Report: Patched vulnerabilities remain prime exploitation vector
Which is the most popular tactic that cybercriminals uses on their way to infect users with malicious code (malware) and generate yet another botnet?
According to a newly released report by M86 Security, that's patched vulnerabilities. Why are cybercriminals turning to the exploitation of outdated flaws in the first place? Sadly, because it works taking into consideration the average insecure 3rd party application/plugin on a sample PC. Are cybercriminals being picky? Not at all, as thanks to web malware exploitation kits such as Eleonore, Phoenix, Unique Pack, Crime Pack or Fragus, they always exploit whatever is exploitable on a targeted host.
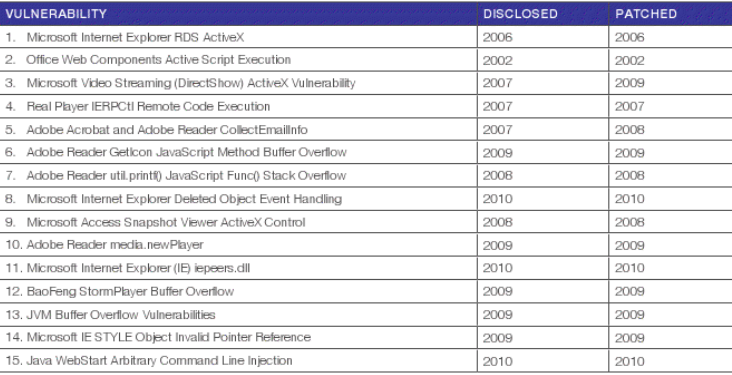
The top 10 most observed vulnerabilities served by web malware exploitation kits:
- Microsoft Internet Explorer RDS ActiveX
- Office Web Components Active Script Execution
- Microsoft Video Streaming (DirectShow) ActiveX Vulnerability
- Real Player IERPCtl Remote Code Execution
- Adobe Acrobat and Adobe Reader CollectEmailInfo
- Adobe Reader GetIcon JavaScript Method Buffer Overflow
- Adobe Reader util.printf() JavaScript Func() Stack Overflow
- Microsoft Internet Explorer Deleted Object Event Handling
- Microsoft Access Snapshot Viewer ActiveX Control
- Adobe Reader media.newPlayer
Next to the above mentioned flaws, the report is also emphasizing the fact that, in the second half of 2010, Java-based attacks rose to higher levels than anticipated.
The trend is confirmed by a second recently released report. According to Cisco's data, the exploitation of patched Java flaws has outpaced exploitation through the use of malicious PDF files, at 6.5 percent on average for 4Q10. The increase of this exploitation technique is once again contributed to the use of specific web malware exploitation kits.
See also:
- Seven myths about zero day vulnerabilities debunked
- Report: Apple had the most vulnerabilities throughout 2005-2010
- Report: ZeuS crimeware kit, malicious PDFs drive growth of cybercrime
- Report: 64% of all Microsoft vulnerabilities for 2009 mitigated by Least Privilege accounts
Users are advised to use least privilege accounts, browse the web in isolated environment, and ensure their hosts are free of outdated 3rd party software, browser plugins or OS-specific flaws.