highlife 76 sample12 56 qaz159 42 bobafett 38 timosha 37 p4ssw0rd 37 okies
You might be expecting to see the password password appear high up in the top ten list. It doesn't not because people are too smart to use it, but because Gawker, like sites such as Twitter, maintains a list of banned passwords preventing people from using blindingly obvious passwords.
"Reusing passwords is BAD!"
Other stats relating to the passwords:
- The vast majority (99.23%) of the cracked passwords were alphanumeric and did not contain any special characters or symbols.
- Of the passwords that were alphanumeric, about 45% were composed of strictly lowercase alphabetic characters, 11% were strictly numeric, less than 1% were strictly uppercase alphabetic characters, and the rest were mixed alphanumeric.
- Of those unique passwords, approximately 118,000 (62%) are used by only a single user (that is, they've selected a password that no one else has). Similarly, 17,000 (9%) are passwords that are shared by only two users and 5,000 (2.5%) are shared by only three users.
"Reusing passwords is BAD!"
So, the bottom line:
- Stop reusing passwords!
- Have in place an effective password manager - don't try to remember this stuff.
- Change important passwords regularly.
- Enjoy life!
If people didn't reuse passwords, this incident would be a minor hassle for those frequenting Gawker. But since some people are hell-bent on reusing passwords, a small leak turns into a really big deal.
Makes sense? Get to it then!