Research: 80% of Carberp infected computers had antivirus software installed
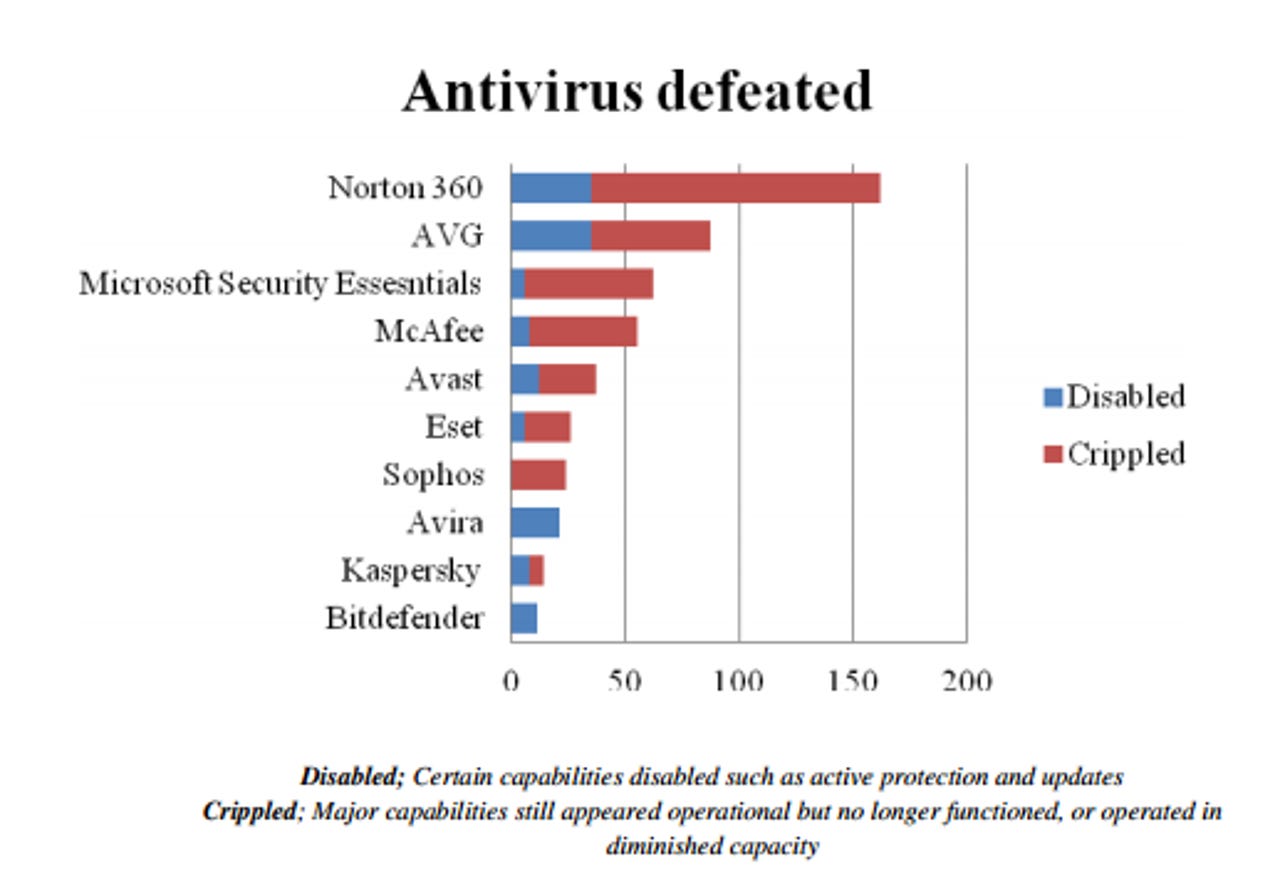
Just how useful is antivirus software in general? According to a recently published study by security researcher Jim McKenney, based on his analysis 80% of Carberp infected computers had antivirus software installed, which was either disabled, or cripped by the Carberp malware leaving antivirus users with a 'false feeling of security'.
The forensic investigation included 603 computers located in Kansas, Missouri, Oklahoma and Nebraska. What he found was pretty interesting. The majority of users relying on Symantec's Norton 360 antivirus had their protection either crippled or completely disabled. The same happened to AVG, Microsoft's Security Essentials, McAfee, Avast, ESET, Sophos, Avira, Kaspersky and BitDefender users.
Are the findings of this study a trend or a fad? Sadly, the cybercriminals' ability to bypass antivirus protection is an emerging trend within the cybercrime ecosystem, rendering popular antivirus solutions completely useless.
This isn't the first study confirming that sophisticated crimeware releases completely bypass antivirus solutions, by either disabling them, or by ensuring that their malicious releases would remain undetected even if executed on a host running an antivirus solution.
In 2009, Trusteer published an advisory that measured the in-the-wild effectiveness of antivirus solutions against the most popular crimeware, the ZeuS crimeware. Their advisory concluded that "The effectiveness of an up to date anti virus against Zeus is thus not 100%, not 90%, not even 50% - it’s just 23%."and indicated that 55% of users infected with the ZeuS crimeware were running an up-to-date antivirus solution.
Prevention is always better than the cure. Ensure that you're always running and up-to-date third-party software and browser plugins as on the majority of occasions cybercriminals will attempt to exploit outdated and already patched vulnerabilities, next to coming up with creative ways to socially engineer you to execute a malicious executable.
Find out more about Dancho Danchev at his LinkedIn profile.