Researcher demos SMS-based smartphone botnet
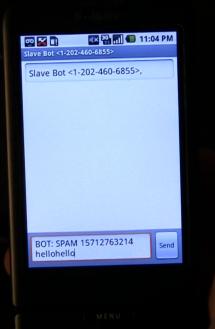
"A botnet control scenario is presented in which smartphone bots receive instructions through sms that are processed by a proxy between the GSM modem and the application layer, making the botnet messages transparent to the user. An Android version of the bot will be shown in action, and proof of concept code will be released for multiple platforms."
Upon sending a simple SMS message to the already infected smartphones, the response in terms of the actions executed can be tailored to the needs of a malicious attacker looking to create a mobile phone based botnet for literally any kind of malicious purpose. (Here's a video of the demonstration).
Last week, researchers from Indiana University and the City University of Hong Kong released another Android based proof of concept malware, this time attempting to "hear" credit card numbers. The Soundminer, a context-aware piece of malware, is the very latest indication that the academic community wants to stay a step ahead of cybercriminals themselves.
Related posts:
- Researchers use smudge attack, identify Android passcodes 68 percent of the time
- Man-in-the-middle attacks demoed on 4 smartphones
What's the future of mobile malware and smartphone botnets? Sadly, the future looks bright. From social engineering driven malware infections on Android devices, to flawed from a security perspective, efficiency-driven models, malicious attackers remain perfectly positioned to capitalize on these exploitation vectors, unless the average and enterprise users become aware of them.